CCNA 3 OSPF Practice Skills Assessment
OSPF Practice Skills Assessment – Packet Tracer
CCNA Routing and Switching – Scaling Networks
[tabs][tab title=”Form 1″]
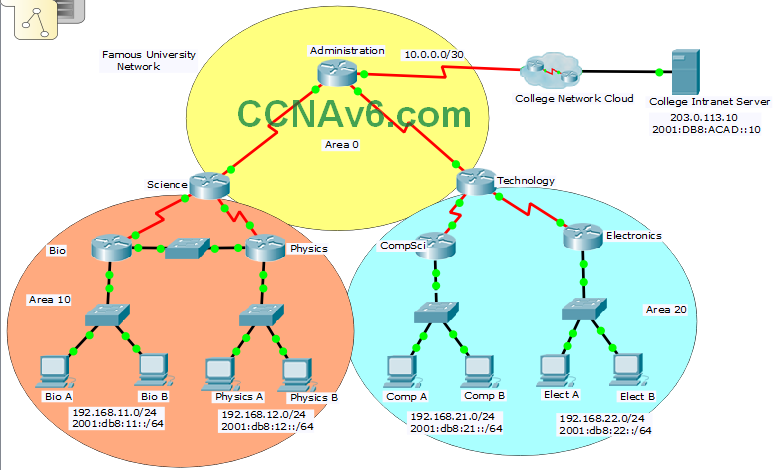
Network Diagram:
Diagram uses slightly different naming convention (Hostnames and vlan names) , same topology)
A few things to keep in mind while completing this activity:
- Do not use the browser Backbutton or close or reload any exam windows during the exam.
- Do not close Packet Tracer when you are done. It will close automatically.
- Click the Submit Assessmentbutton in the browser window to submit your work.
Introduction
In this practice skills assessment, you will configure the Famous University network with OSPF routing. The network is configured with both IPv4 and IPv6 on all devices. This will allow you to implement routing in both OSPFv2 and OSPFv3. In addition, you will configure both versions of OSPF in multiple areas. For a full list of tasks, see below.
You are not required to configure the following:
- The network switches
- The network hosts
- The College Intranet Server
- The College Network Cloud
All IOS device configurations should be completed from a direct terminal connection to the device console.
You will practice and be assessed on the following skills:
- Configuration of IPv4 and IPv6 default routes
- Configuration of OSPFv2 in a single area
- Configuration of OSPFv2 in multiple areas
- Configuration of OSPFv3 in a single area
- Configuration of OSPFv3 in multiple areas
- Customization of OSPFv2 and OSPFv3 settings
- Interface Bandwidth
- OSPF Priority
- OSPF timer settings
- Passive interfaces
You will configure specific devices as follows:
Router Administration:
- IPv4 and IPv6 default route configuration
- OSPFv2 and OSPFv3 Area 0 configuration
- Interface bandwidth configuration
- OSPFv2 and OSPFv3 router ID configuration
- Distribution of default routes
- Auto-cost reference bandwidth configuration for OSPFv2 and OSPFv3
Router Science:
- OSPFv2 and OSPFv3 Area 0 configuration
- OSPFv2 and OSPFv3 Area 10 configuration
- Interface bandwidth configuration
- OSPFv2 and OSPFv3 router ID configuration
