Chapter Outline:
8.0 Introduction
8.1 VPNs
8.2 IPsec VPN Components and Operations
8.3 Implementing Site-to-Site IPsec VPNs with CLI
8.4 Summary
Section 8.1: VPNs
Upon completion of this section, you should be able to:
- Describe VPNs and their benefits.
- Compare site-to-site and remote-access VPNs.
Topic 8.1.1: VPN Overview
Introducing VPNs
VPN Benefits:
- Cost Savings
- Security
- Scalability
- Compatibility
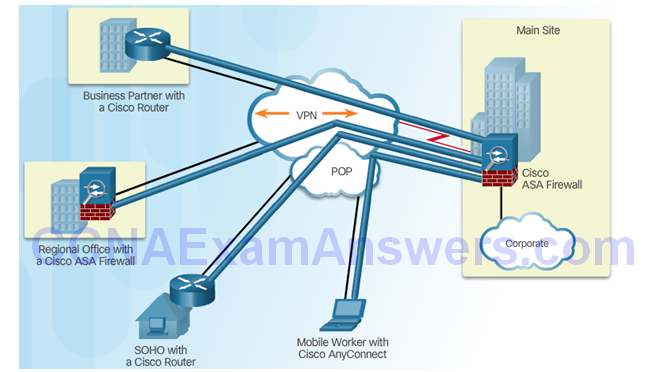
Layer 3 IPsec VPNs
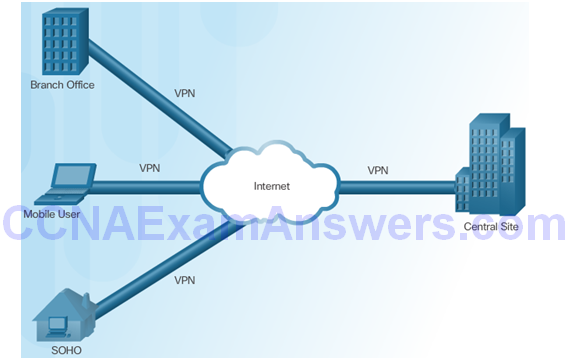
Topic 8.1.2: VPN Technologies
Two Types of VPNs
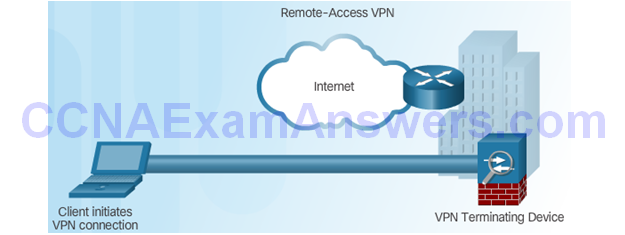
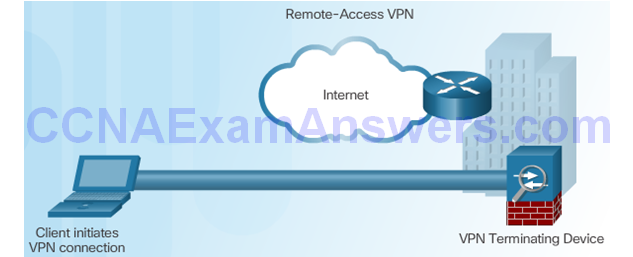
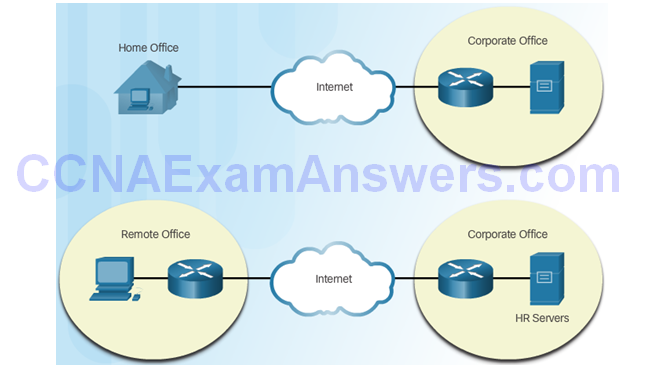
Remote-Access VPN
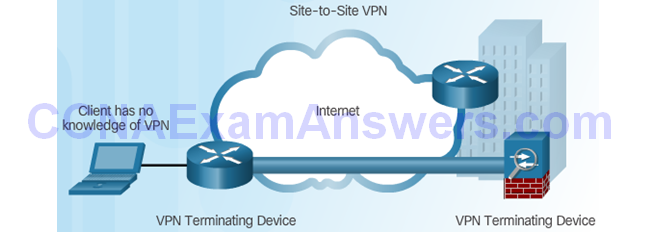
