Lab – Basic Switch Configuration
Topology
Addressing Table
| Device | Interface | IP Address / Prefix |
|---|---|---|
| S1 | VLAN 99 | 192.168.1.2 /24 |
| 2001:db8:acad::2 /64 | ||
| fe80::2 | ||
| PC-A | NIC | 192.168.1.10 /24 |
| 2001:db8:acad:3 /64 | ||
| fe80::3 |
Objectives
Part 1: Cable the Network and Verify the Default Switch Configuration
Part 2: Configure Basic Network Device Settings
• Configure basic switch settings.
• Configure the PC IP address.
Part 3: Verify and Test Network Connectivity
• Display device configuration.
• Test end-to-end connectivity with ping.
• Test remote management capabilities with Telnet.
Part 4: Manage the MAC Address Table
• Record the MAC address of the host.
• Determine the MAC addresses that the switch has learned.
• List the show mac address-table command options.
• Set up a static MAC address.
Background / Scenario
Cisco switches can be configured with a special IP address known as the switch virtual interface (SVI). The SVI, or management address, can be used for remote access to the switch to display or configure settings. If the VLAN 1 SVI is assigned an IP address, by default all ports in VLAN 1 have access to the SVI IP address.
In this lab, you will build a simple topology using Ethernet LAN cabling and access a Cisco switch using the console and remote access methods. You will examine default switch configurations before configuring basic switch settings. These basic switch settings include device name, interface description, local passwords, message of the day (MOTD) banner, IP addressing, and static MAC address. You will also demonstrate the use of a management IP address for remote switch management. The topology consists of one switch and one host using only Ethernet and console ports.
Note: The switches used are Cisco Catalyst 2960s with Cisco IOS Release 15.2(2) (lanbasek9 image). Other switches and Cisco IOS versions can be used. Depending on the model and Cisco IOS version, the commands available and output produced might vary from what is shown in the labs.
Note: Make sure that the switches have been erased and have no startup configurations. If you are unsure, contact your instructor. Refer to Appendix A for the procedures to initialize and reload a switch.
The default bias template used by the Switch Database Manager (SDM) does not provide IPv6 address capabilities. Verify that SDM is using either the dual-ipv4-and-ipv6 template or the lanbase-routing template. The new template will be used after reboot even if the configuration is not saved.
S1# show sdm prefer
Use the following commands to assign the dual-ipv4-and-ipv6 template as the default SDM template.
S1# configure terminal S1(config)# sdm prefer dual-ipv4-and-ipv6 default S1(config)# end S1# reload
Required Resources
• 1 Switch (Cisco 2960 with Cisco IOS Release 15.2(2) lanbasek9 image or comparable)
• 1 PC (Windows with terminal emulation program, such as Tera Term)
• 1 Console cable to configure the Cisco IOS device via the console port
• 1 Ethernet cable as shown in the topology
Part 1: Cable the Network and Verify the Default Switch Configuration
In Part 1, you will set up the network topology and verify default switch settings.
Step 1: Cable the network as shown in the topology.
a. Connect the console cable as shown in the topology. Do not connect the PC-A Ethernet cable at this time.
Note: If you are using Netlab, shut down F0/6 on S1. This has the same effect as not connecting PC-A to S1.
b. Connect to the switch from PC-A using Tera Term or other terminal emulation program.
Why must you use a console connection to initially configure the switch? Why is it not possible to connect to the switch via Telnet or SSH?
Step 2: Verify the default switch configuration.
In this step, you will examine the default switch settings, such as current switch configuration, IOS information, interface properties, VLAN information, and flash memory.
You can access all the switch IOS commands in privileged EXEC mode. Access to privileged EXEC mode should be restricted by password protection to prevent unauthorized use because it provides direct access to global configuration mode and commands used to configure operating parameters. You will set passwords later in this lab.
The privileged EXEC mode command set includes those commands contained in user EXEC mode, as well as the configure command through which access to the remaining command modes is gained. Use the enable command to enter privileged EXEC mode.
a. Assuming the switch had no configuration file stored in nonvolatile random-access memory (NVRAM), A console connection using Tera Term or other terminal emulation program will place you at the user EXEC mode prompt on the switch with a prompt of Switch>. Use the enable command to enter privileged EXEC mode.
Notice that the prompt changed in the configuration to reflect privileged EXEC mode.
