CCNA 1 Chapter 1 Exam Answers
-
Which device performs the function of determining the path that messages should take through internetworks?
- a router*
- a firewall
- a web server
- a DSL modem
-
Fill in the blank.
A convergednetwork is capable of delivering voice, video, text, and graphics over the same communication channels.
-
Fill in the blank.
The acronym byod refers to the policy that allows employees to use their personal devices in the business office to access the network and other resources.
-
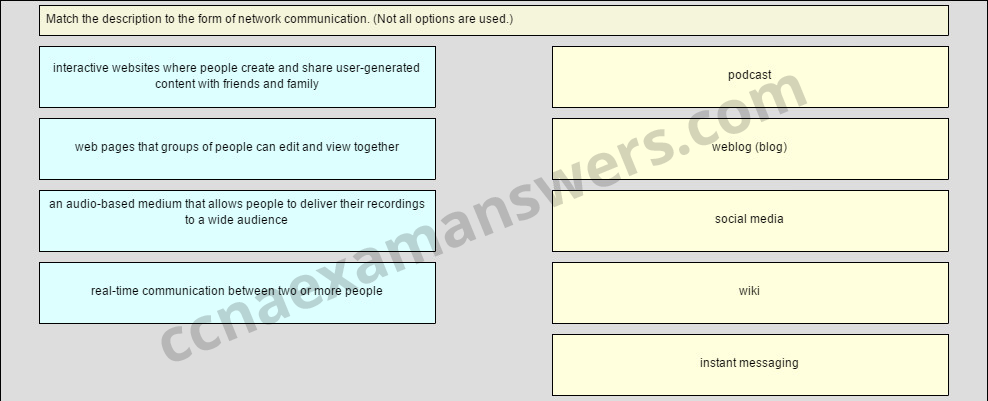
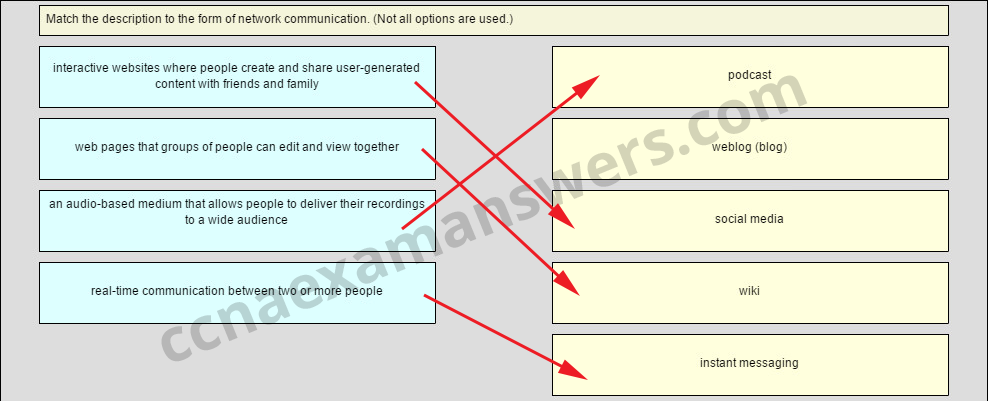
Match the description to the form of network communication. (Not all options are used.)
- Question
- Answer
- Question
-
What two criteria are used to help select a network medium from various network media? (Choose two.)
- the types of data that need to be prioritized
- the cost of the end devices utilized in the network
- the distance the selected medium can successfully carry a signal*
- the number of intermediary devices installed in the network
- the environment where the selected medium is to be installed*
-
What are two functions of end devices on a network? (Choose two.)
- They originate the data that flows through the network.*
- They direct data over alternate paths in the event of link failures.
- They filter the flow of data to enhance security.
- They are the interface between humans and the communication network.*
- They provide the channel over which the network message travels.
-
Which area of the network would a college IT staff most likely have to redesign as a direct result of many students bringing their own tablets and smartphones to school to access school resources?
- extranet
- intranet
- wired LAN
- wireless LAN*
- wireless WAN
-
What type of network must a home user access in order to do online shopping?
- an intranet
- the Internet*
- an extranet
- a local area network
-
An employee at a branch office is creating a quote for a customer. In order to do this, the employee needs to access confidential pricing information from internal servers at the Head Office. What type of network would the employee access?
- an intranet*
- the Internet
- an extranet
- a local area network
-
Which two connection options provide an always-on, high-bandwidth Internet connection to computers in a home office? (Choose two.)
- cellular
- DSL*
- satellite
- cable*
- dial-up telephone
-
Which two Internet connection options do not require that physical cables be run to the building? (Choose two.)
- DSL
- cellular *
- satellite*
- dialup
- dedicated leased line
-
Which term describes the state of a network when the demand on the network resources exceeds the available capacity?
- convergence
- congestion*
- optimization
- synchronization
-
What type of network traffic requires QoS?
- on-line purchasing
- video conferencing*
- wiki
-
Which expression accurately defines the term bandwidth?
- a method of limiting the impact of a hardware or software failure on the network
- a measure of the data carrying capacity of the media*
- a state where the demand on the network resources exceeds the available capacity
- a set of techniques to manage the utilization of network resources
-
A network administrator is implementing a policy that requires strong, complex passwords. Which data protection goal does this policy support?
- data integrity
- data quality
- data confidentiality*
- data redundancy
-
Which statement describes a characteristic of cloud computing?
- A business can connect directly to the Internet without the use of an ISP.
- Applications can be accessed over the Internet by individual users or businesses using any device, anywhere in the world.*
- Devices can connect to the Internet through existing electrical wiring.
- Investment in new infrastructure is required in order to access the cloud.
-
Which statement describes the use of powerline networking technology?
