Chapter Outline:
3.0 Introduction
3.1 Purpose of the AAA
3.2 Local AAA Authentication
3.3 Server-Based AAA
3.4 Server-Based AAA Authentication
3.5 Server-Based Authorization and Accounting
3.6 Summary
Section 3.1: Purpose of the AAA
Upon completion of this section, you should be able to:
- Explain why AAA is critical to network security.
- Describe the characteristics of AAA.
Topic 3.1.1: AAA Overview
Authentication without AAA
Telnet is Vulnerable to Brute-Force Attacks
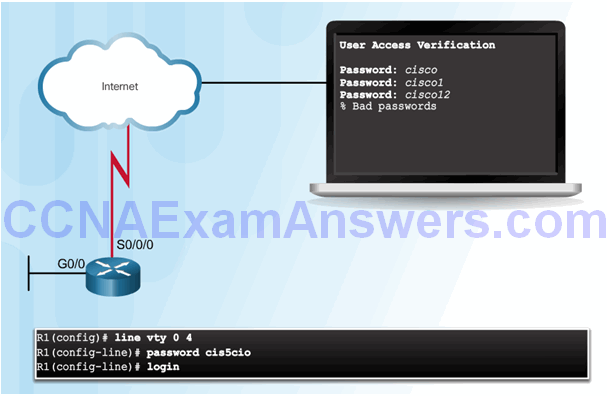
AAA Components
Topic 3.1.2: AAA Characteristics
Authentication Modes
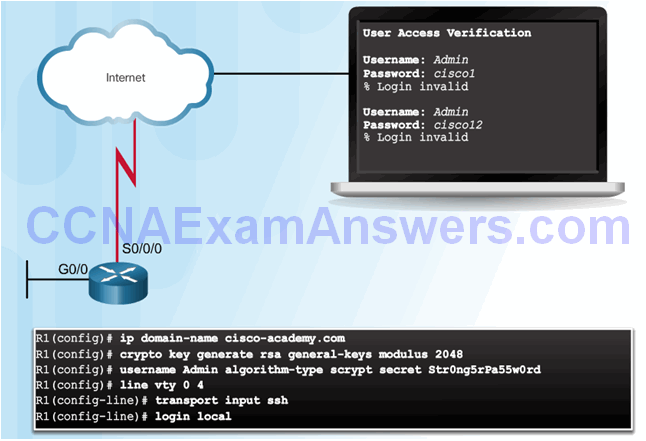
Local AAA Authentication

Server-Based AAA Authentication
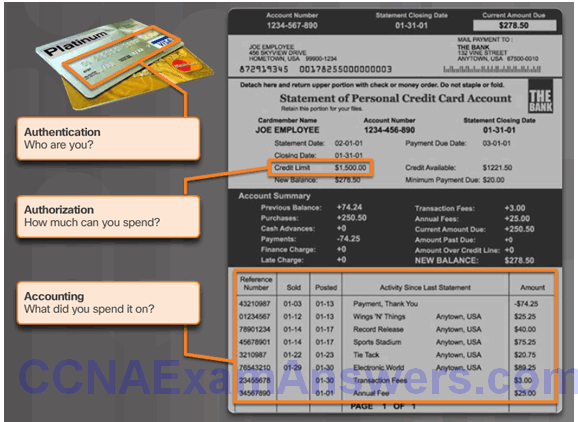
Authorization
AAA Authorization

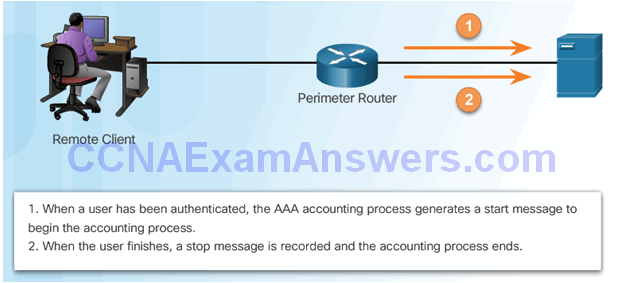
Accounting
- Types of accounting information:
- Network
- Connection
- EXEC
- System
- Command
- Resource
AAA Accounting
Activity – Indentify the Characteristics of AAA
Section 3.2: Local AAA Authentication
Upon completion of this section, you should be able to:
- Configure AAA authentication, using the CLI, to validate users against a local database.