Verify that there is a clean default configuration file on the switch by issuing the show running-config privileged EXEC mode command. If a configuration file was previously saved, it must be removed.
Depending on the switch model and IOS version, your configuration may look slightly different. However, there should be no configured passwords or IP address. If your switch does not have a default configuration, erase and reload the switch.
Note: Appendix A details the steps to initialize and reload a switch.
b. Examine the current running configuration file.
Switch# show running-config
How many FastEthernet interfaces does a 2960 switch have?
How many Gigabit Ethernet interfaces does a 2960 switch have?
What is the range of values shown for the vty lines?
c. Examine the startup configuration file in NVRAM.
Switch# show startup-config startup-config is not present
Why does this message appear?
d. Examine the characteristics of the SVI for VLAN 1.
Switch# show interface vlan1
Is there an IP address assigned to VLAN 1?
What is the MAC address of this SVI? Answers will vary.
Is this interface up?
no shutdown command configured by default on VLAN 1, but VLAN 1 won’t reach the up/up state until a port is assigned to it and this port is also up. If there is no port in the up state in VLAN 1, then the VLAN 1 interface will be up, line protocol down. By default, all ports are assigned initially to VLAN 1.e. Examine the IP properties of the SVI VLAN 1.
Switch# show ip interface vlan1
What output do you see?
Internet protocol processing disabled
f. Connect an Ethernet cable from PC-A to port 6 on the switch and examine the IP properties of the SVI VLAN 1. Allow time for the switch and PC to negotiate duplex and speed parameters.
Note: If you are using Netlab, enable interface F0/6 on S1.
What output do you see?
Internet protocol processing disabled
g. Examine the Cisco IOS version information of the switch.
Switch# show version
What is the Cisco IOS version that the switch is running?
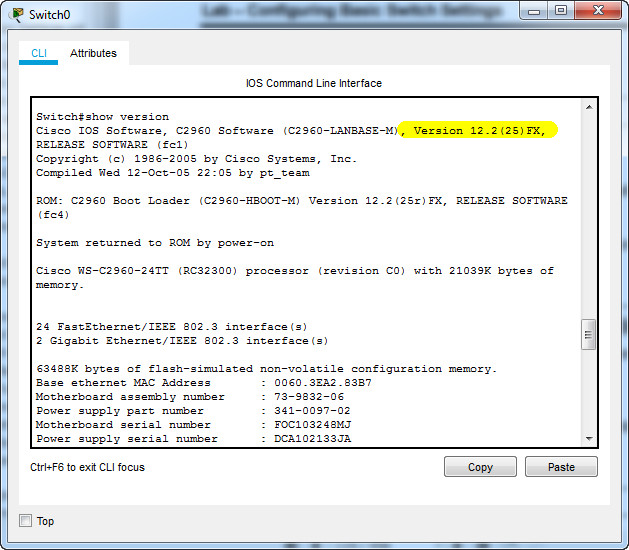
What is the system image filename?
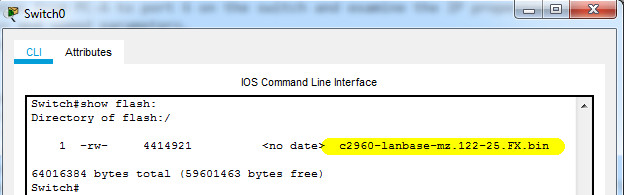
Switch#show flash:
What is the base MAC address of this switch?
h. Examine the default properties of the FastEthernet interface used by PC-A.
Switch# show interface f0/6
Is the interface up or down?
What event would make an interface go up?
What is the MAC address of the interface?
What is the speed and duplex setting of the interface?
i. Examine the default VLAN settings of the switch.
