9.3.1.2 Packet Tracer Simulation – TCP and UDP Communications (Instructor Version – Optional Packet Tracer)
Topology
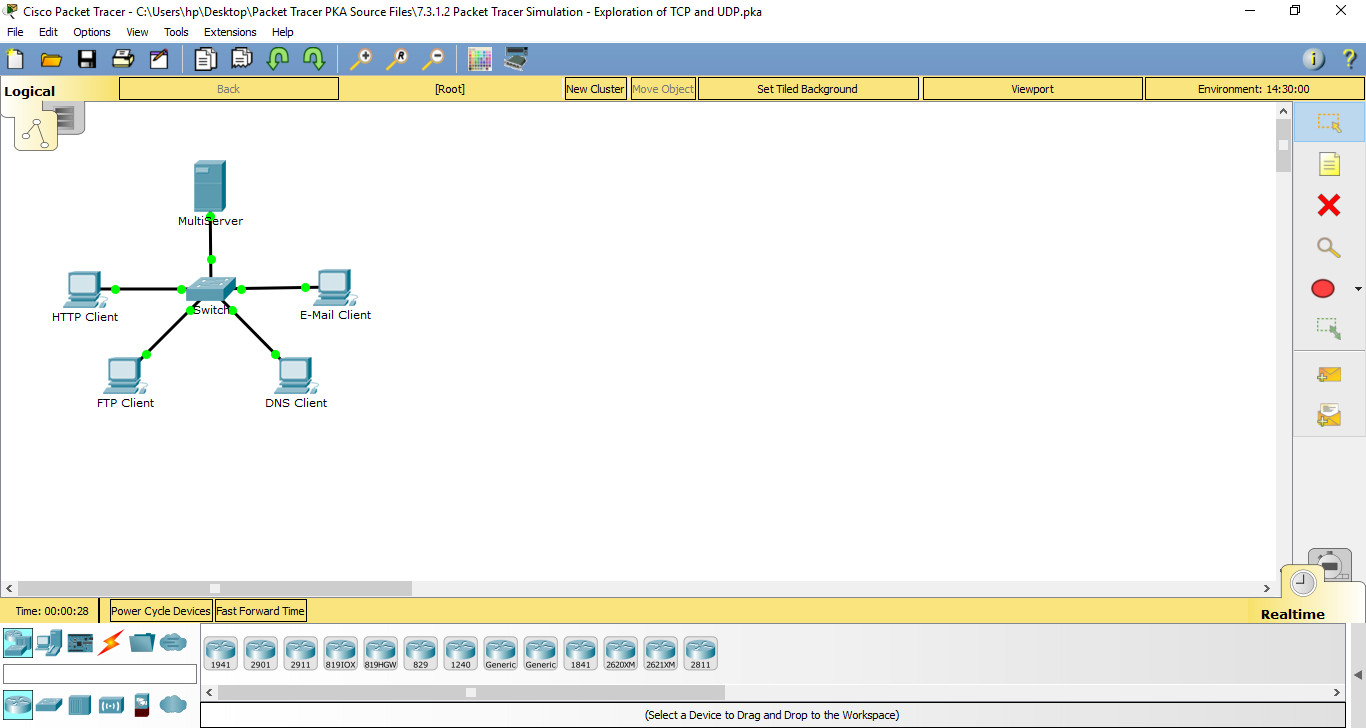
Packet Tracer Simulation – TCP and UDP Communications
Objectives
Part 1: Generate Network Traffic in Simulation Mode
Part 2: Examine the Functionality of the TCP and UDP Protocols
Background
This simulation activity is intended to provide a foundation for understanding the TCP and UDP in detail. Simulation mode provides the ability to view the functionality of the different protocols.
As data moves through the network, it is broken down into smaller pieces and identified in some fashion so that the pieces can be put back together. Each of these pieces is assigned a specific name (protocol data unit [PDU]) and associated with a specific layer. Packet Tracer Simulation mode enables the user to view each of the protocols and the associated PDU. The steps outlined below lead the user through the process of requesting services using various applications available on a client PC.
This activity provides an opportunity to explore the functionality of the TCP and UDP protocols, multiplexing and the function of port numbers in determining which local application requested the data or is sending the data.
Part 1: Generate Network Traffic in Simulation Mode
Step 1: Generate traffic to populate Address Resolution Protocol (ARP) tables.
Perform the following tasks task to reduce the amount of network traffic viewed in the simulation.
a. Click MultiServer and click the Desktop tab > Command Prompt.
b. Enter the ping 192.168.1.255 command. This will take a few seconds as every device on the network responds to MultiServer.
c. Close the MultiServer window.
