CCNA 2 Chapter 7 RSE Practice Skills Assessment
CCNA Routing and Switching
Routing & Switching Essentials
Chapter 7 SIC: VLANs, Trunking, and Router-on-a-Stick
A few things to keep in mind while completing this activity:
- Do not use the browser Back button or close or reload any exam windows during the exam.
- Do not close Packet Tracer when you are done. It will close automatically.
- Click the Submit Assessment button in the browser window to submit your work.
Introduction
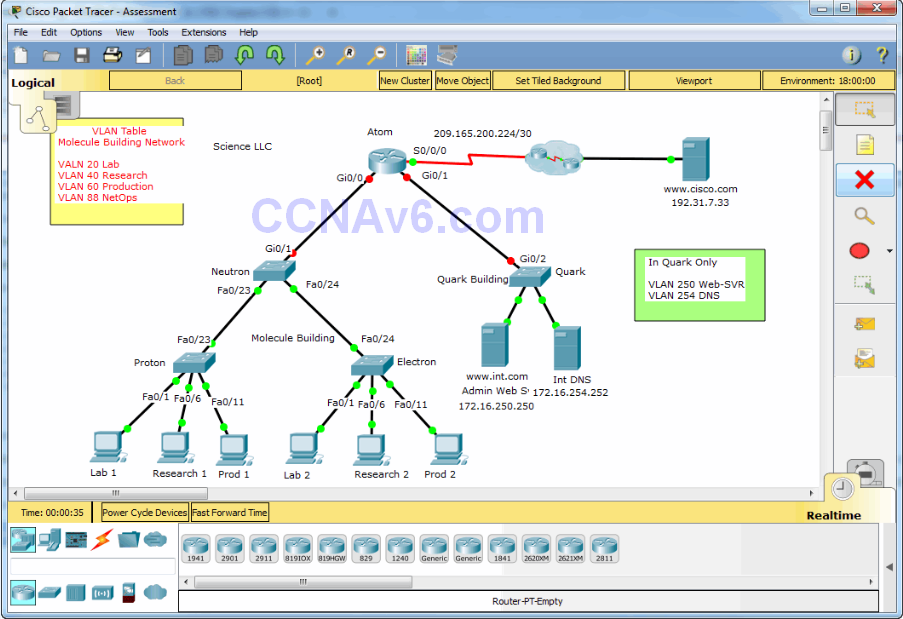
In this practice skills assessment, you will configure the Science LLC network with VLANs, Trunking, inter-VLAN routing, and IPv4 standard ACLs. As part of this process, you will perform basic VLAN configuration tasks, address router interfaces and hosts, and implement two ACLs.
You are not required to configure the Quark switch, or any of the servers.
Note: In order to keep the assessment activity as brief as possible, you will only be partially configuring some devices, as directed in the instructions. In a real network, all devices would be fully configured to function in the network. You are only responsible for completing the tasks covered in the instructions. Any configuration that you do beyond the requirements will not result in additional credit.
All IOS device configurations should be completed from a direct terminal connection to the device console. In addition, many values that are required to complete the configurations have not been given to you. In those cases, create the values that you need to complete the requirements.