Switch# show vlan
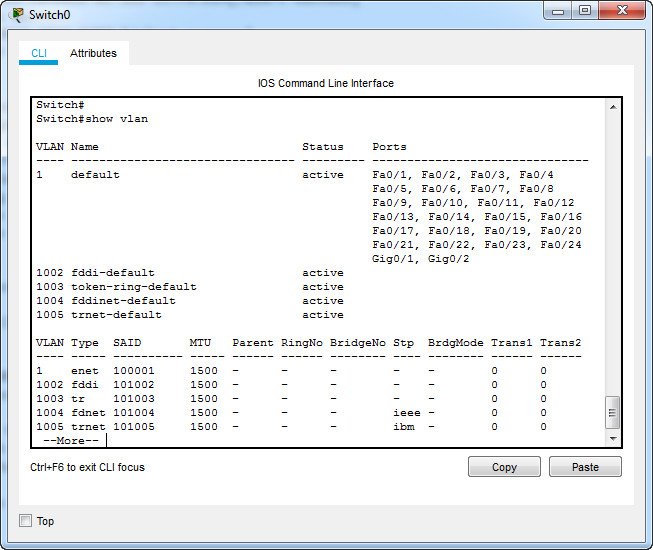
What is the default name of VLAN 1?
Which ports are in VLAN 1?
Is VLAN 1 active?
What type of VLAN is the default VLAN?
j. Examine flash memory.
Issue one of the following commands to examine the contents of the flash directory.
Switch# show flash: Switch# dir flash:
Files have a file extension, such as .bin, at the end of the filename. Directories do not have a file extension.
What is the filename of the Cisco IOS image?
Part 2: Configure Basic Network Device Settings
In Part 2, you will configure basic settings for the switch and PC.
Step 1: Configure basic switch settings.
a. Copy the following basic configuration and paste it into S1 while in global configuration mode.
no ip domain-lookup hostname S1 service password-encryption enable secret class banner motd # Unauthorized access is strictly prohibited. #
b. Set the SVI IP address of the switch. This allows remote management of the switch.
Before you can manage S1 remotely from PC-A, you must assign the switch an IP address. The default configuration on the switch is to have the management of the switch controlled through VLAN 1.
However, a best practice for basic switch configuration is to change the management VLAN to a VLAN other than VLAN 1.
For management purposes, use VLAN 99. The selection of VLAN 99 is arbitrary and in no way implies that you should always use VLAN 99.
First, create the new VLAN 99 on the switch. Then set the IP address of the switch to 192.168.1.2 with a subnet mask of 255.255.255.0 on the internal virtual interface VLAN 99. IPv6 address can also be configured on the SVI interface. Use the IPv6 addresses listed in the Addressing Table.
Notice that the VLAN 99 interface is in the down state even though you entered the no shutdown command. The interface is currently down because no switch ports are assigned to VLAN 99.
S1#configure terminal Enter configuration commands, one per line. End with CNTL/Z. S1(config)#vlan 99 S1(config-vlan)#exit S1(config)#interface vlan99 S1(config-if)# %LINK-5-CHANGED: Interface Vlan99, changed state to up S1(config-if)#ip address 192.168.1.2 255.255.255.0 S1(config-if)#no shutdown S1(config-if)#exit
c. Assign all user ports to VLAN 99.
S1(config)#interface range f0/1-24, g0/1-2 S1(config-if-range)#switchport access vlan 99 S1(config-if-range)# %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan1, changed state to down %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan99, changed state to up S1(config-if-range)#exit
To establish connectivity between the host and the switch, the ports used by the host must be in the same VLAN as the switch. Notice in the above output that the VLAN 1 interface goes down because none of the ports are assigned to VLAN 1. After a few seconds, VLAN 99 comes up because at least one active port (F0/6 with PC-A attached) is now assigned to VLAN 99.
d. Issue the show vlan brief command to verify that all ports are in VLAN 99.
S1#show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active
99 VLAN0099 active Fa0/1, Fa0/2, Fa0/3, Fa0/4
Fa0/5, Fa0/6, Fa0/7, Fa0/8
Fa0/9, Fa0/10, Fa0/11, Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gig0/1, Gig0/2
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
e. Configure the default gateway for S1. If no default gateway is set, the switch cannot be managed from a remote network that is more than one router away. Although this activity does not include an external IP gateway, assume that you will eventually connect the LAN to a router for external access. Assuming that the LAN interface on the router is 192.168.1.1, set the default gateway for the switch.
S1(config)#ip default-gateway 192.168.1.1
f. Console port access should also be restricted with a password. Use cisco as the console login password in this activity. The default configuration is to allow all console connections with no password needed. To prevent console messages from interrupting commands, use the logging synchronous option.
S1(config)#line console 0 S1(config-line)#password cisco S1(config-line)#login S1(config-line)#loggin synchronous S1(config-line)#exit S1(config)#
g. Configure the virtual terminal (vty) lines for the switch to allow telnet access. If you do not configure a vty password, you will not be able to telnet to the switch.