Step 2: Generate web (HTTP) traffic.
a. Switch to Simulation mode.
b. Click HTTP Client and click the Desktop tab > Web Browser.
c. In the URL field, enter 192.168.1.254 and click Go. Envelopes (PDUs) will appear in the simulation window.
d. Minimize, but do not close, the HTTP Client configuration window.
Step 3: Generate FTP traffic.
a. Click FTP Client and click the Desktop tab > Command Prompt.
b. Enter the ftp 192.168.1.254 command. PDUs will appear in the simulation window.
c. Minimize, but do not close, the FTP Client configuration window.
Step 4: Generate DNS traffic.
a. Click DNS Client and click the Desktop tab > Command Prompt.
b. Enter the nslookup multiserver.pt.ptu command. A PDU will appear in the simulation window.
c. Minimize, but do not close, the DNS Client configuration window.
Step 5: Generate Email traffic.
a. Click E-Mail Clien and click the Desktop tab > E Mail tool.
b. Click Compose and enter the following information:
1) To: [email protected]
2) Subject: Personalize the subject line
3) E-Mail Body: Personalize the Email
c. Click Send.
d. Minimize, but do not close, the E-Mail Client configuration window.
Step 6: Verify that the traffic is generated and ready for simulation.
Every client computer should have PDUs listed in the Simulation Panel.
Part 2: Examine Functionality of the TCP and UDP Protocols
Step 1: Examine multiplexing as all of the traffic crosses the network.
You will now use the Capture/Forward button and the Back button in the Simulation Panel.
a. Click Capture/Forward once. All of the PDUs are transferred to the switch.
b. Click Capture/Forward again. Some of the PDUs disappear. What do you think happened to them? They are stored in the switch
c. Click Capture/Forward six times. All clients should have received a reply. Note that only one PDU can cross a wire in each direction at any given time. What is this called? Multiplexing.
d. A variety of PDUs appears in the event list in the upper right pane of the simulation window. Why are they so many different colors? They represent different protocols.
e. Click Back eight times. This should reset the simulation.
NOTE: Do not click Reset Simulation any time during this activity; if you do, you will need to repeat the steps in Part 1.
Step 2: Examine HTTP traffic as the clients communicate with the server.
a. Filter the traffic that is currently displayed to display only HTTP and TCP PDUs filter the traffic that is currently displayed:
1) Click Edit Filters and toggle the Show All/None check box.
2) Select HTTP and TCP. Click anywhere outside of the Edit Filters box to hide it. The Visible Events should now display only HTTP and TCP PDUs.
b. Click Capture/Forward. Hold your mouse above each PDU until you find one that originates from HTTP Client. Click the PDU envelope to open it.
c. Click the Inbound PDU Details tab and scroll down to the last section. What is the section labeled? TCP
Are these communications considered to be reliable? Yes
d. Record the SRC PORT, DEST PORT, SEQUENCE NUM, and ACK NUM values. What is written in the field to the left of the WINDOW field?
1025 (could be different), 80, 0, 0 SYN
e. Close the PDU and click Capture/Forward until a PDU returns to the HTTP Client with a checkmark.
f. Click the PDU envelope and select Inbound PDU Details. How are the port and sequence numbers different than before?
80, 1025, 0, 1. SYN+ACK. The source and destination ports are reversed, and the acknowledgement number is 1. The SYN has changed to SYN+ACK.
g. There is a second PDU of a different color, which HTTP Client has prepared to send to MultiServer. This is the beginning of the HTTP communication. Click this second PDU envelope and select Outbound PDU Details.
h. What information is now listed in the TCP section? How are the port and sequence numbers different from the previous two PDUs?
1025, 80, 1, 1. PSH+ACK The source and destination ports are reversed, and both sequence and acknowledgement numbers are 1.
i. Click Back until the simulation is reset.
Step 3: Examine FTP traffic as the clients communicate with the server.
a. In the Simulation Panel, change Edit Filters to display only FTP and TCP.
b. Click Capture/Forward. Hold your cursor above each PDU until you find one that originates from FTP Client. Click that PDU envelope to open it.
c. Click the Inbound PDU Details tab and scroll down to the last section. What is the section labeled? TCP
Are these communications considered to be reliable? Yes.
d. Record the SRC PORT, DEST PORT, SEQUENCE NUM, and ACK NUM values. What is written in the field to the left of the WINDOW field? 1025, 21, 0, 0. SYN
e. Close the PDU and click Capture/Forward until a PDU returns to the FTP Client with a checkmark.
f. Click the PDU envelope and select Inbound PDU Details. How are the port and sequence numbers different than before?
