Chapter Outline:
5.0 Introduction
5.1 IPS Technologies
5.2 IPS Signatures
5.3 Implement IPS
5.4 Summary
Section 5.1: IPS Technologies
Upon completion of this section, you should be able to:
- Explain zero-day attacks.
- Understand how to monitor, detect and stop attacks.
- Describe the advantages and disadvantages of IDS and IPS.
Topic 5.1.1: IDS and IPS Characteristics
Zero-Day Attacks
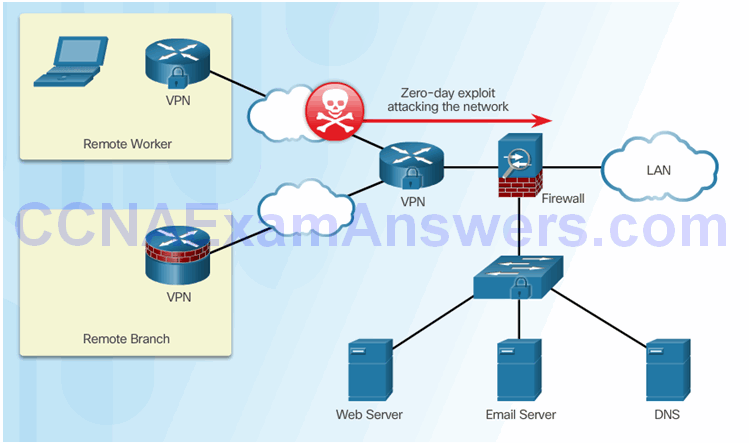
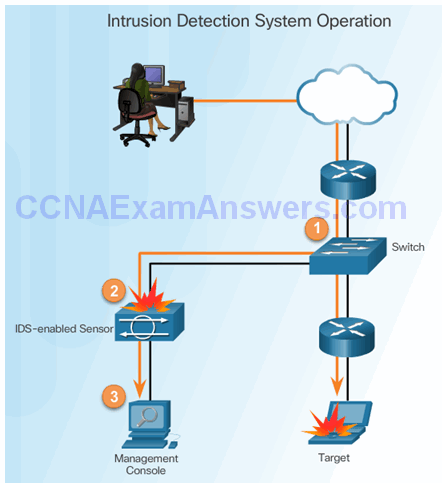
Monitor for Attacks
Advantages of an IDS:
- Works passively
- Requires traffic to be mirrored in order to reach it
- Network traffic does not pass through the IDS unless it is mirrored
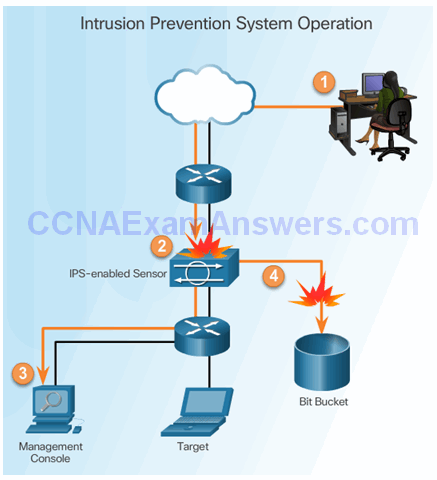
Detect and Stop Attacks
IPS:
- Implemented in an inline mode
- Monitors Layer 3 and Layer 4 traffic
- Can stop single packet attacks from reaching target
- Responds immediately, not allowing any malicious traffic to pass
Similarities Between IDS and IPS
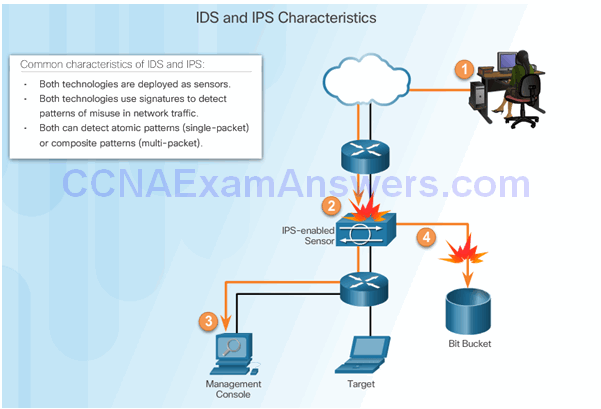
Advantages and Disadvantages of IDS and IPS
- Advantages IDS:
- No impact on network
- No network impact if there is a sensor failure
- No network impact if there is a sensor overload
- Advantages IPS:
- Stops trigger packets
- Can use stream normalization techniques
- Disadvantages IDS:
- Response action cannot stop trigger
- Correct tuning required for response actions