- Troubleshoot AAA authentication that validates users against a local database.
Topic 3.2.1: Configuring Local AAA Authentication with CLI
Authenticating Administrative Access
- Add usernames and passwords to the local router database for users that need administrative access to the router.
- Enable AAA globally on the router.
- Configure AAA parameters on the router.
- Confirm and troubleshoot the AAA configuration.
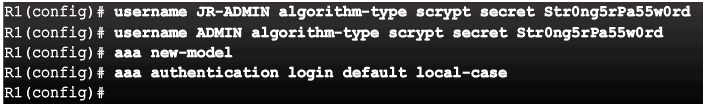
Authentication Methods
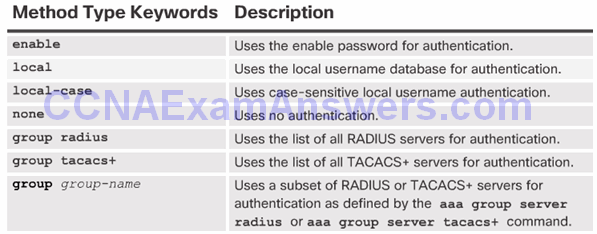
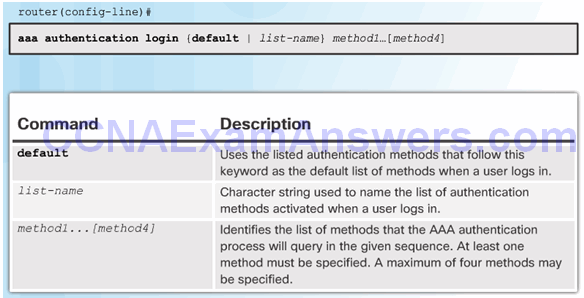
Default and Named Methods
Example Local AAA Authentication
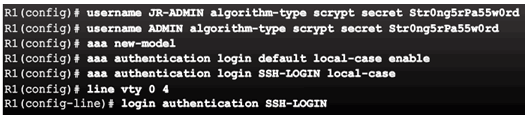
Fine-Tuning the Authentication Configuration
Command Syntax
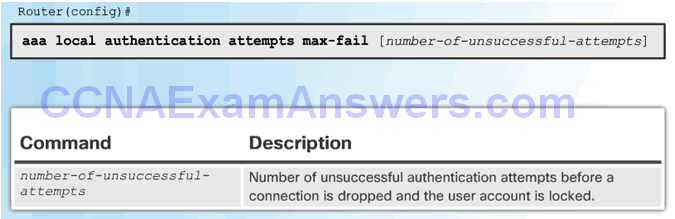
Display Locked Out Users
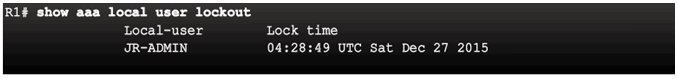
Show Unique ID of a Session

Topic 3.2.2: Troubleshooting Local AAA Authentication
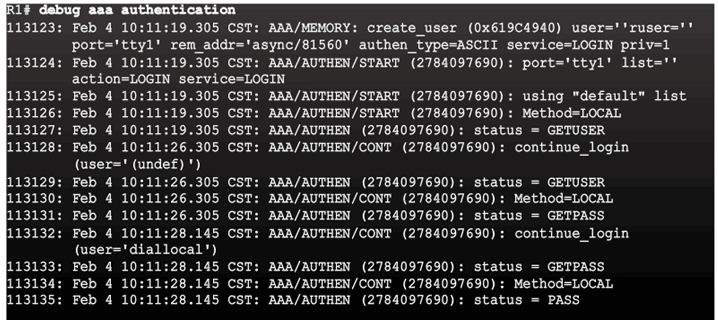
Debug Options
Debug Local AAA Authentication
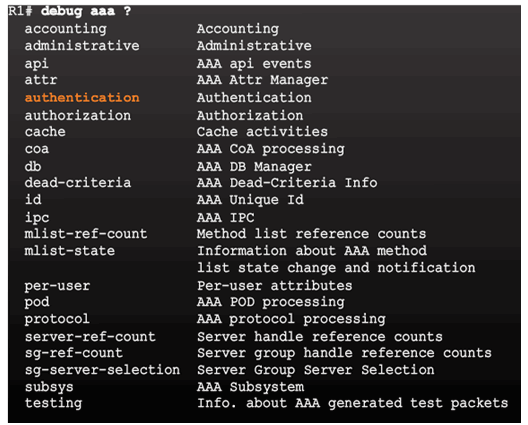
Debugging AAA Authentication
Understanding Debug Output
Section 3.3: Server-Based AAA
Upon completion of this section, you should be able to:
- Describe the benefits of server-based AAA.