S1(config)#line vty 0 15 S1(config-line)#password cisco S1(config-line)#login S1(config-line)#end
Why is the login command required?
Step 2: Configure an IP address on PC-A.
Assign the IP address and subnet mask to the PC as shown in the Addressing Table. An abbreviated version of the procedure is described here. A default gateway is not required for this topology; however, you can enter 192.168.1.1 and fe80::1 to simulate a router attached to S1.
1) Navigate to the Control Panel.
2) In the Category view, select View network status and tasks.
3) Click Change adapter settings on the left panel.
4) Right-click an Ethernet interface, and choose Properties.
5) Choose Internet Protocol Version 4 (TCP/IPv4) and click Properties.
6) Click the Use the following IP address radio button and enter the IP address and subnet mask and
click OK.
7) Select Internet Protocol Version 6 (TCP/IPv6) and click Properties.
8) Click the Use the following IPv6 address radio button and enter the IPv6 address and prefix and
click OK to continue
9) Click OK to exit the Properties window.
Part 3: Verify and Test Network Connectivity
In Part 3, you will verify and document the switch configuration, test end-to-end connectivity between PC-A and S1, and test the switch’s remote management capability.
Step 1: Display the switch configuration.
Use the console connection on PC-A to display and verify the switch configuration. The show run command displays the entire running configuration, one page at a time. Use the spacebar to advance paging.
a. A sample configuration is shown here. The settings you configured are highlighted in yellow. The other configuration settings are IOS defaults.
S1# show run Building configuration... Current configuration : 2206 bytes ! version 15.2 no service pad service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname S1 ! boot-start-marker boot-end-marker ! enable secret 5 $1$mtvC$6NC.1VKr3p6bj7YGE.jNg0 ! no aaa new-model system mtu routing 1500 ! ! no ip domain-lookup !
b. Verify the management VLAN 99 settings.
S1#show interface vlan 99
Vlan99 is up, line protocol is up
Hardware is CPU Interface, address is 0060.3ea2.8301 (bia 0060.3ea2.8301)
Internet address is 192.168.1.2/24
MTU 1500 bytes, BW 100000 Kbit, DLY 1000000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
ARP type: ARPA, ARP Timeout 04:00:00
Last input 21:40:21, output never, output hang never
Last clearing of "show interface" counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
1682 packets input, 530955 bytes, 0 no buffer
Received 0 broadcasts (0 IP multicast)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
563859 packets output, 0 bytes, 0 underruns
0 output errors, 23 interface resets
0 output buffer failures, 0 output buffers swapped out
S1#
What is the bandwidth on this interface?
What is the VLAN 99 state?
What is the line protocol state?
Step 2: Test end-to-end connectivity with ping.
a. From the command prompt on PC-A, ping the address of PC-A first.
C:\> ping 192.168.1.10
b. From the command prompt on PC-A, ping the SVI management address of S1.
C:\> ping 192.168.1.2
Because PC-A needs to resolve the MAC address of S1 through ARP, the first packet may time out. If ping results continue to be unsuccessful, troubleshoot the basic device configurations. Check both the physical cabling and logical addressing.
Step 3: Test and verify remote management of S1.
You will now use Telnet to remotely access the switch. In this lab, PC-A and S1 reside side by side. In a production network, the switch could be in a wiring closet on the top floor while your management PC is located on the ground floor. In this step, you will use Telnet to remotely access switch S1 using its SVI management address. Telnet is not a secure protocol; however, you will use it to test remote access. With Telnet, all information, including passwords and commands, are sent across the session in plain text. In subsequent labs, you will use SSH to remotely access network devices.
a. Open Tera Term or other terminal emulation program with Telnet capability.
b. Select the Telnet server and provide the SVI management address to connect to S1. The password is cisco.
c. After entering the password cisco, you will be at the user EXEC mode prompt. Access privileged EXEC mode using the enable command and providing the secret password class.
d. Save the configuration.
e. Type exit to end the Telnet session.
C:\>telnet 192.168.1.2 Trying 192.168.1.2 ...Open User Access Verification Password: S1>enable Password: Password: S1# S1#copy running-config startup-config Destination filename [startup-config]? Building configuration... [OK] S1#exit [Connection to 192.168.1.2 closed by foreign host] C:\>
Part 4: Manage the MAC Address Table
In Part 4, you will determine the MAC addresses that the switch has learned, set up a static MAC address on one interface of the switch, and then remove the static MAC address from that interface.