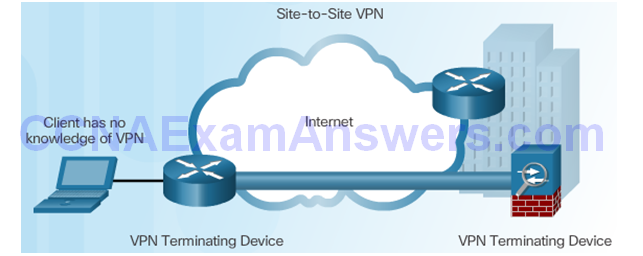
Site-to-Site VPN Access
Components of Remote-Access VPNs
Components of Site-to-Site VPNs
Section 8.2: IPsec VPN Components and Operation
Topic 8.2.1: Introducing IPsec
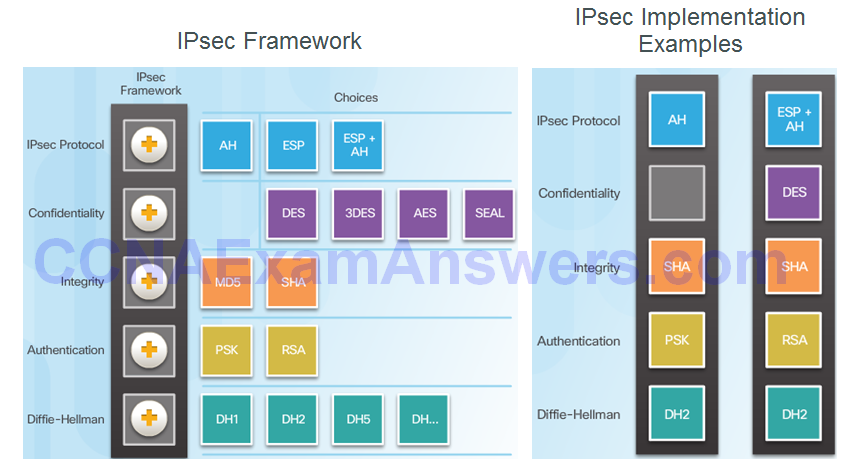
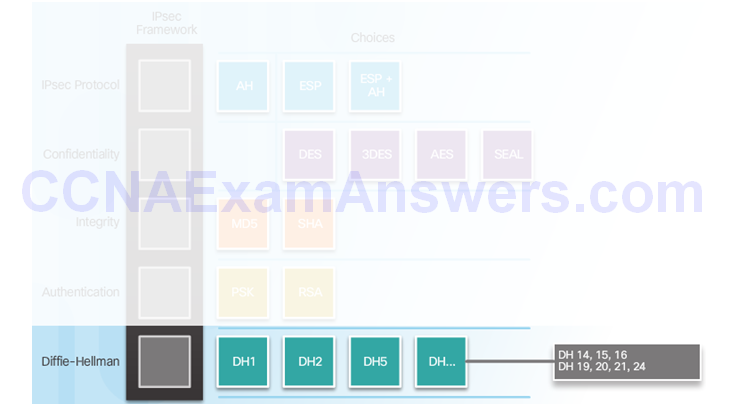
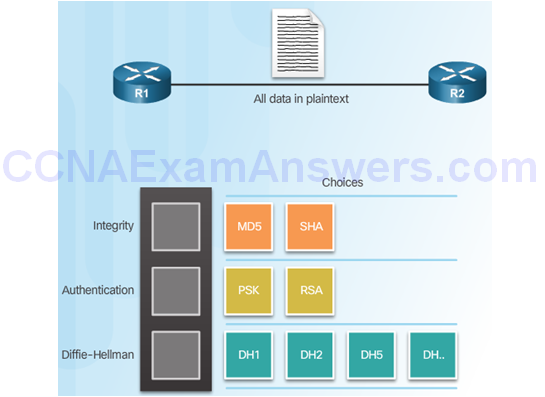
IPsec Technologies
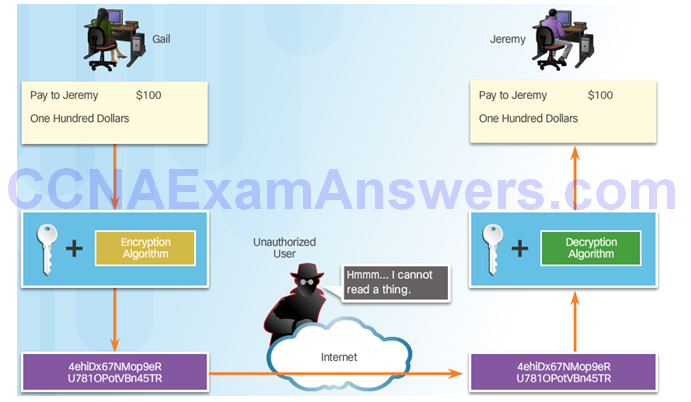
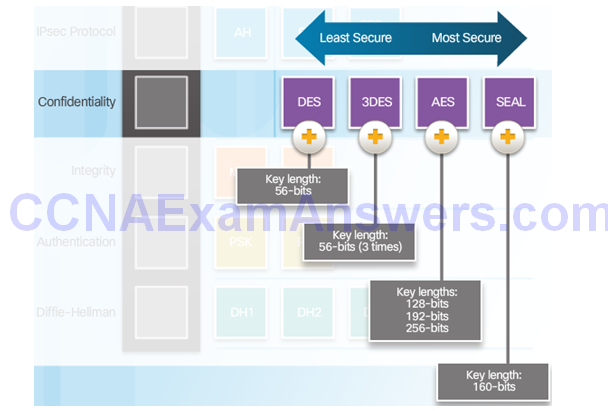
Confidentiality
Confidentiality with Encryption:
Encryption Algorithms:
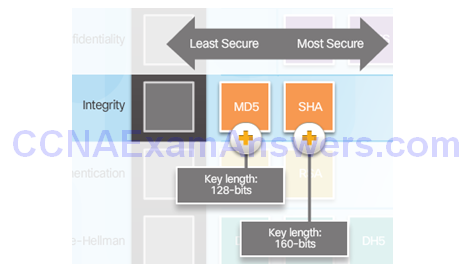
Integrity
Hash Algorithms
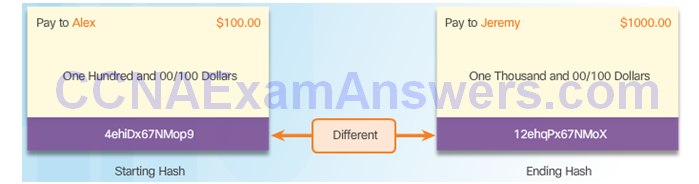
Security of Hash Algorithms
Authentication
Peer Authentication Methods
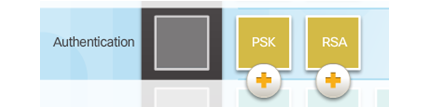
PSK