- More vulnerable to network security evasion techniques
- Disadvantages IPS:
- Sensor issues might affect network traffic
- Sensor overloading impacts the network
- Some impact on network
Topic 5.1.2: Network-Based IPS Implementations
Host-Based and Network-Based IPS
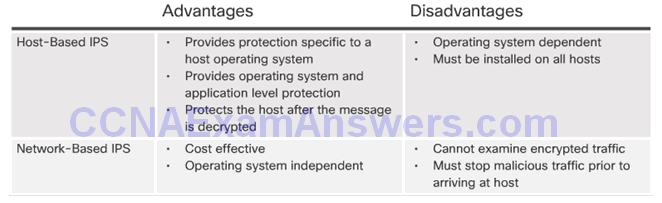
Network-Based IPS Sensors
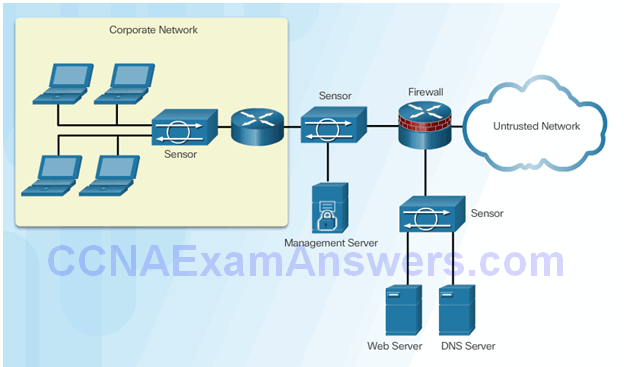
Cisco’s Modular and Appliance-Based IPS Solutions
Cisco IPS AIM and Network Module Enhanced (IPS NME)
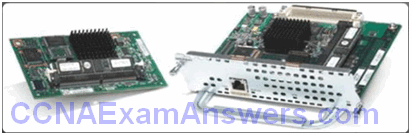
Cisco ASA AIP-SSM

Cisco IPS 4300 Series Sensors

Cisco Catalyst 6500 Series IDSM-2
Choose an IPS Solution
Factors affecting the IPS sensor selection and deployment:
- Amount of network traffic
- Network topology
- Security budget
- Available security staff to manage IPS
IPS Advantages and Disadvantages

Modes of Deployment
Promiscuous Mode
Inline Mode

Topic 5.1.3: Cisco Switched Port Analyzer
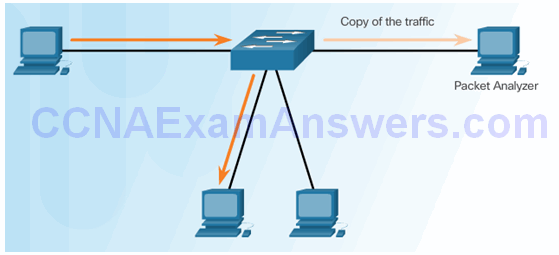
Port Mirroring
Traffic Sniffing Using a Hub
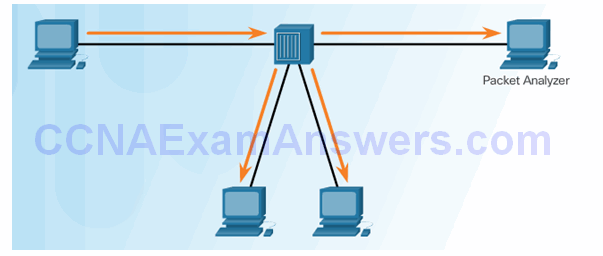
Traffic Sniffing Using a Switch
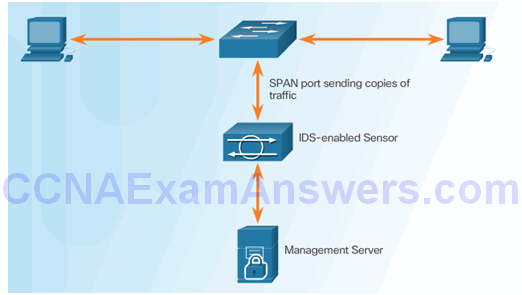
Cisco SPAN
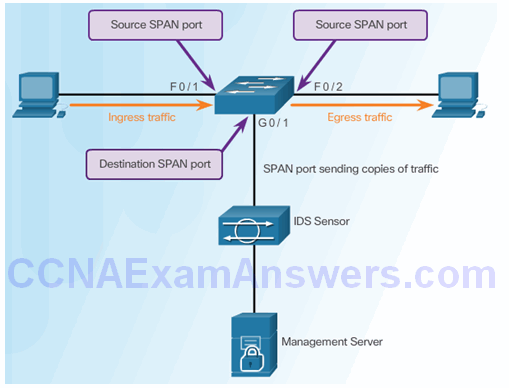
Configuring Cisco SPAN Using Intrusion Detection
- Cisco SPAN Commands:
- Monitor session command – used to associate a source port and a destination port with a SPAN session.