Step 1: Record the MAC address of the host.
Open a command prompt on PC-A and issue the ipconfig /all command to determine and record the Layer 2 (physical) addresses of the NIC.
C:\>ipconfig /all FastEthernet0 Connection:(default port) Connection-specific DNS Suffix..: Physical Address................: 0009.7C28.ED5E Link-local IPv6 Address.........: FE80::3 IP Address......................: 192.168.1.10 Subnet Mask.....................: 255.255.255.0 Default Gateway.................: 0.0.0.0 DNS Servers.....................: 0.0.0.0 DHCP Servers....................: 0.0.0.0 DHCPv6 Client DUID..............: 00-01-00-01-69-B1-D6-1E-00-09-7C-28-ED-5E
Step 2: Determine the MAC addresses that the switch has learned.
Display the MAC addresses using the show mac address-table command.
S1#show mac-address-table
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
99 0009.7c28.ed5e DYNAMIC Fa0/6
S1#
How many dynamic addresses are there?
How many MAC addresses are there in total?
Does the dynamic MAC address match the MAC address of PC-A?
Step 3: List the show mac address-table options.
a. Display the MAC address table options.
S1# show mac address-table ?
How many options are available for the show mac address-table command?
b. Issue the
show mac address-table dynamic command to display only the MAC addresses that were learned dynamically.
S1# show mac address-table dynamic
How many dynamic addresses are there?
c. View the MAC address entry for PC-A. The MAC address formatting for the command is xxxx.xxxx.xxxx.
S1# show mac address-table address
Step 4: Set up a static MAC address.
a. Clear the MAC address table.
To remove the existing MAC addresses, use the clear mac address-table dynamic command in privileged EXEC mode.
S1# clear mac address-table dynamic
b. Verify that the MAC address table was cleared.
S1# show mac address-table
How many static MAC addresses are there?
Instructor Note: The first 20 static addresses in the MAC address table are built-in.
How many dynamic addresses are there?
c. Examine the MAC table again.
More than likely, an application running on your PC has already sent a frame out the NIC to S1. Look at the MAC address table again in privileged EXEC mode to see if S1 has relearned the MAC address of PC-A.
S1# show mac address-table
How many dynamic addresses are there?
Why did this change from the last display?
If S1 has not yet relearned the MAC address for PC-A, ping the VLAN 99 IP address of the switch from PC-A, and then repeat the
show mac address-table command.d. Set up a static MAC address.
To specify which ports a host can connect to, one option is to create a static mapping of the host MAC address to a port.
Set up a static MAC address on F0/6 using the address that was recorded for PC-A in Part 4, Step 1. The MAC address 0050.56BE.6C89 is used as an example only. You must use the MAC address of PC-A, which is different than the one given here as an example.
S1(config)# mac address-table static 0050.56BE.6C89 vlan 99 interface fastethernet 0/6
e. Verify the MAC address table entries.
S1# show mac address-table
How many total MAC addresses are there?
How many static addresses are there?
f. Remove the static MAC entry. Enter global configuration mode and remove the command by putting a no in front of the command string.
Note: The MAC address 0050.56BE.6C89 is used in the example only. Use the MAC address for PC-A.
S1(config)# no mac address-table static 0050.56BE.6C89 vlan 99 interface fastethernet 0/6
g. Verify that the static MAC address has been cleared.
S1# show mac address-table
How many total static MAC addresses are there?
Reflection Questions
1. Why should you configure the vty password for the switch?
2. Why change the default VLAN 1 to a different VLAN number?
3. How can you prevent passwords from being sent in plain text?
service password-encryption command.4. Why configure a static MAC address on a port interface?
Appendix A: Initialize and Reload a Switch
a. Console into the switch and enter privileged EXEC mode.
Switch> enable Switch#
b. Use the show flash command to determine if any VLANs have been created on the switch.