21, 1025, 0, 1. SYN+ACK. The source and destination ports are reversed, and the acknowledgement number is 1.
g. Click the Outbound PDU Details tab. How are the port and sequence numbers different from the previous two results?
1025, 21, 1, 1. ACK. The source and destination ports are reversed, and both sequence and acknowledgement numbers are 1.
h. Close the PDU and click Capture/Forward until a second PDU returns to the FTP Client. The PDU is a different color.
i. Open the PDU and select Inbound PDU Details. Scroll down past the TCP section. What is the message from the server?
May say either “Username ok, need password” or “Welcome to PT Ftp server”
j. Click Back until the simulation is reset.
Step 4: Examine DNS traffic as the clients communicate with the server.
a. In the Simulation Panel, change Edit Filters to display only DNS and UDP.
b. Click the PDU envelope to open it.
c. Click the Inbound PDU Details tab and scroll down to the last section. What is the section labeled? UDP
Are these communications considered to be reliable? No
d. Record the SRC PORT and DEST PORT values. Why is there no sequence and acknowledgement number? 1025, 53. Because UDP does not need to establish a reliable connection.
e. Close the PDU and click Capture/Forward until a PDU returns to the DNS Client with a checkmark.
f. Click the PDU envelope and select Inbound PDU Details. How are the port and sequence numbers different than before?
53, 1025. The source and destination ports are reversed
g. What is the last section of the PDU called? DNS ANSWER
h. Click Back until the simulation is reset.
Step 5: Examine email traffic as the clients communicate with the server.
a. In the Simulation Panel, change Edit Filters to display only POP3, SMTP and TCP.
b. Click Capture/Forward. Hold your cursor above each PDU until you find one that originates from E-mail Client. Click that PDU envelope to open it.
c. Click the Inbound PDU Details tab and scroll down to the last section. What transport layer protocol does email traffic use? TCP
Are these communications considered to be reliable? Yes
d. Record the SRC PORT, DEST PORT, SEQUENCE NUM, and ACK NUM values. What is written in the field to the left of the WINDOW field? 1025, 25, 0, 0. SYN
e. Close the PDU and click Capture/Forward until a PDU returns to the E-Mail Client with a checkmark.
f. Click the PDU envelope and select Inbound PDU Details. How are the port and sequence numbers different than before?
25, 1025, 0, 1. SYN+ACK. The source and destination ports are reversed, and the acknowledgement number is 1.
g. Click the Outbound PDU Details tab. How are the port and sequence numbers different from the previous two results?
1025, 25, 1, 1. ACK. The source and destination ports are reversed, and both sequence and acknowledgement numbers are 1. ACK
h. There is a second PDU of a different color that HTTP Client has prepared to send to MultiServer. This is the beginning of the email communication. Click this second PDU envelope and select Outbound PDU Details.
i. How are the port and sequence numbers different from the previous two PDUs?
1025, 25, 1, 1. PSH+ACK. The source and destination ports are reversed, and both sequence and acknowledgement numbers are 1.
j. What email protocol is associated with TCP port 25? What protocol is associated with TCP port 110?
SMTP. POP3
k. Click Back until the simulation is reset.
Step 6: Examine the use of port numbers from the server.
a. To see TCP active sessions, perform the following steps in quick succession:
1) Switch back to Realtime mode.
2) Click MultiServer and click the Desktop tab > Command Prompt.
b. Enter the netstat command. What protocols are listed in the left column? TCP
What port numbers are being used by the server?
Answers will vary, but students may see all three: 21, 25, 80. They should certainly see 21
c. What states are the sessions in?
Answer will vary. Possible states include CLOSED, ESTABLISHED, LAST_ACK
d. Repeat the netstat command several times until you see only one session still ESTABLISHED. For which service is this connection still open? FTP
Why doesn’t this session close like the other three? (Hint: Check the minimized clients)
The server is waiting for a password from the client
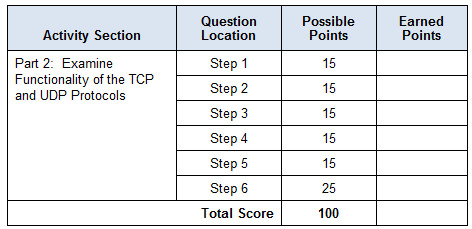
Suggested Scoring Rubric
Download PDF & PKA file:
[sociallocker id=”54558″]
[wpdm_package id=’5268′]
[wpdm_package id=’35307′]
[/sociallocker]

Where is the .pka?
added, sorry for this omission
no apology necessary! when i become a network engineer i will repay the favor!