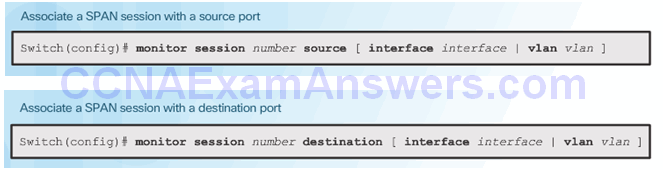
- Show monitor command – used to verify the SPAN session.
Section 5.2: IPS Signatures
Upon completion of the section, you should be able to:
- Understand IPS signature characteristics
- Explain IPS signature alarms
- Manage and monitor IPS
- Understand the global correlation of Cisco IPS devices
Topic 5.2.1: IPS Signature Characteristics
Signature Attributes
- A signature is a set of rules that an IDS and an IPS use to detect typical intrusion activity.
- Signatures have three distinct attributes:
- Type
- Trigger (alarm)
- Action
Signature Types
Signatures are categorized as either:
- Atomic – this simplest type of signature consists of a single packet, activity, or event that is examined to determine if it matches a configured signature. If yes, an alarm is triggered and a signature action is performed.
- Composite – this type of signature identifies a sequence of operations distributed across multiple hosts over an arbitrary period of time.
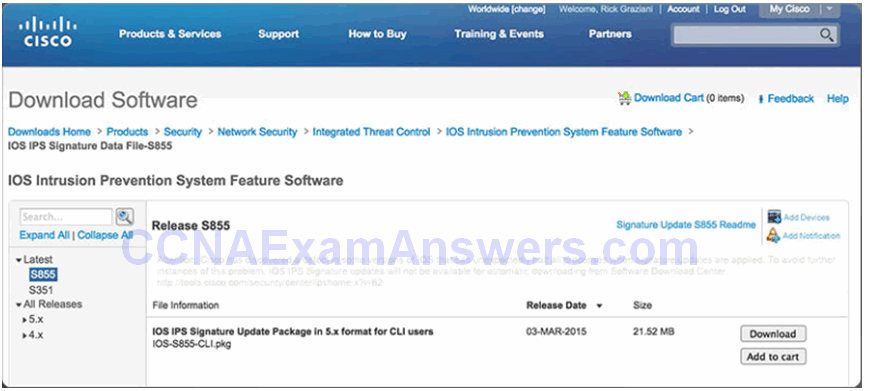
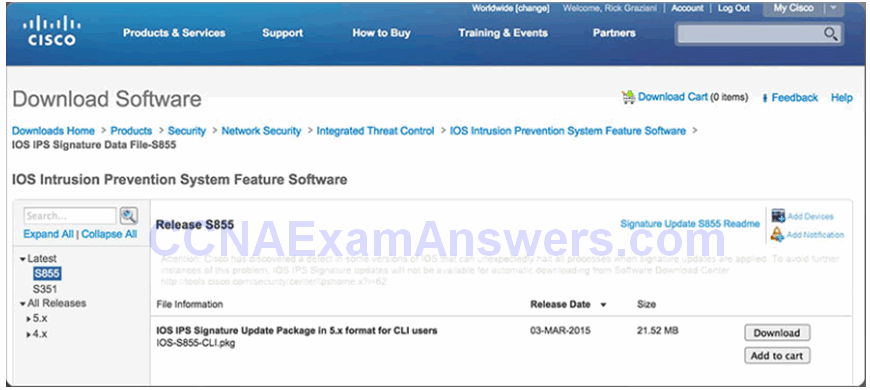
Signature File
- As new threats are identified, new signatures must be created and uploaded to an IPS.
- A signature file contains a package of network signatures.
Signature Micro-Engines
Cisco IOS defines five micro-engines:
- Atomic – Signatures that examine simple packets.
- Service – Signatures that examine the many services that are attacked.
- String – Signatures that use regular expression-based patterns to detect intrusions.
- Multi-string – Supports flexible pattern matching and Trend Labs signatures.
- Other – Internal engine that handles miscellaneous signatures.