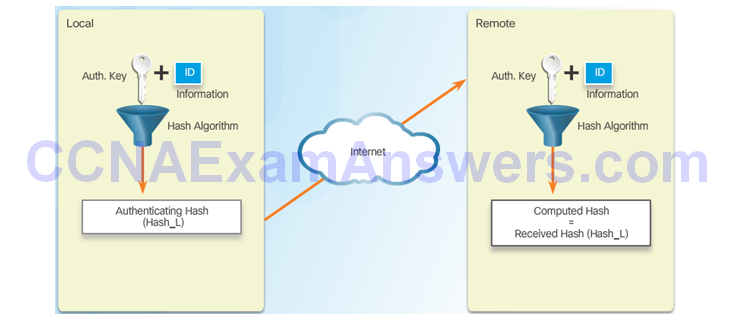
RSA
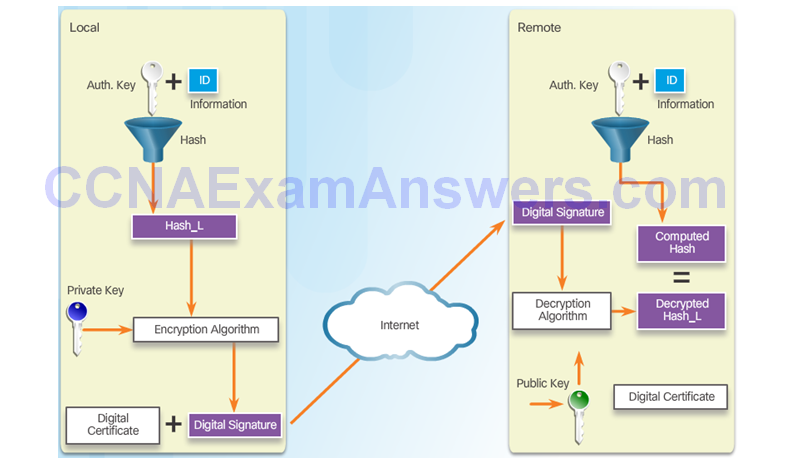
Secure Key Exchange
Diffie-Hellman Key Exchange
Topic 8.2.2: IPsec Protocols
IPsec Protocol Overview
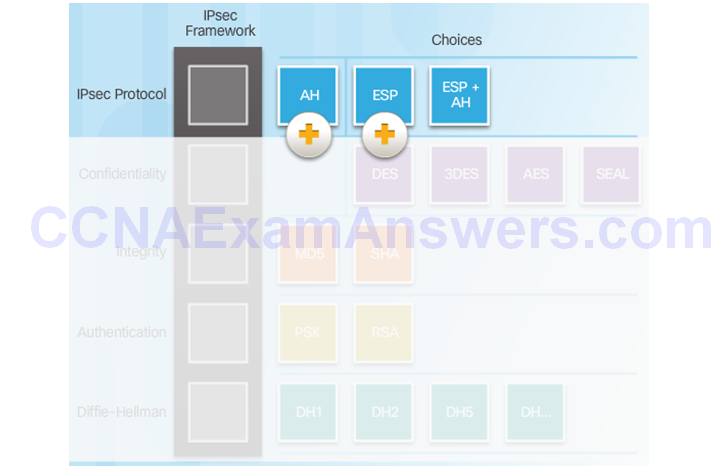
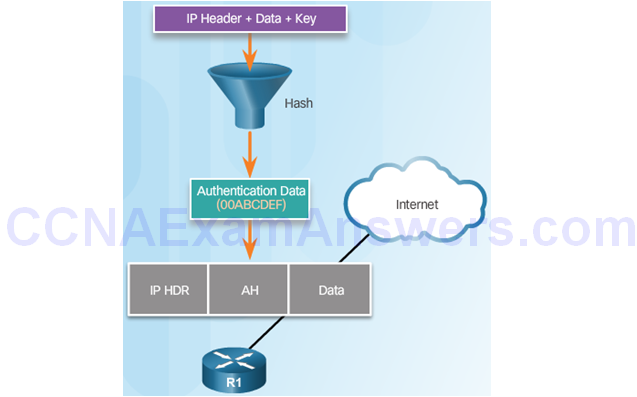
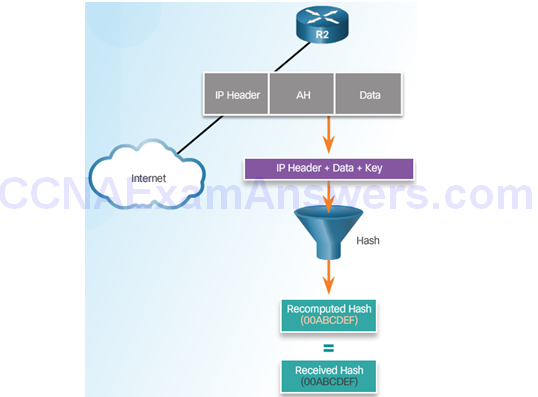
Authentication Header
AH Protocols
Router Creates Hash and Transmits to Peer
Peer Router Compares Recomputed Hash to Received Hash
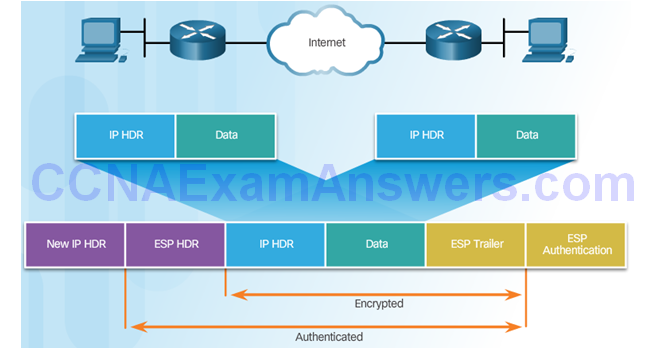
ESP
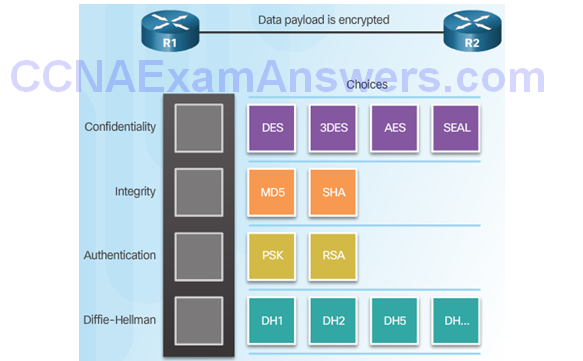
ESP Encrypts and Authenticates
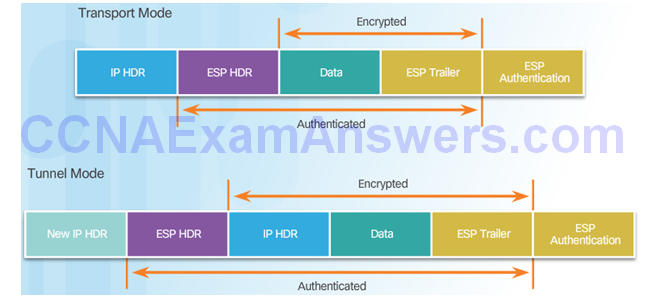
Transport and Tunnel Modes
Apply ESP and AH in Two Modes
ESP Tunnel Mode
Topic 8.2.3: Internet Key Exchange
The IKE Protocol
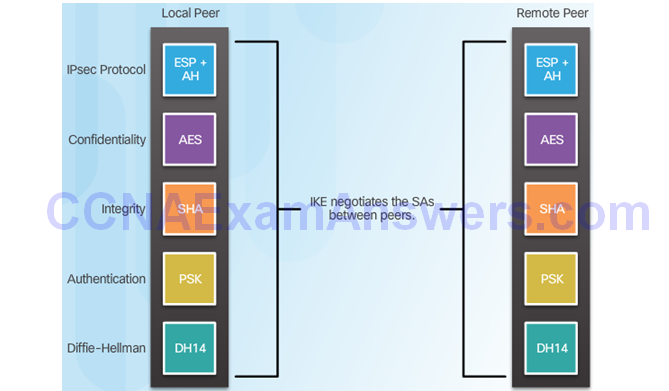