- Compare the TACACS+ and RADIUS authentication protocols.
Topic 3.3.1: Server-Based AAA Characteristics
Comparing Local AAA and Server-Based AAA Implementations
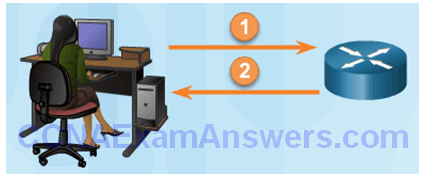
Local authentication:
- User establishes a connection with the router.
- Router prompts the user for a username and password, authentication the user using a local database.
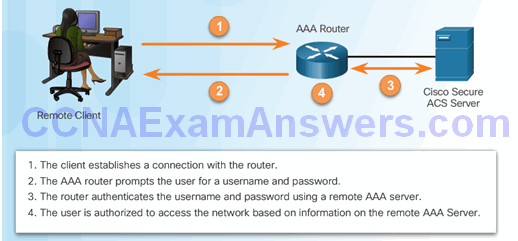
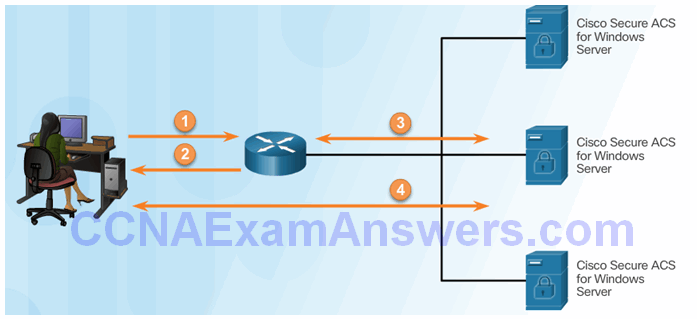
Server-based authentication:
- User establishes a connection with the router.
- Router prompts the user for a username and password.
- Router passes the username and password to the Cisco Secure ACS (server or engine)
- The Cisco Secure ACS authenticates the user.