You will practice and be assessed on the following skills:
- Configuration of initial device settings
- IPv4 address assignment
- Configuration and addressing of device interfaces
- Configuration of VLANs on three switches
- Configuration of trunking and inter-VLAN routing
- Configuration of ACL to limit device access
Requirements by device:
Router Atom:
- Configuration of initial router settings
- Interface configuration and IPv4 addressing
Switch Neutron:
- Configuration of VLANs
- Configuration of VLAN trunking
- Configuration of interfaces into VLAN
- Configuration of IP address for the Management VLAN
Switch Proton:
- Configuration of VLANs
- Configuration of VLAN trunking
- Configuration of interfaces into VLAN
- Configuration of IP address for the Management VLAN
Switch Electron:
- Configuration of VLANs
- Configuration of VLAN trunking
- Configuration of interfaces into VLAN
- Configuration of IP address for the Management VLAN
PC hosts:
- Pv4 full addressing
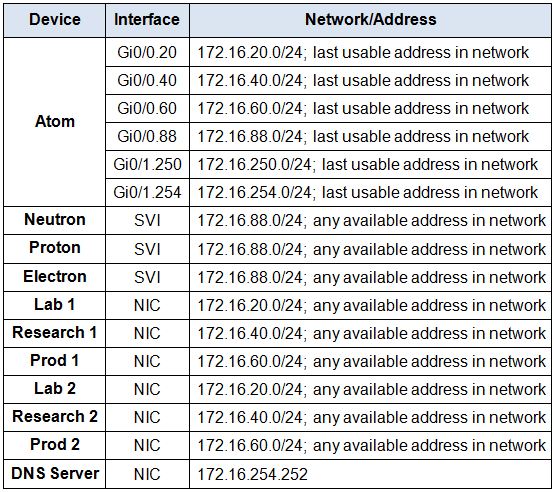
Addressing Table
Note: You are provided with the networks that interfaces should be configured on. Unless you are told to do differently in the detailed instructions below, you are free to choose the host addresses to assign.
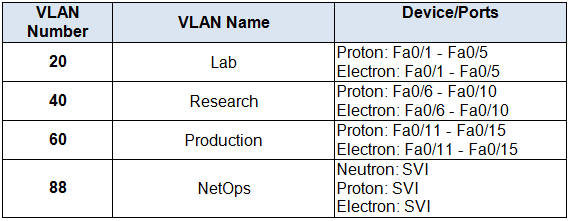
VLAN Assignment Table
Instructions
Step 1: Determine Addressing
Determine the IP addresses that you will use for the required interfaces on the three switch SVIs, and the six LAN hosts. Use the information in the addressing table.
- Select the switch SVI addresses.
- The interfaces on the Atomrouter that are used to route the VLANs should be addressed with the last usable IP address in the subnet.
- Assign valid host addresses to the LAN hosts according to the Addressing Table and VLAN assignment.
Step 2: Configure initial device setting on Neutron and Atom
Configure Neutron and Atom with all initial configurations that you have learned in the course so far:
- Configure the switch hostname: Neutron.
- Configure the router hostname: Atom.
- Prevent the router from attempting to resolve unrecognized CLI entries as domain names.
- Protect device configurations from unauthorized access with the encrypted password cisco.
- Secure the router and switch console and remote access lines with password cisco.
- Prevent all passwords from being viewed in clear text in device configuration files.
Step 3: Configure VLANs
Configure four VLANs on the Neutron, Proton, and Electron switches using the values in the addressing table.
Step 4: Assign Switch Interfaces to VLANs
Configure FastEthernet interfaces on Proton and Electron according to the following guidelines:
- Interfaces Fa0/1 – Fa0/5 are assigned to VLAN 20
- Interfaces Fa0/6 – Fa0/10 are assigned to VLAN 40
- Interfaces Fa0/11 – Fa0/15 are assigned to VLAN 60
Step 5: Configure the Switches for Remote Management
Configure the SVIs of the Neutron, Proton, and Electron switches using the information in the VLAN and Addressing Tables. Configure the IP address for the Management VLAN and the default-gateway IP address. Configure the SVIs so that they will be reachable by devices on other networks after the network has been fully configured.
Step 6: Configure VLAN Trunking
Configure VLAN trunking between the Neutron, Proton, and Electron switches.
- Manuallyconfigure the VTP domain name to School on the Neutron, Proton, and Electron switches.
- Manuallyconfigure the trunking ports on the Neutron, Proton, and Electron switches.
Step 7: Configure inter-VLAN Routing
Use the information in the Addressing and VLAN tables to configure inter-VLAN routing on Atom according to the following guidelines:
- Configure inter-VLAN routing among VLANs 20, 40, 60 and 88 through Gi0/0 subinterfaces.
- Configure inter-VLAN routing for VLANs 250 and 254 through Gi0/1 subinterfaces.