Phase 1 and 2 Key Negotiation
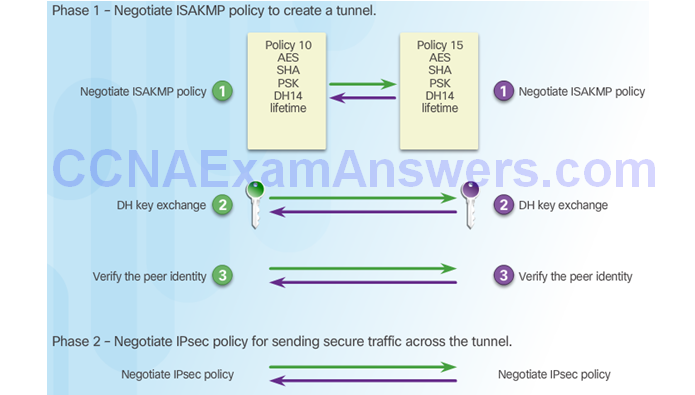
Phase 2: Negotiating SAs

Section 8.3: Implementing Site-to-Site IPsec VPNs with CLI
Upon completion of this section, you should be able to:
- Describe IPsec negotiation and the five steps of IPsec configuration.
- Configure the ISAKMP policy.
- Configure the IPsec policy.
- Configure and apply a crypto map.
- Verify the IPsec VPN.
Topic 8.3.1: Configuring a Site-to-Site IPsec VPN
IPsec Negotiation
IPsec VPN Negotiation: Step 1 – Host A sends interesting traffic to Host B.
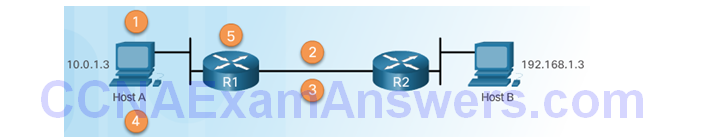
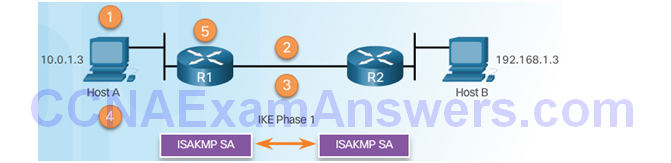
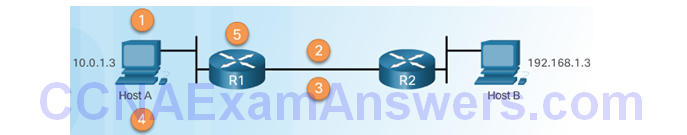
IPsec VPN Negotiation: Step 2 – R1 and R2 negotiate an IKE Phase 1 session.