Introducing Cisco Secure Access Control System
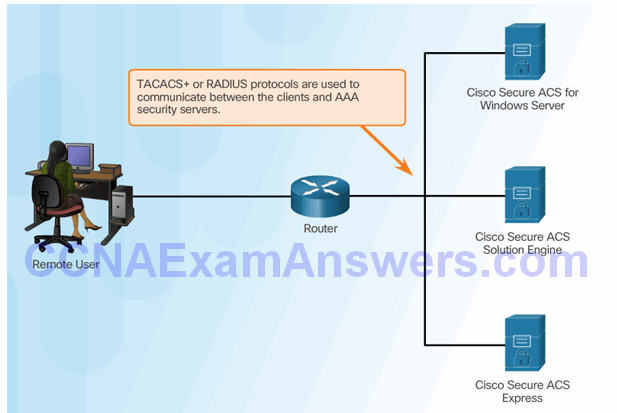
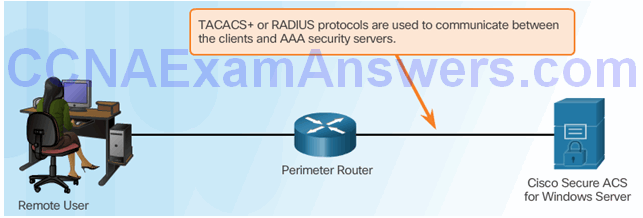
Topic 3.3.2: Server-Based AAA Communication Protocols
Introducing TACACS+ and RADIUS
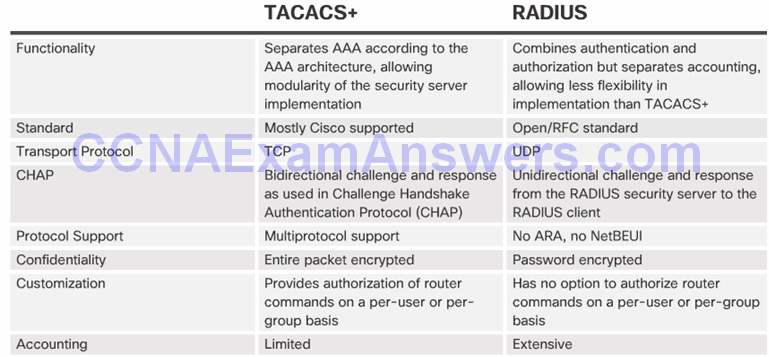
TACACS+ Authentication
TACACS+ Authentication Process
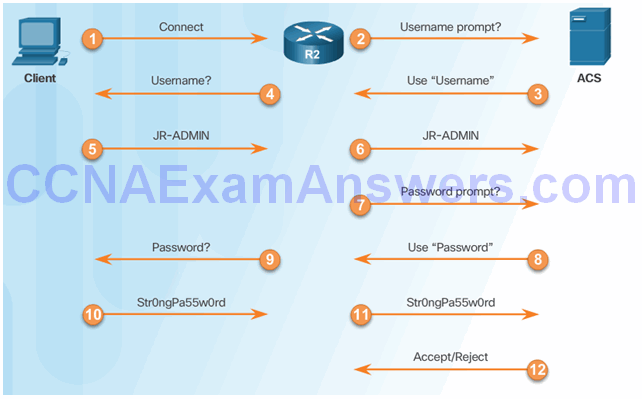
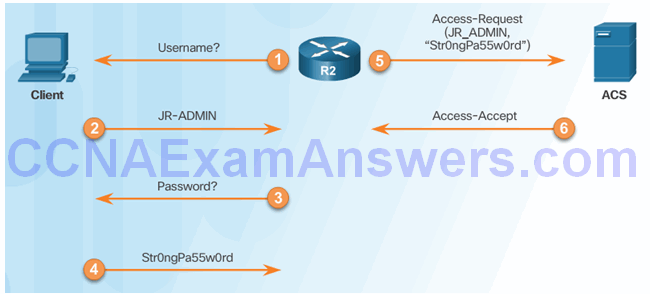
RADIUS Authentication
RADIUS Authentication Process
Integration of TACACS+ and ACS
Cisco Secure ACS
Integration of AAA with Active Directory
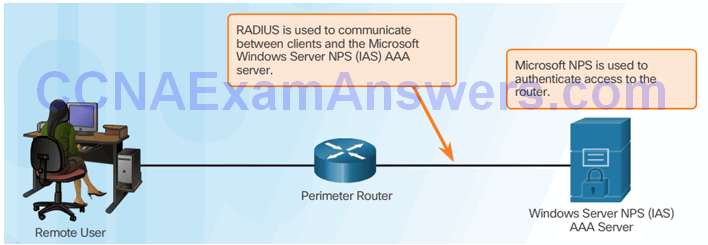
Section 3.4: Server-Based AAA Authentication
Upon completion of this section, you should be able to:
- Configure server-based AAA authentication, using the CLI, on Cisco routers.