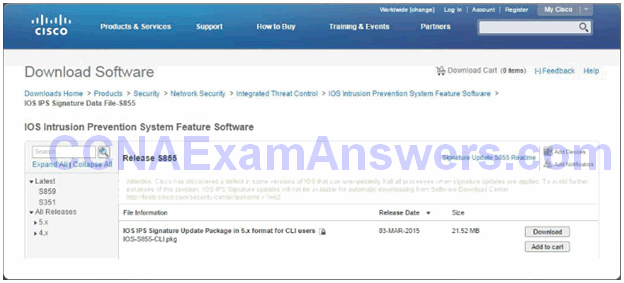
Download a Signature File
Topic 5.2.2: IPS Signature Alarms
Signature Alarm
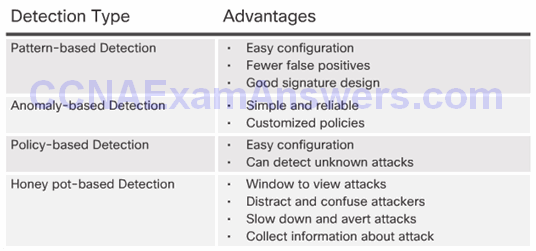
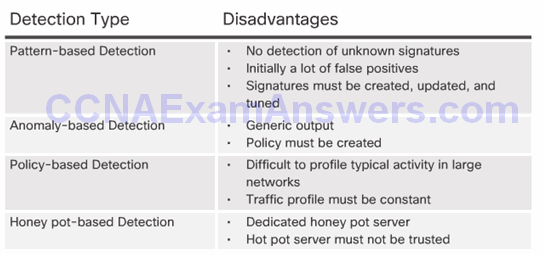
Pattern-Based Detection
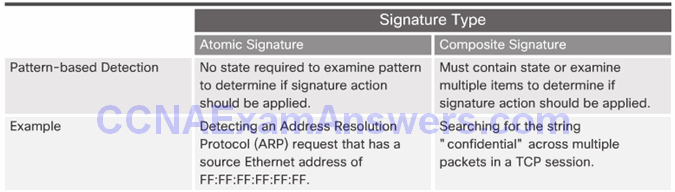
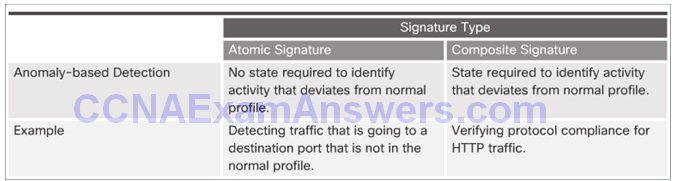
Anomaly-Based Detection
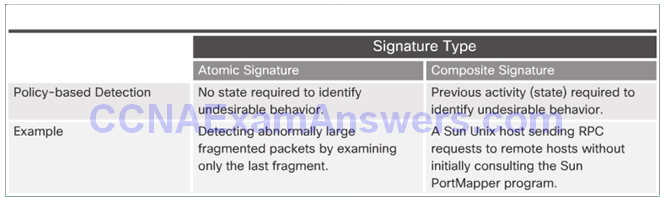
Policy-Based and Honey Pot-Based Detection
Benefits of the Cisco IOS IPS Solution
Benefits:
- It uses underlying routing infrastructure to provide an additional layer of security.
- It is inline and is supported on a broad range of routing platforms.
- It provides threat protection at all entry points to the network when used in combination with Cisco IDS, Cisco IOS Firewall, VPN, and NAC solutions
- The size of the signature database used by the devices can be adapted to the amount of available memory in the router.