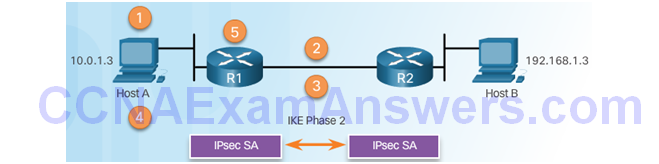
IPsec VPN Negotiation: Step 3 – R1 and R2 negotiate an IKE Phase 2 session.
IPsec VPN Negotiation: Step 4 – Information is exchanged via IPsec tunnel.
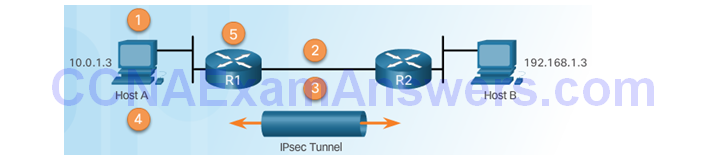
IPsec VPN Negotiation: Step 5 – The IPsec tunnel is terminated.
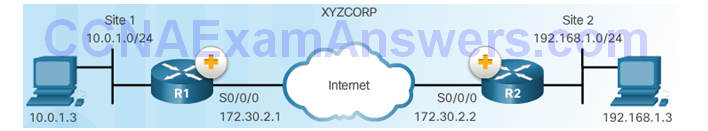
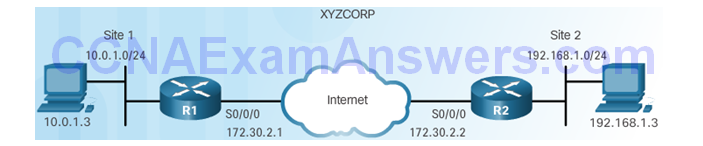
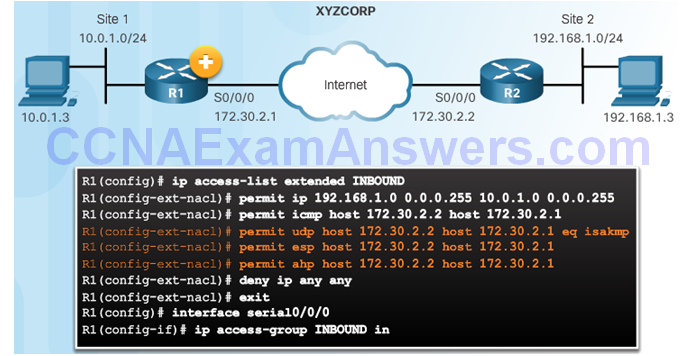
Site-to-Site IPsec VPN Topology
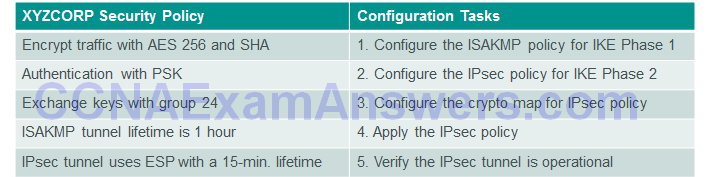
IPsec VPN Configuration Tasks
Existing ACL Configurations
ACL Syntax for IPsec Traffic
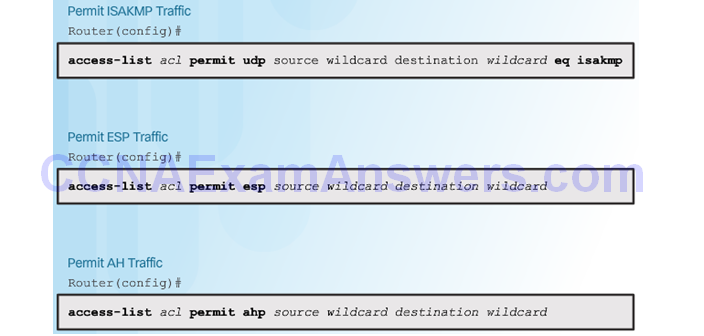
Permitting Traffic for IPsec Negotiations
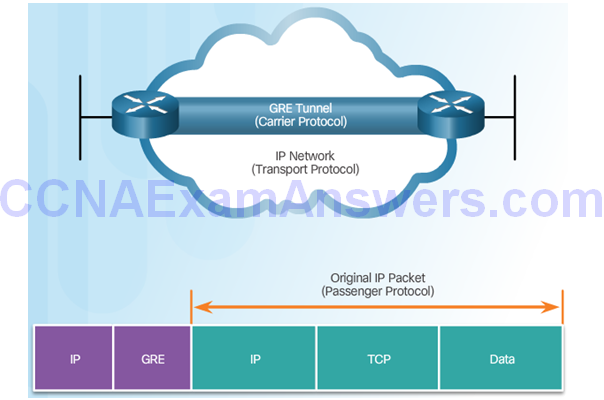