- Troubleshoot server-based AAA authentication.
Topic 3.4.1: Configuring Server-Based Authentication with CLI
Steps for Configuring Server-Based AAA Authentication with CLI
- Enable AAA.
- Specify the IP address of the ACS server.
- Configure the secret key.
- Configure authentication to use either the RADIUS or TACACS+ server.
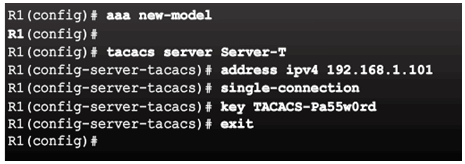
Configuring the CLI with TACACS+ Servers
Server-Based AAA Reference Topology
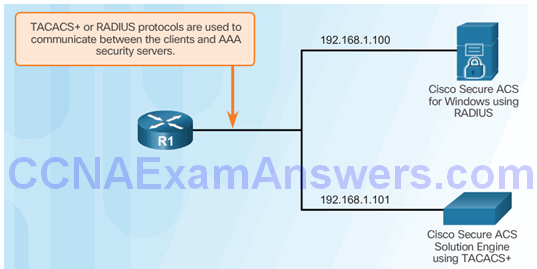
Configure a AAA TACACS+ Server
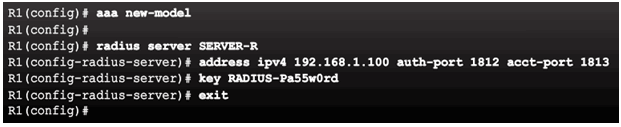
Configuring the CLI for RADIUS Servers
Configure a AAA RADIUS Server
Configure Authentication to Use the AAA Server
Command Syntax
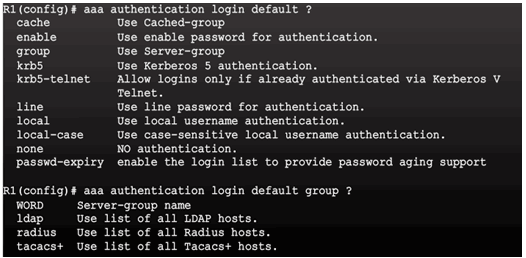
Configure Server-Based AAA Authentication
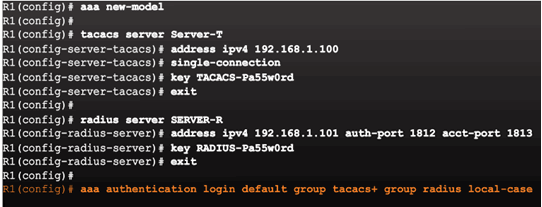
Topic 3.4.2: Troubleshooting Server-Based AAA Authentication
Monitoring Authentication Traffic
Troubleshooting Server-Based AAA Authentication
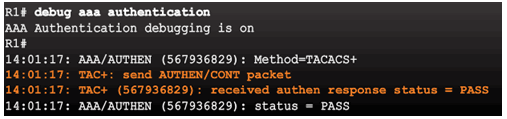
Debugging TACACS+ and RADIUS
Troubleshooting RADIUS
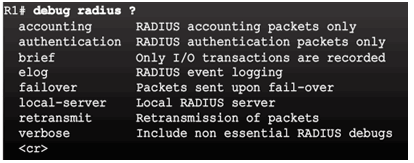
Troubleshooting TACACS+
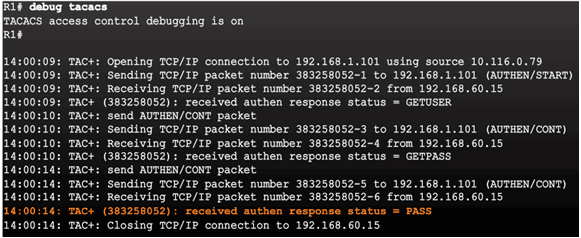
AAA Server-Based Authentication Success
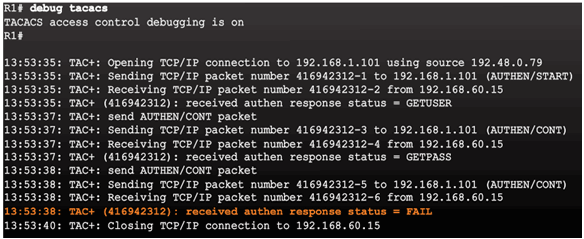
AAA Server-Based Authentication Failure
Section 3.5: Server-Based AAA Authorization and Accounting
Upon completion of this section, you should be able to:
- Configure server-based AAA authorization.