- New “smart” electrical cabling is used to extend an existing home LAN.
- A home LAN is installed without the use of physical cabling.
- A device connects to an existing home LAN using an adapter and an existing electrical outlet.*
- Wireless access points use powerline adapters to distribute data through the home LAN.
-
What security violation would cause the most amount of damage to the life of a home user?
- denial of service to your email server
- replication of worms and viruses in your computer
- capturing of personal data that leads to identity theft*
- spyware that leads to spam emails
-
A company is contemplating whether to use a client/server or a peer-to-peer network. What are three characteristics of a peer-to-peer network? (Choose three.)
- better security
- easy to create*
- better device performance when acting as both client and server
- lacks centralized administration *
- less cost to implement*
- scalable
-
Which two statements describe intermediary devices? (Choose two.)
- Intermediary devices generate data content.
- Intermediary devices alter data content.
- Intermediary devices direct the path of the data. *
- Intermediary devices connect individual hosts to the network.*
- Intermediary devices initiate the encapsulation process.
-
A user is implementing security on a small office network. Which two actions would provide the minimum security requirements for this network? (Choose two.)
- implementing a firewall*
- installing a wireless network
- installing antivirus software*
- implementing an intrusion detection system
- adding a dedicated intrusion prevention device
-
What is the Internet?
- It provides connections through interconnected global networks.*
- It is a network based on Ethernet technology.
- It provides network access for mobile devices.
- It is a private network for an organization with LAN and WAN connections.
-
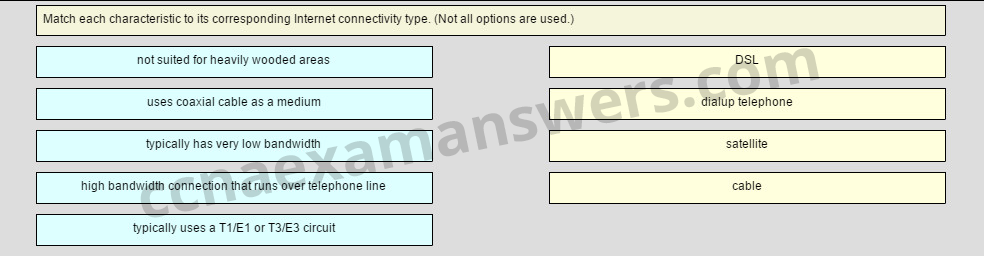
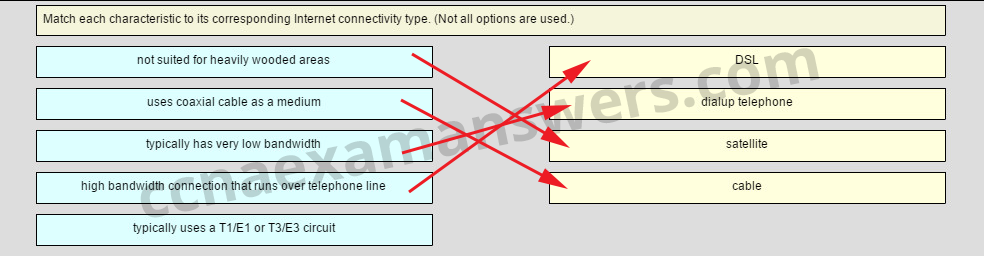
Match each characteristic to its corresponding Internet connectivity type. (Not all options are used.)
- Question
- Answer
- Question
-
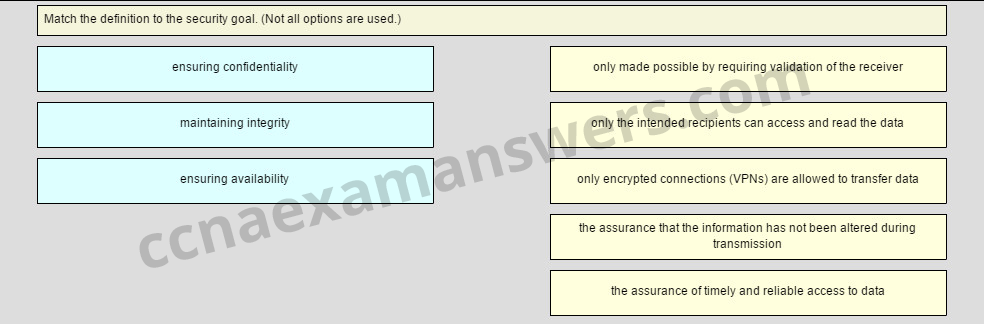
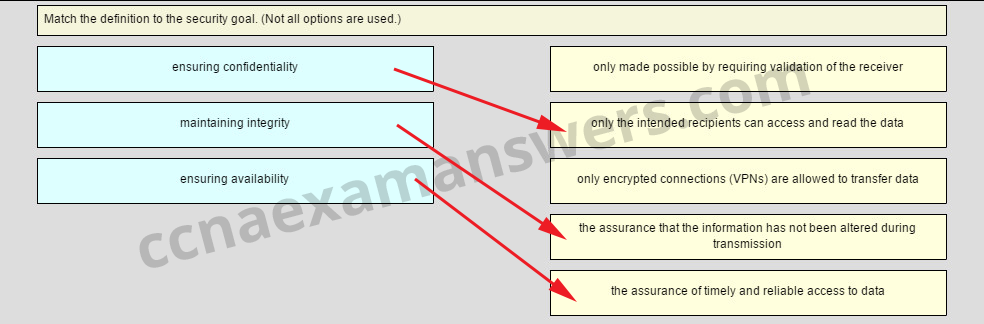
Match the definition to the security goal. (Not all options are used.)
- Question
- Answer
- Question