Introduction to GRE Tunnels
Topic 8.3.2: ISAKMP Policy
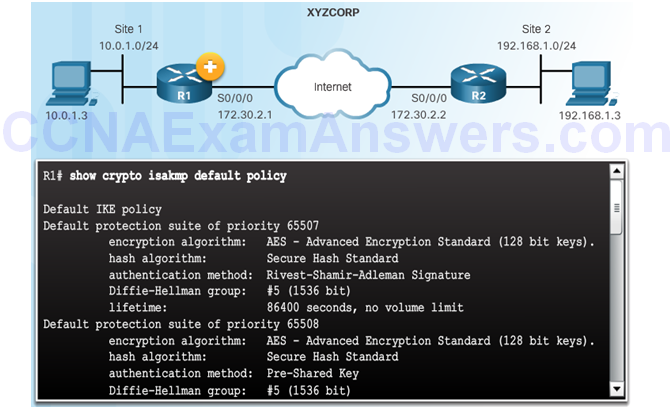
The Default ISAKMP Policies
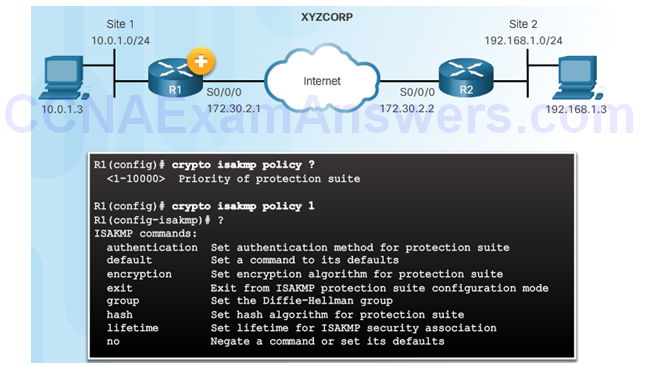
Syntax to Configure a New ISAKMP Policy
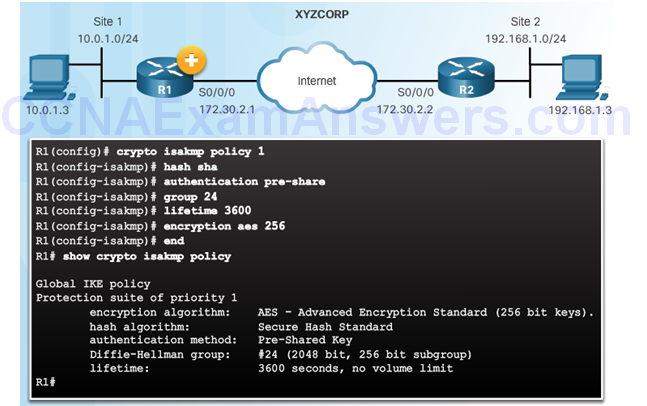
XYZCORP ISAKMP Policy Configuration
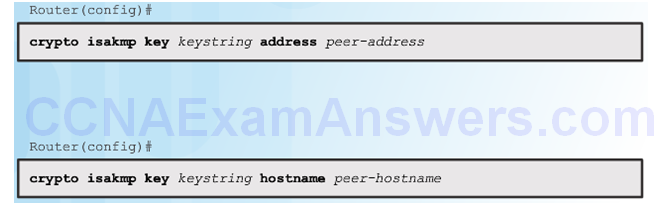
Configuring a Pre-Shared Key
The crypto isakmp key Command
Pre-Shared Key Configuration
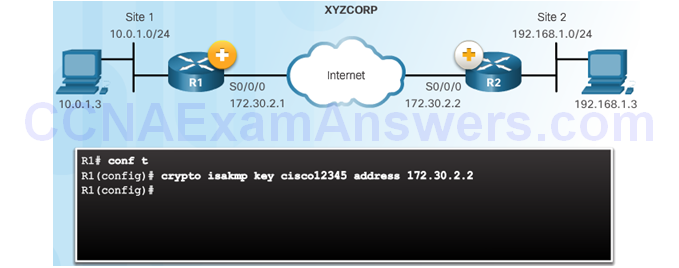
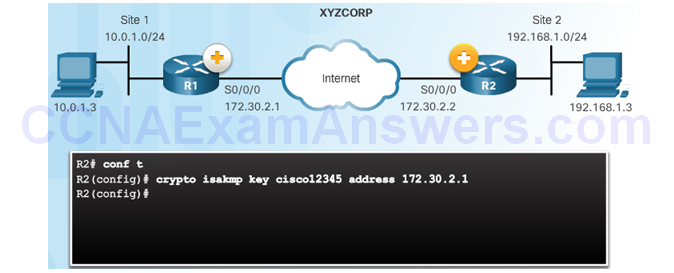
Topic 8.3.3: IPsec Policy
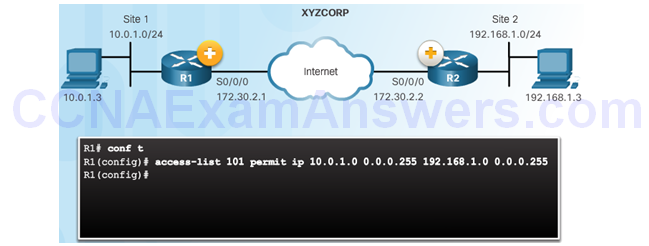
Define Interesting Traffic
The IKE Phase 1 Tunnel Does Not Exist Yet
Configure an ACL to Define Interesting Traffic