Step 8: Configure Host Addressing
Address the hosts according to the values in the addressing table. Use a DNS server address of 172.16.254.252. All hosts should be able to reach the www.cisco.com server.
Step 9: Configure Access Control Lists
You will configure two access control lists on the Atom router. The ACL specifications are as follows:
a. Restrict access to the vty lines on Atom.
- Create a numberedstandard ACL using number 10. Be sure that you use this number exactly as it appears in these instructions.
- Allow only hosts on the ProductionVLAN to access the vty lines of Atom.
- No other internal and Internet hosts should be able to access the vty lines of Atom.
- Your solution should consist of a single ACL statement.
b. Restrict access to the internal web server
- Create a named standard ACL using the name INT-WEB. Be sure that you use this name exactly as it appears in these instructions.
- Allow hosts on the Researchand Production VLANs to reach the internal administrative web server at int.com.
- No other internal and Internet hosts should be able to access the internal administrative web server.
- Your solution should consist of two ACL statements.
Step 10: Verify Connectivity
Verify your configurations according to the following guidelines:
-
- Hosts in VLANs 20, 40, and 60 can ping each other.
- Hosts in VLANs 20, 40, and 60 can visit the external web server www.cisco.com.
- Hosts in VLAN 40 and 60 can visit the administrative web server www.int.com.
- Hosts in VLAN 60 can telnet into Atom
- Hosts in VLANs 20 and 40 cannot telnet to Atom.
Intructions – Answer 100%
Router 1: HQ or Atom
[[R1name]]#enable
[[R1name]]#conf ter
[[R1name]](config)#hostname HQ (or Atom)
HQ(config)#no ip domain-lookup
HQ(config)#enable secret cisco
HQ(config)#line console 0
HQ(config-line)#password cisco
HQ(config-line)#login
HQ(config-line)#line vty 0 15
HQ(config-line)#password cisco
HQ(config-line)#login
HQ(config-line)#exit
HQ(config)#int g0/0.20
HQ(config-subif)#encapsulation dot1Q 20
HQ(config-subif)#ip address 172.16.20.254 255.255.255.0
HQ(config-subif)#int g0/0.40
HQ(config-subif)#encapsulation dot1Q 40
HQ(config-subif)#ip address 172.16.40.254 255.255.255.0
HQ(config-subif)#int g0/0.60
HQ(config-subif)#encapsulation dot1Q 60
HQ(config-subif)#ip address 172.16.60.254 255.255.255.0
HQ(config-subif)#int g0/0.88
HQ(config-subif)#encapsulation dot1Q 88
HQ(config-subif)#ip address 172.16.88.254 255.255.255.0
HQ(config-subif)#int g0/0
HQ(config-if)#no sh
HQ(config-if)#int g0/1.250
HQ(config-subif)#encapsulation dot1Q 250
HQ(config-subif)#ip address 172.16.250.254 255.255.255.0
HQ(config-subif)#int g0/1.254
HQ(config-subif)#encapsulation dot1Q 254
HQ(config-subif)#ip address 172.16.254.254 255.255.255.0
HQ(config-subif)#int g0/1
HQ(config-if)#no shutdown
HQ(config-if)#exit
HQ(config)#access-list 10 permit 172.16.60.0 0.0.0.255
HQ(config)#access-list 10 deny any
HQ(config)#ip access-list standard INT-WEB
HQ(config-std-nacl)#permit 172.16.40.0 0.0.0.255
HQ(config-std-nacl)#permit 172.16.60.0 0.0.0.255
HQ(config-std-nacl)#exit
HQ(config)#line vty 0 15
HQ(config-line)#access-class 10 in
HQ(config-line)#exit
HQ(config)#int g0/1.250
