Chapter Outline:
11.0 Introduction
11.1 Network Security Testing
11.2 Developing a Comprehensive Security Policy
11.3 Summary
Section 11.1: Network Security Testing
Upon completion of this section, you should be able to:
- Describe the techniques used in network security testing.
- Describe the tools used in network security testing.
Topic 11.1.1: Network Security Testing Techniques
Operations Security

Testing and Evaluating Network Security

Types of Network Tests
Operational Status of the Network:
- Penetration testing
- Network scanning
- Vulnerability scanning
- Password cracking
- Log review
- Integrity checks
- Virus detection

Applying Network Test Results

Topic 11.1.2: Network Security Testing Tools

Network Testing Tools
- Nmap/Zenmap
- SuperScan
- SIEM
- GFI LANguard
- Tripwire
- Nessus
- L0phtCrack
- Metasploit
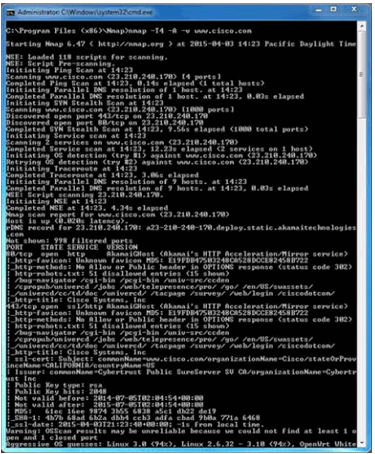
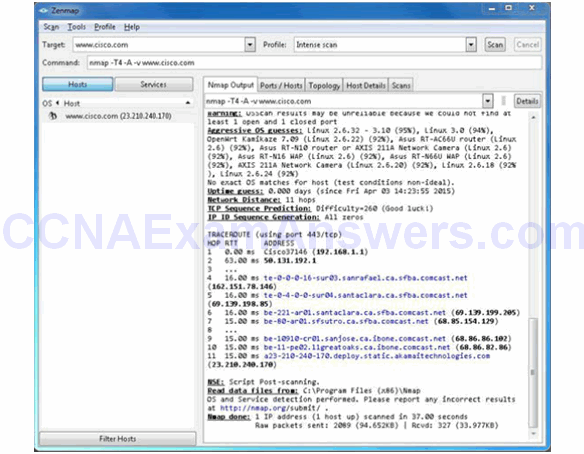
Nmap and Zenmap
Sample Nmap Screenshot
Sample Zenmap Screenshot
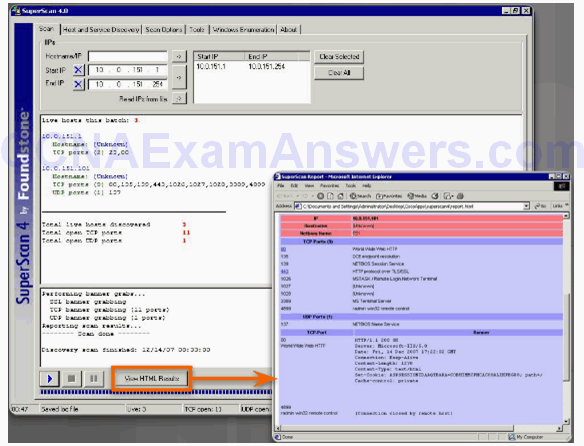
SuperScan
SIEM
Essential functions:
- Forensic Analysis
- Correlation
- Aggregation
- Retention
Section 11.2: Developing a Comprehensive Security Policy
Topic 11.2.1: Security Policy Overview
Secure Network Life Cycle
Determine what the assets of an organization are by asking:
- What does the organization have that others want?
- What processes, data, or information systems are critical to the organization?
- What would stop the organization from doing business or fulfilling its mission?

Security Policy

Security Policy Audience
Audience Determines Security Policy Content

Topic 11.2.2: Structure of a Security Policy
Security Policy Hierarchy
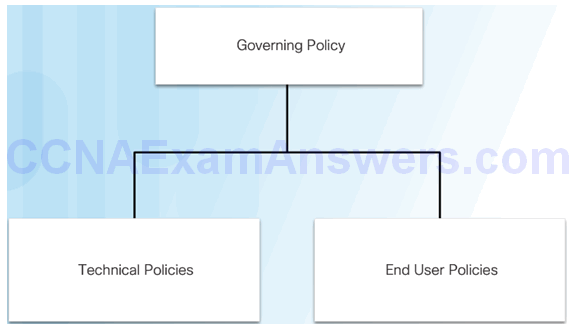
Governing Policy
A governing policy includes:
- Statement of the issue that the policy addresses
- How the policy applies in the environment
- Roles and responsibilities of those affected by the policy
- Actions, activities, and processes that are allowed (and not allowed)
- Consequences of noncompliance

Technical Policies

Technical components:
- General policies
- Telephony policy
- Email and communication policy
- Remote access policy
- Network policy
- Application policy
End User Polices
Customize End-User Policies for Groups

Topic 11.2.3: Standards, Guidelines, and Procedures
Security Policy Documents

Standards Documents

Guideline Documents
NIST Information Technology Portal
NSA Website

Common Criteria Website
Procedure Documents

Topic 11.2.4: Roles and Responsibilities
Organizational Reporting Structure

Common Executive Titles
- Chief Executive Officer (CEO)
- Chief Technology Officer (CTO)
- Chief Information Officer (CIO)
- Chief Security Officer (CSO)
- Chief Information Security Officer (CISO)

Topic 11.2.5: Security Awareness and Training
Security Awareness Program
Primary components:
- Awareness campaigns
- Training and education

Topic 11.2.6: Responding to a Security Breach
Motive, Opportunity, and Means

Collecting Data
Section 11.3: Summary
Chapter Objectives:
- Explain the various techniques and tools used for network security testing.
- Explain how to develop a comprehensive security policy.
Download Slide PowerPoint (pptx):
[sociallocker id=”2293″][wpdm_package id=’3550′][/sociallocker]