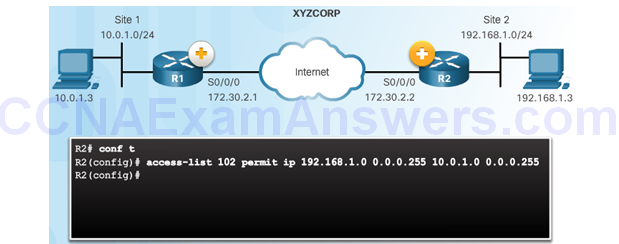
Configure IPsec Transform Set
The crypto ipsec transform-set Command
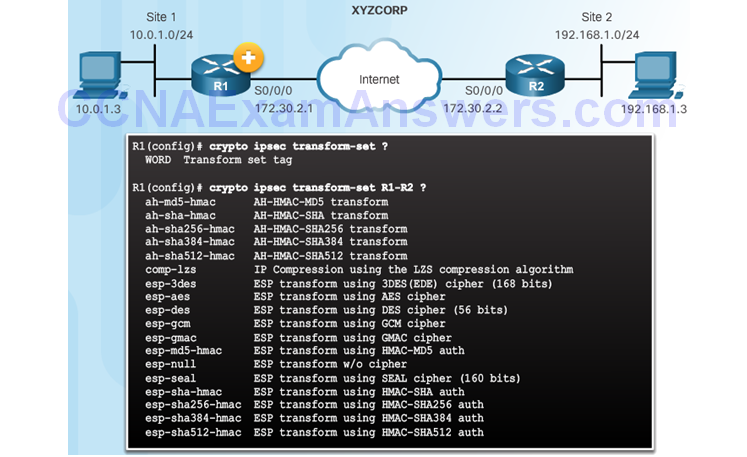
The crypto ipsec transform-set Command
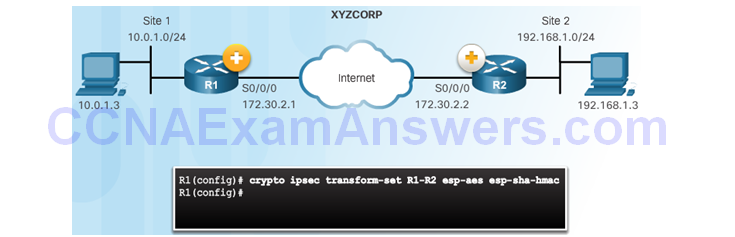
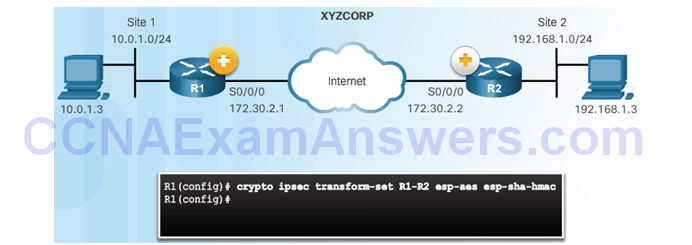
Topic 8.3.4: Crypto Map
Syntax to Configure a Crypto Map
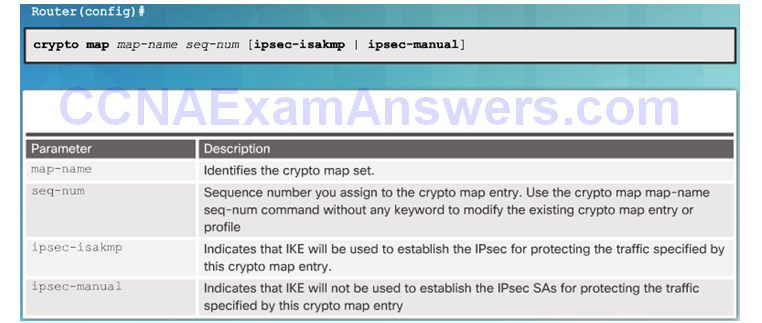
Crypto Map Configuration Commands
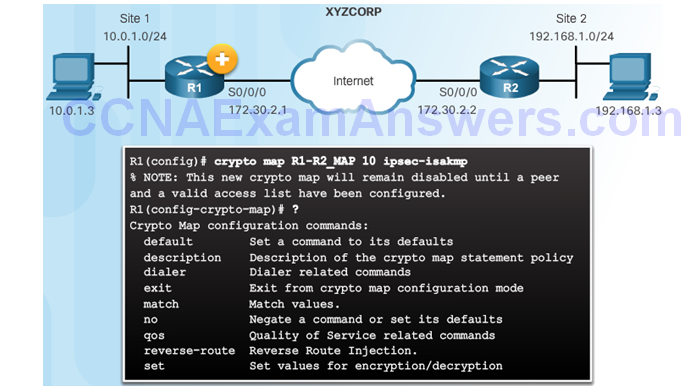
XYZCORP Crypto Map Configuration
Crypto Map Configuration:
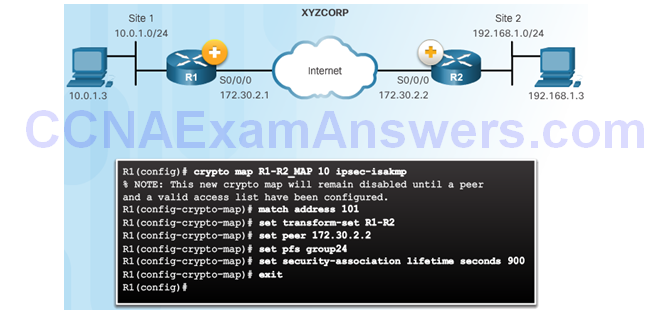
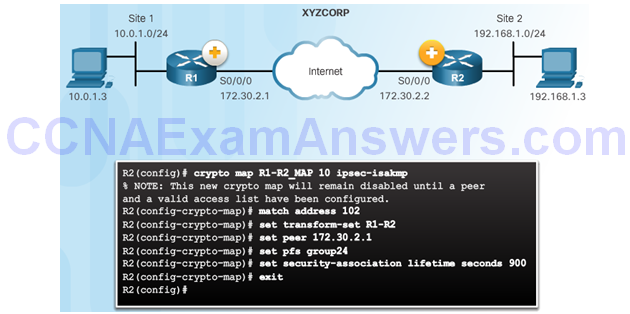
Crypto Map Configuration:
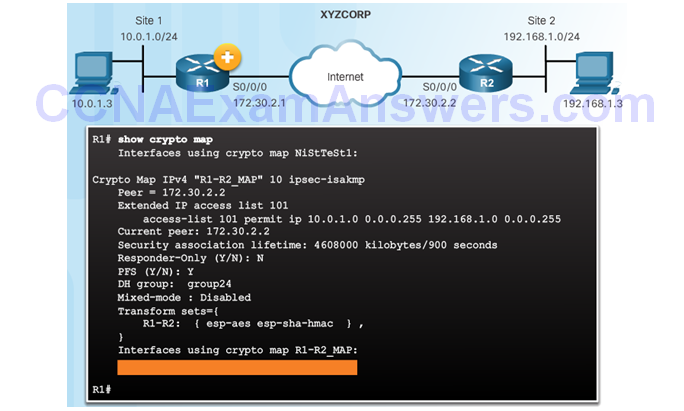
Apply the Crypto Map