- Configure server-based AAA accounting.
- Explain the functions of 802.1x components.
Topic 3.5.1: Configuring Server-Based AAA Authorization
Introduction to Server-Based AAA Authorization
- Authentication vs. Authorization
- Authentication ensures a device or end-user is legitimate
- Authorization allows or disallows authenticated users access to certain areas and programs on the network.
- TACACS+ vs. RADIUS
- TACACS+ separates authentication from authorization
- RADIUS does not separate authentication from authorization
AAA Authorization Configuration with CLI
Command Syntax
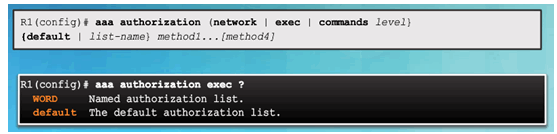
Authorization Method Lists
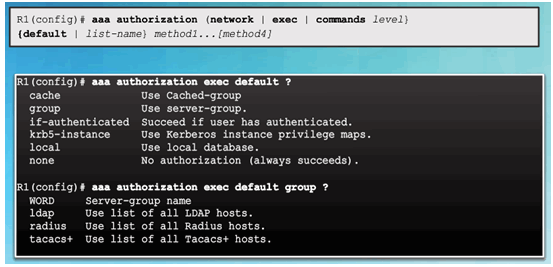
Example AAA Authorization
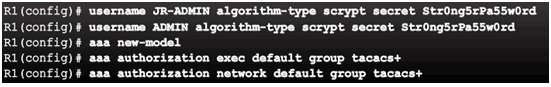
Topic 3.5.2: Configuring Server-Based AAA Accounting
Introduction to Server-Based AAA Accounting
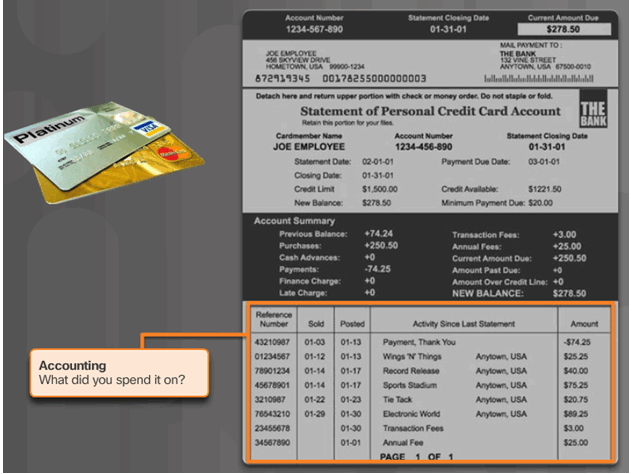
AAA Accounting Configuration with CLI
Command Syntax