HQ(config-subif)#ip access-group INT-WEB out
HQ(config-subif)#
Switch 1: Mgmt or Neutron
[[SW1name]]>en
[[SW1name]]#conf ter
[[SW1name]](config)#hostname Mgmt (or Neutron)
Mgmt(config)#no ip domain-lookup
Mgmt(config)#enable secret cisco
Mgmt(config)#line console 0
Mgmt(config-line)#password cisco
Mgmt(config-line)#login
Mgmt(config-line)#line vty 0 15
Mgmt(config-line)#password cisco
Mgmt(config-line)#login
Mgmt(config-line)#exit
Mgmt(config)#service password-encryption
Mgmt(config)#vlan 20
Mgmt(config-vlan)#name Clerical
Mgmt(config-vlan)#vlan 40
Mgmt(config-vlan)#name Acct
Mgmt(config-vlan)#vlan 60
Mgmt(config-vlan)#name HR
Mgmt(config-vlan)#vlan 88
Mgmt(config-vlan)#name NetAdmin
Mgmt(config-vlan)#exit
Mgmt(config)#int vlan 88
Mgmt(config-if)#ip add 172.16.88.253 255.255.255.0
Mgmt(config-if)#no shutdown
Mgmt(config-if)#exit
Mgmt(config)#ip default-gateway 172.16.88.254
Mgmt(config)#vtp domain School
Mgmt(config)#int g0/1
Mgmt(config-if)#switchport mode trunk
Mgmt(config-if)#int range f0/23-24
Mgmt(config-if-range)#switchport mode trunk
Mgmt(config-if-range)#
Switch 2: Acct or Proton
[[SW2name]]>en
[[SW2name]]#conf ter
[[SW2name]](config)#hostname Acct (or Proton)
Acct(config)#vlan 20
Acct(config-vlan)#name Clerical
Acct(config-vlan)#vlan 40
Acct(config-vlan)#name Acct
Acct(config-vlan)#vlan 60
Acct(config-vlan)#name HR
Acct(config-vlan)#vlan 88
Acct(config-vlan)#name NetAdmin
Acct(config-vlan)#exit
Acct(config)#int range fastEthernet 0/1-5
Acct(config-if-range)#switchport mode access
Acct(config-if-range)#switchport access vlan 20
Acct(config-if-range)#int range fastEthernet 0/6-10
Acct(config-if-range)#switchport mode access
Acct(config-if-range)#switchport access vlan 40
Acct(config-if-range)#int range fastEthernet 0/11-15
Acct(config-if-range)#switchport mode access
Acct(config-if-range)#switchport access vlan 60
Acct(config-if-range)#exit
Acct(config)#int vlan 88
Acct(config-if)#ip add 172.16.88.252 255.255.255.0
Acct(config-if)#no sh
Acct(config-if)#no shutdown
Acct(config-if)#exit
Acct(config)#ip default-gateway 172.16.88.254
Acct(config)#vtp domain School
Acct(config)#
Acct(config)#int f0/23
Acct(config-if)#switchport mode trunk
Acct(config-if)#
Switch 3: HR or Electron
[[SW3name]]>en
[[SW3name]]#conf ter
[[SW3name]](config)#hostname HR (or Electron)
HR(config)#vlan 20
HR(config-vlan)#name Clerical
HR(config-vlan)#vlan 40
HR(config-vlan)#name Acct
HR(config-vlan)#vlan 60
HR(config-vlan)#name HR
HR(config-vlan)#vlan 88
HR(config-vlan)#name NetAdmin
HR(config-vlan)#exit
HR(config)#int range fa0/1-5
HR(config-if-range)#switchport mode access
HR(config-if-range)#switchport access vlan 20
HR(config-if-range)#int range fa0/6-10
HR(config-if-range)#switchport mode access
HR(config-if-range)#switchport access vlan 40
HR(config-if-range)#int range fa0/11-15
HR(config-if-range)#switchport mode access
HR(config-if-range)#switchport access vlan 60
HR(config-if-range)#exit
HR(config)#int vlan 88
HR(config-if)#ip add 172.16.88.251 255.255.255.0
HR(config-if)#no shutdown
HR(config-if)#exit
HR(config)#ip default-gateway 172.16.88.254
HR(config)#vtp domain School
HR(config)#int f0/24
HR(config-if)#switchport mode trunk

cuando te sale el CLI bloqueado como entro?