Alarm Triggering Mechanisms
Understanding Alarm Types:
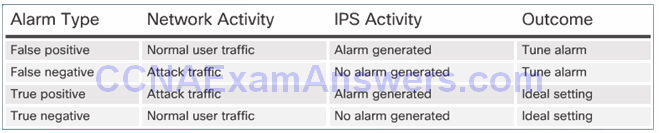
Topic 5.2.3: IPS Signature Actions
Signature Actions
Summary of Action Categories:
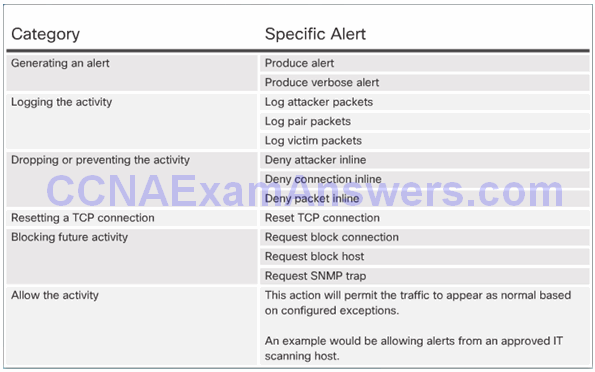
Manage Generated Alerts
Generating an Alert:
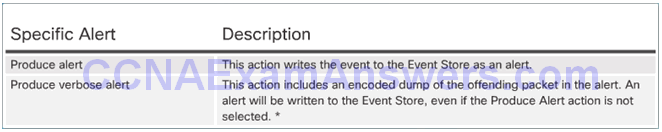
Log Activities for Later Analysis
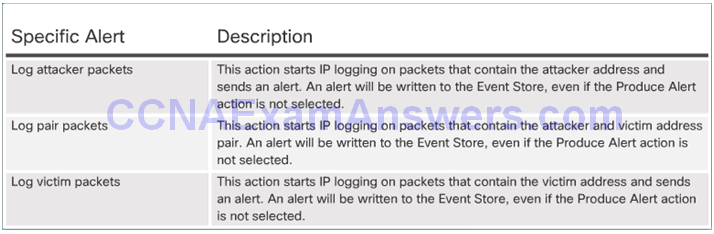
Deny the Activity
Dropping or Preventing the Activity:
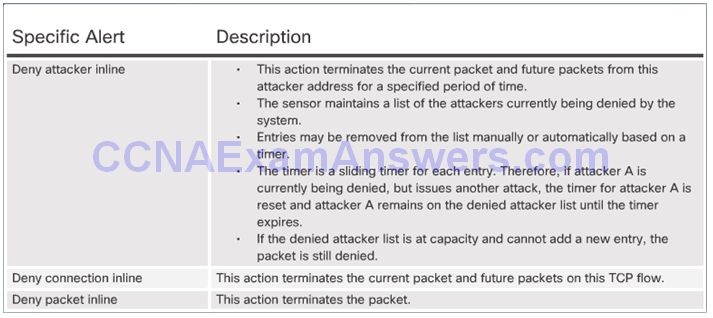
Reset, Block, and Allow Traffic
Resetting the Connection and Blocking the Activity:
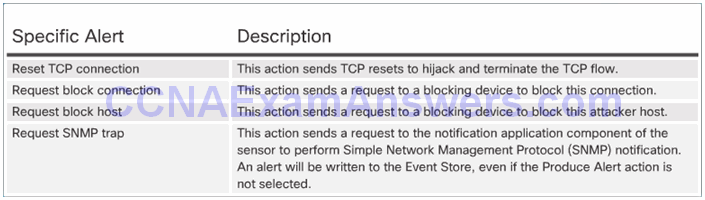
Topic 5.2.4: Manage and Monitor IPS
Monitor Activity
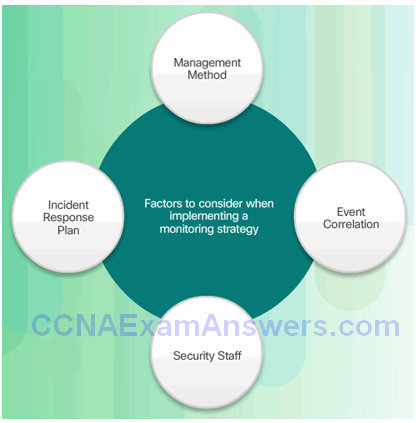
IPS Planning and Monitoring Considerations:
- Management method
- Event correlation
- Security staff
- Incident response plan
Monitoring Considerations
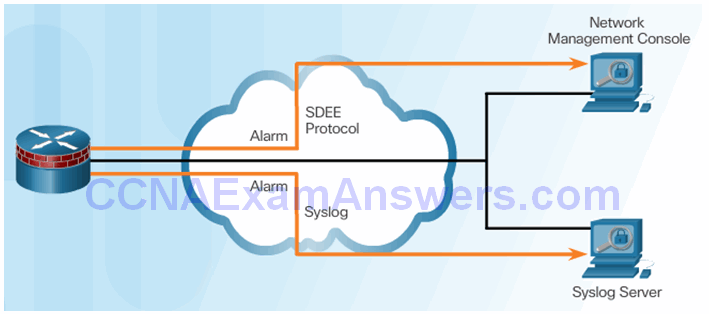
Secure Device Event Exchange
IPS Configuration Best Practices
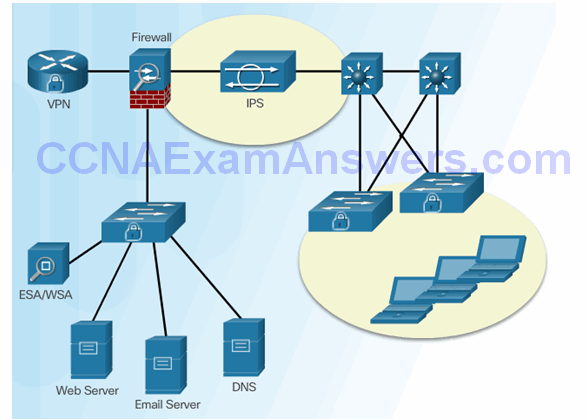
Topic 5.2.5: IPS Global Correlation
Cisco Global Correlation
Goals of global correlation:
- Dealing intelligently with alerts to improve effectiveness