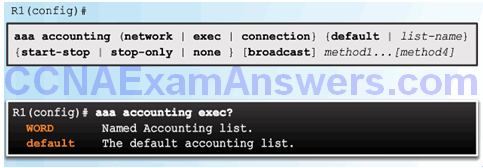
Accounting Method Lists
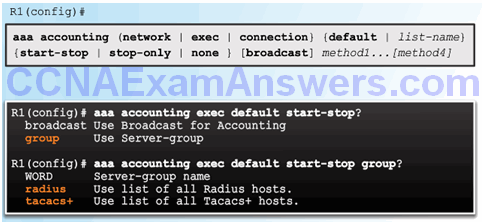
Example AAA Accounting
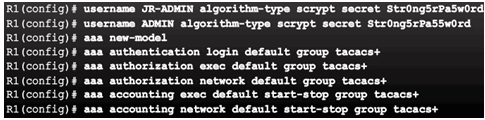
Topic 3.5.3: 802.1X Authentication
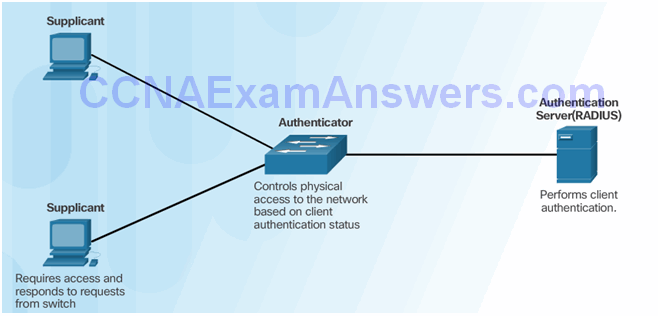
Security Using 802.1X Port-Based Authentication
802.1X Roles
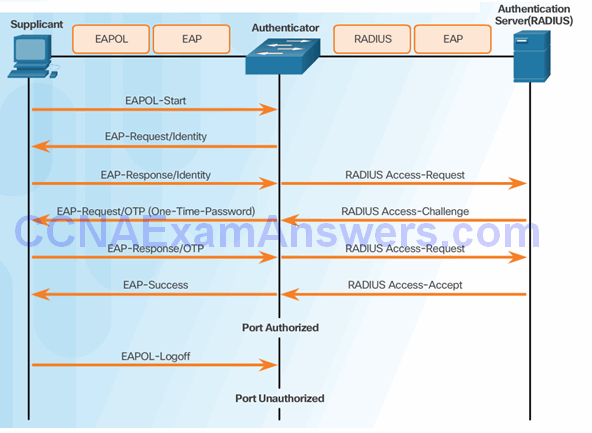
802.1X Message Exchange
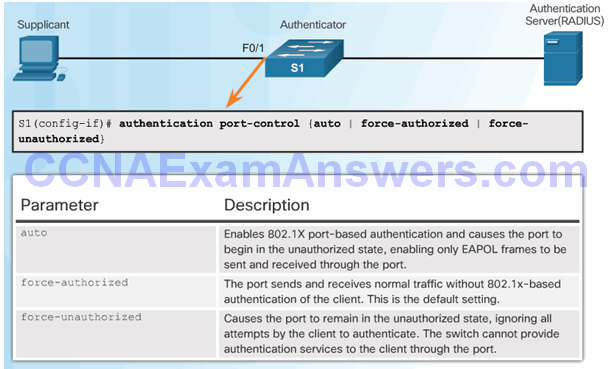
802.1X Port Authorization State
Command Syntax for dot1x port-control
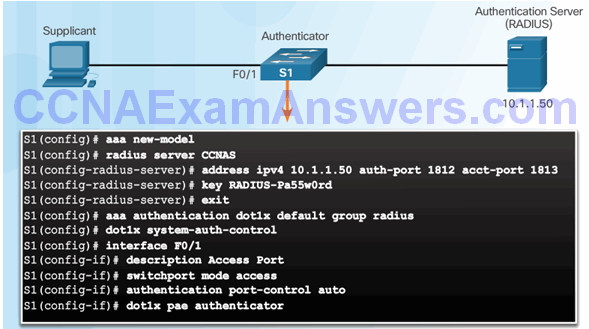
Configuring 802.1X
Section 3.6: Summary
Chapter Objectives:
- Explain how AAA is used to secure a network.
- Implement AAA authentication that validates users against a local database.
- Implement server-based AAA authentication using TACACS+ and RADIUS protocols.
- Configure server-based AAA authorization and accounting.
Download Slide PowerPoint (pptx):
[sociallocker id=”2293″][wpdm_package id=’2892′][/sociallocker]