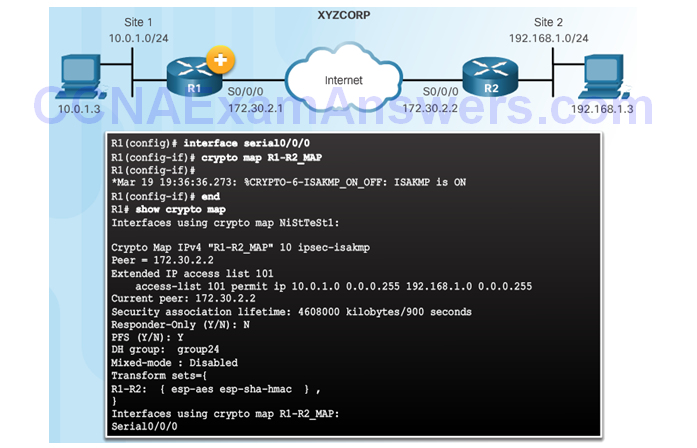
Topic 8.3.5: IPsec VPN
Send Interesting Traffic
Use Extended Ping to Send Interesting Traffic
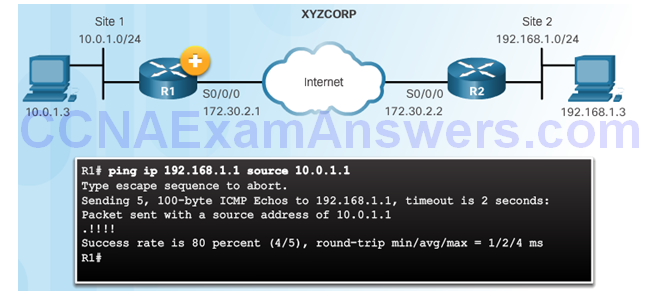
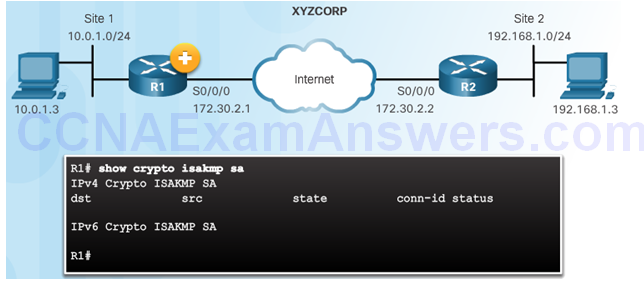
Verify ISAKMP and IPsec Tunnels
Verify the ISAKMP Tunnel is Established
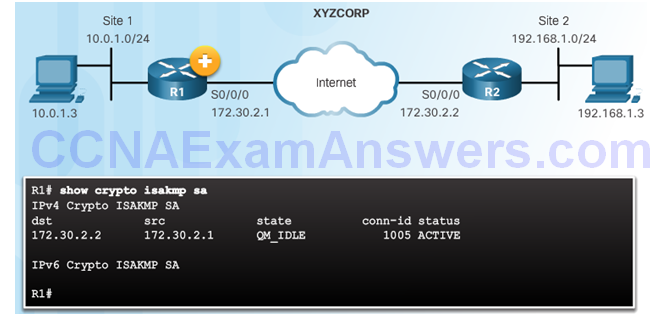
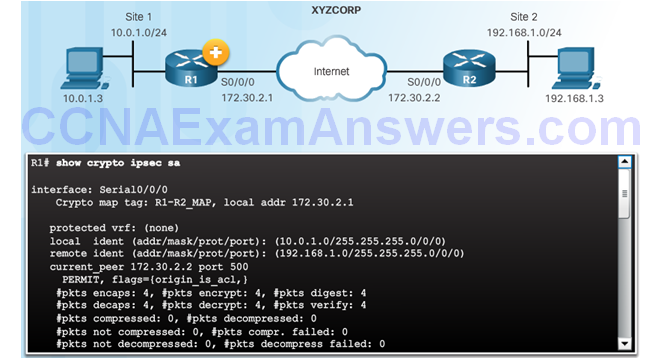
Verify the IPsec Tunnel is Established
Section 8.4: Summary
Chapter Objectives:
- Explain the purpose of VPNs.
- Explain how IPsec VPNs operate.
- Configure a site-to-site IPsec VPN, with pre-shared key authentication,
using the CLI.
Download Slide PowerPoint (pptx):
[sociallocker id=”2293″][wpdm_package id=’3231′][/sociallocker]