- Improving protection against known malicious sites
- Sharing telemetry data with the SensorBase Network to improve visibility of alerts and sensor actions on a global scale
- Simplifying configuration settings
- Automatic handling of security information uploads and downloads
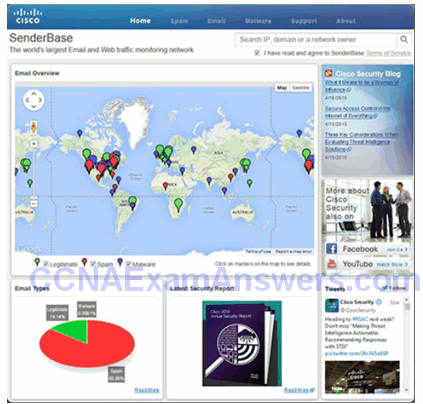
Cisco SensorBase Network
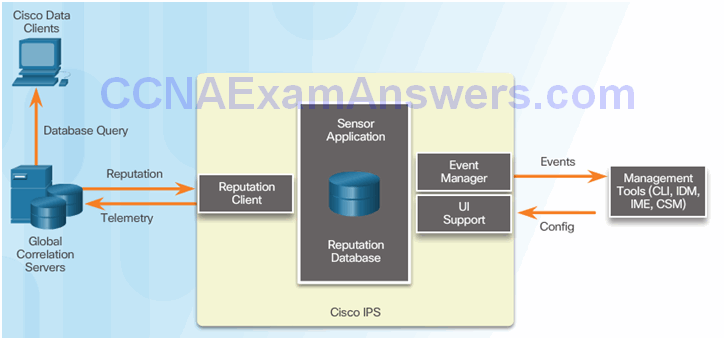
Cisco Security Intelligence Operation
Network participation gathers the following data:
- Signature ID
- Attacker IP address
- Attacker port
- Maximum segment size
- Victim IP address
- Victim port
- Signature version
- TCP options string
- Reputation score
- Risk rating
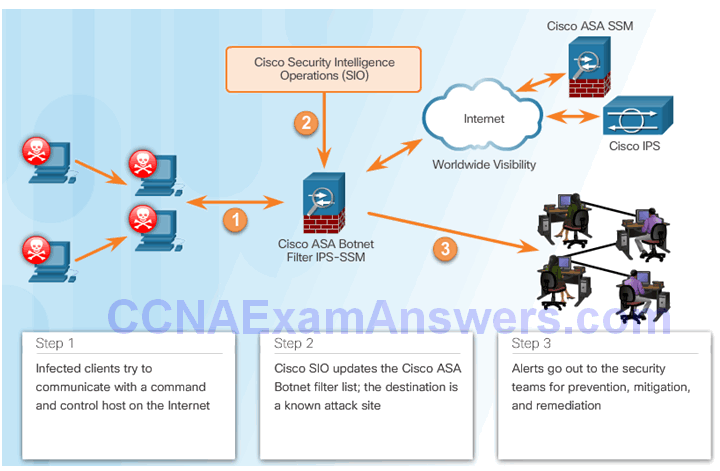
Reputations, Blacklists, and Traffic Filters
Section 5.3: Implement IPS
Upon completion of this section, you should be able to:
- Understand how to configure Cisco IOS IPS with CLI
- Explain how to verify and monitor IPS
Topic 5.3.1: Configure Cisco IOS IPS with CLI
Implement IOS IPS
- Step 1. Download the IOS IPS files.
- Step 2. Create an IOS IPS configuration directory in Flash.
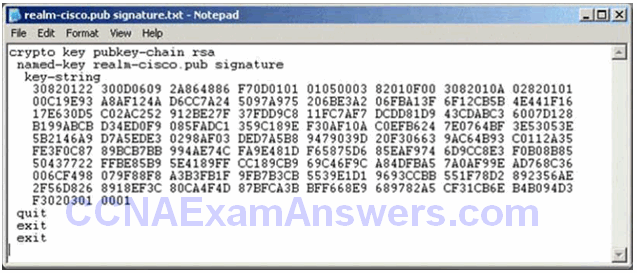
- Step 3. Configure an IOS IPS crypto key.
- Step 4. Enable IOS IPS.