Switch# show flash Directory of flash:/ 2 -rwx 1919 Mar 1 1993 00:06:33 +00:00 private-config.text 3 -rwx 1632 Mar 1 1993 00:06:33 +00:00 config.text 4 -rwx 13336 Mar 1 1993 00:06:33 +00:00 multiple-fs 5 -rwx 11607161 Mar 1 1993 02:37:06 +00:00 c2960-lanbasek9-mz.150-2.SE.bin 6 -rwx 616 Mar 1 1993 00:07:13 +00:00 vlan.dat 32514048 bytes total (20886528 bytes free)
c. If the vlan.dat file was found in flash, then delete this file.
Switch# delete vlan.dat Delete filename [vlan.dat]?
d. You are prompted to verify the filename. If you have entered the name correctly, press Enter; otherwise, you can change the filename.
You are prompted to confirm deletion of this file. Press Enter to confirm.
Delete flash:/vlan.dat? [confirm] Switch#
e. Use the erase startup-config command to erase the startup configuration file from NVRAM. You are prompted to remove the configuration file. Press Enter to confirm.
Switch# erase startup-config Erasing the nvram filesystem will remove all configuration files! Continue? [confirm] [OK] Erase of nvram: complete Switch#
f. Reload the switch to remove any old configuration information from memory. You will then receive a prompt to confirm reloading of the switch. Press Enter to proceed.
Switch# reload Proceed with reload? [confirm]
Note: You may receive a prompt to save the running configuration prior to reloading the switch. Respond by typing no and press Enter.
System configuration has been modified. Save? [yes/no]: no
g. After the switch reloads, you should see a prompt to enter the initial configuration dialog. Respond by entering no at the prompt and press Enter.
Would you like to enter the initial configuration dialog? [yes/no]: no Switch>
Device Configs
Switch S1
S1#sh run Building configuration... Current configuration : 2359 bytes ! version 15.0 no service pad service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname S1 ! boot-start-marker boot-end-marker ! enable secret 4 06YFDUHH61wAE/kLkDq9BGho1QM5EnRtoyr8cHAUg.2 ! no aaa new-model system mtu routing 1500 ! ! no ip domain-lookup ! spanning-tree mode pvst spanning-tree extend system-id ! vlan internal allocation policy ascending ! !interface FastEthernet0/1 switchport access vlan 99 ! interface FastEthernet0/2 switchport access vlan 99 ! interface FastEthernet0/3 switchport access vlan 99 ! interface FastEthernet0/4 switchport access vlan 99 ! interface FastEthernet0/5 switchport access vlan 99 ! interface FastEthernet0/6 switchport access vlan 99 ! interface FastEthernet0/7 switchport access vlan 99 ! interface FastEthernet0/8 switchport access vlan 99 ! interface FastEthernet0/9 switchport access vlan 99 ! interface FastEthernet0/10 switchport access vlan 99 ! interface FastEthernet0/11 switchport access vlan 99 ! interface FastEthernet0/12 switchport access vlan 99 ! interface FastEthernet0/13 switchport access vlan 99 ! interface FastEthernet0/14 switchport access vlan 99 ! interface FastEthernet0/15 switchport access vlan 99 ! interface FastEthernet0/16 switchport access vlan 99 ! interface FastEthernet0/17 switchport access vlan 99 ! interface FastEthernet0/18 switchport access vlan 99 ! interface FastEthernet0/19 switchport access vlan 99 ! interface FastEthernet0/20 switchport access vlan 99 ! interface FastEthernet0/21 switchport access vlan 99 ! interface FastEthernet0/22 switchport access vlan 99 ! interface FastEthernet0/23 switchport access vlan 99 ! interface FastEthernet0/24 switchport access vlan 99 ! interface GigabitEthernet0/1 switchport access vlan 99 ! interface GigabitEthernet0/2 switchport access vlan 99 ! interface Vlan1 no ip address ! interface Vlan99 ip address 192.168.1.2 255.255.255.0 ! ip default-gateway 192.168.1.1 ip http server ip http secure-server ! ! banner motd ^C Unauthorized access is strictly prohibited. ^C ! line con 0 password 7 0822455D0A16 logging synchronous login line vty 0 4 password 7 01100F175804 login line vty 5 15 password 7 01100F175804 login ! end login line vty 0 4 password 7 01100F175804 login line vty 5 15 password 7 01100F175804 login ! end
Download PDF & Packet Tracer file:
[sociallocker id=”54558″][wpdm_package id=’49218′][/sociallocker]

Thank you very much. This is really good. Great job
How can this be downloaded? Any pdfs?