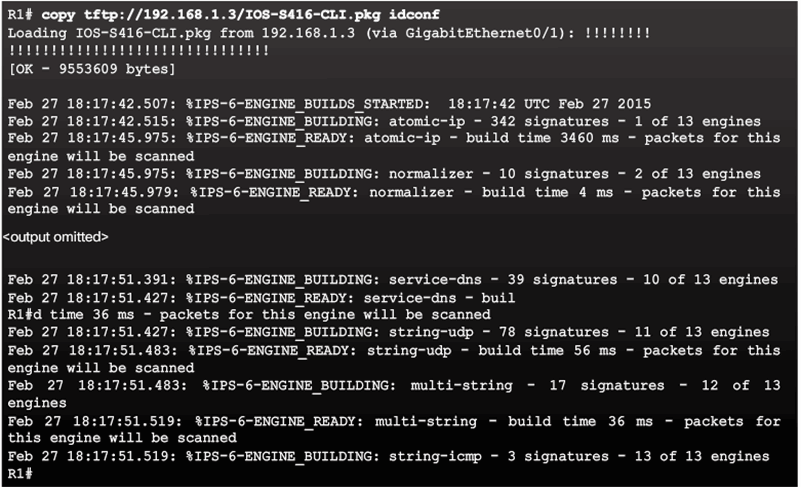
- Step 5. Load the IOS IPS signature package to the router.
Download the IOS IPS Files
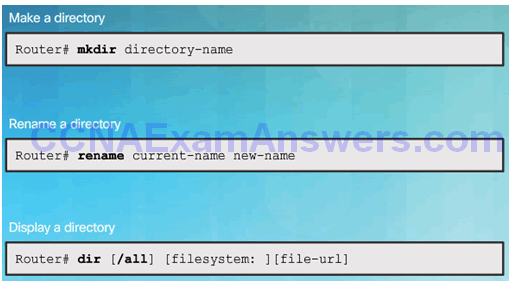
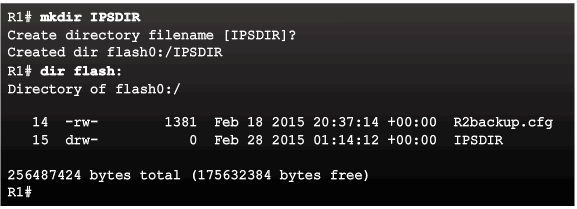
IPS Crypto Key
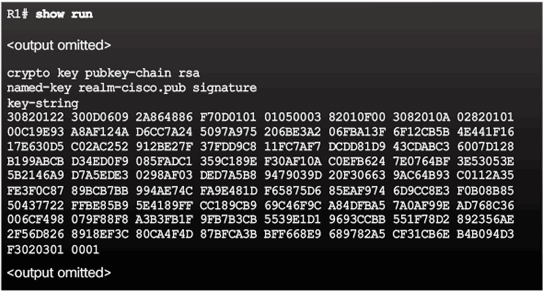
Enable IOS IPS
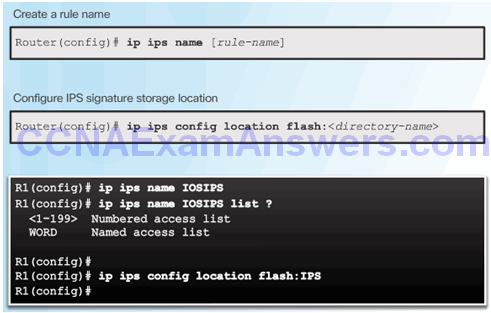
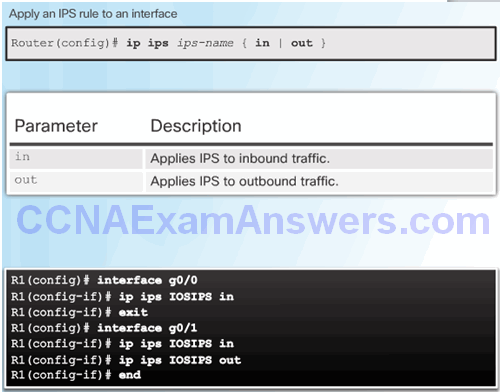
Load the IPS Signature Package in RAM
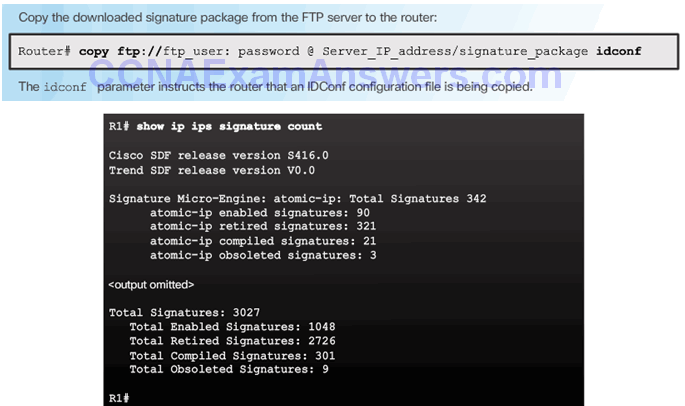
Topic 5.3.2: Modifying Cisco IOS IPS Signatures
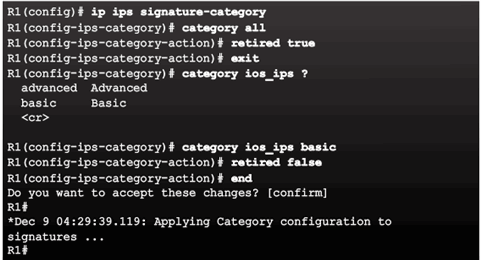
Retire and Unretire Signatures
Retiring an Individual Signature:
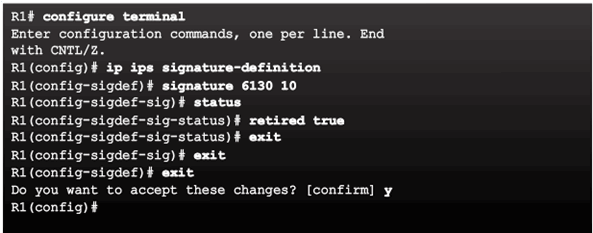
Retiring a Signature Category:
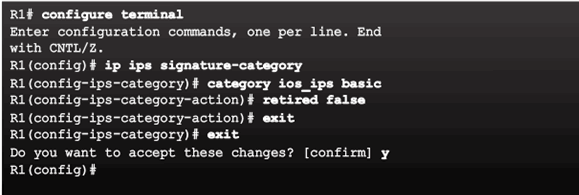
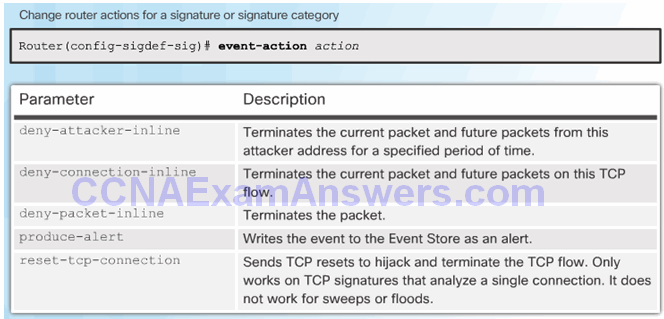
Change Signature Actions
Topic 5.3.3: Verify and Monitor IPS
Verify IOS IPS
- Show commands to verify the IOS IPS configuration:
- show ip ips
- show ip ips all
- show ip ips configuration
- show ip ips interfaces
- show ip ips signatures
- show ip ips statistics
- Clear commands to disable IPS:
- clear ip ips configuration
- clear ip ips statistics
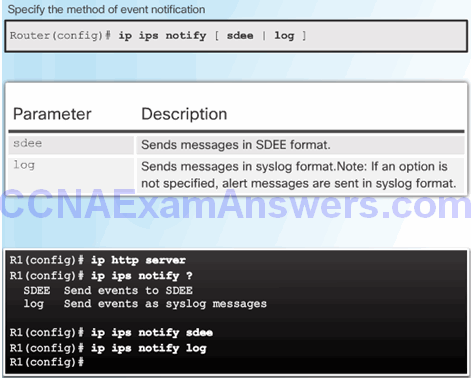
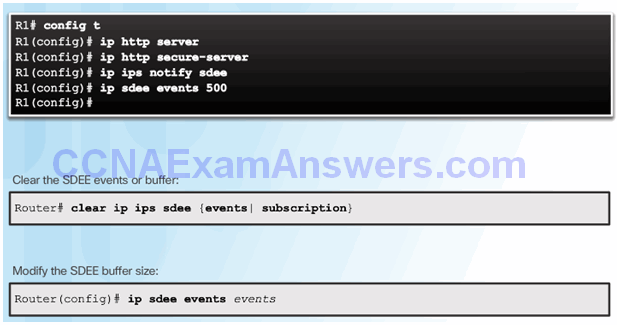
Report IPS Alerts

Enable SDEE
Section 5.4: Summary
Chapter Objectives:
- Describe IPS technologies and how they are implemented.
- Explain IPS Signatures.
- Describe the IPS implementation process.
Download Slide PowerPoint (pptx):
[sociallocker id=”2293″][wpdm_package id=’3006′][/sociallocker]