- Auto-cost reference bandwidth configuration for OSPFv2 and OSPFv3
Router Bio:
- OSPFv2 and OSPFv3 Area 10 configuration
- OSPFv2 and OSPFv3 router ID configuration
- Auto-cost reference bandwidth configuration for OSPFv2 and OSPFv3
- OSPFv2 and OSPFv3 interface priority configuration
- OSPFv2 and OSPFv3 hello and dead timer configuration
- OSPFv2 and OSPFv3 passive interface configuration
Router Physics
- OSPFv2 and OSPFv3 Area 10 configuration
- OSPFv2 and OSPFv3 router ID configuration
- Auto-cost reference bandwidth configuration for OSPFv2 and OSPFv3
- OSPFv2 and OSPFv3 interface priority configuration
- OSPFv2 and OSPFv3 hello and dead timer configuration
- OSPFv2 and OSPFv3 passive interface configuration
Router Technology:
- OSPFv2 and OSPFv3 Area 0 configuration
- OSPFv2 and OSPFv3 Area 20 configuration
- Interface bandwidth configuration
- OSPFv2 and OSPFv3 router ID configuration
- Auto-cost reference bandwidth configuration for OSPFv2 and OSPFv3
Router CompSci:
- OSPFv2 and OSPFv3 Area 20 configuration
- OSPFv2 and OSPFv3 router ID configuration
- Auto-cost reference bandwidth configuration for OSPFv2 and OSPFv3
- OSPFv2 and OSPFv3 interface priority configuration
- OSPFv2 and OSPFv3 hello and dead timer configuration
- OSPFv2 and OSPFv3 passive interface configuration
Router Electronics:
- OSPFv2 and OSPFv3 Area 20 configuration
- OSPFv2 and OSPFv3 router ID configuration
- Auto-cost reference bandwidth configuration for OSPFv2 and OSPFv3
- OSPFv2 and OSPFv3 interface priority configuration
- OSPFv2 and OSPFv3 hello and dead timer configuration
- OSPFv2 and OSPFv3 passive interface configuration
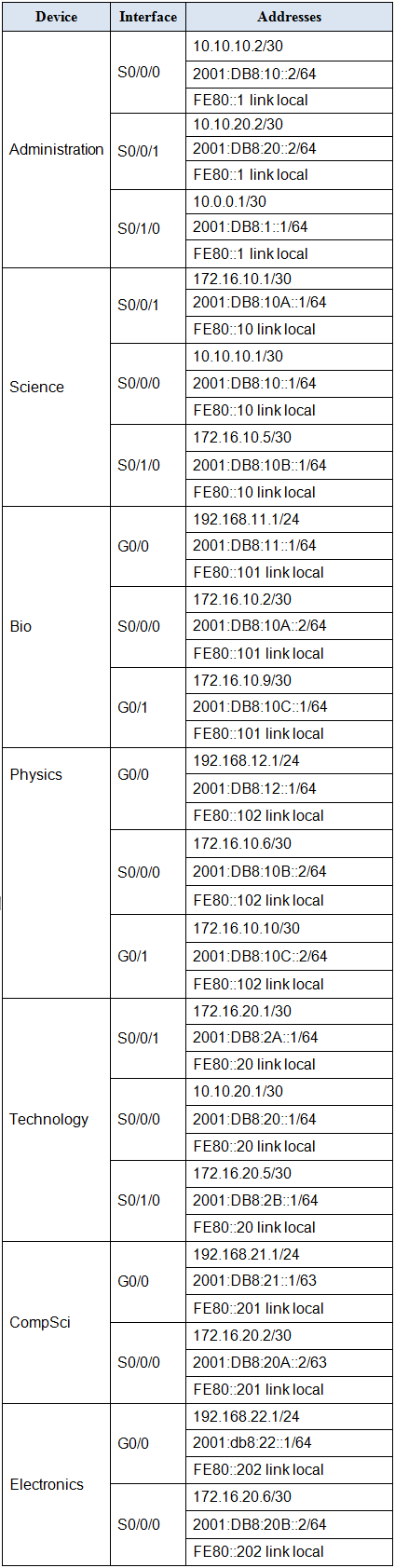
Addressing Table
Use the following addresses to configure the network. Some addresses are preconfigured on devices that you are not required to configure, and are provided for reference purposes only.
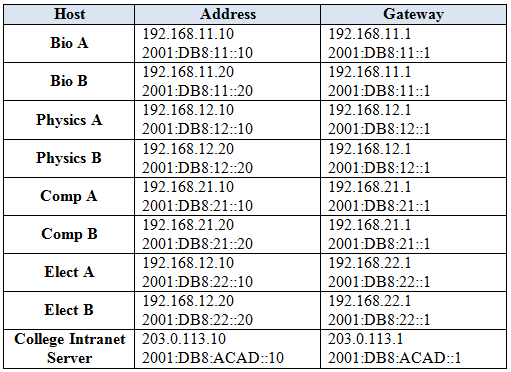
Host Address Table
The addresses of the PC and server hosts are provided for connectivity testing purposes. All addressing is preconfigured.
Instructions
Step1: Configure default static routes on the Administration router.
Configure IPv4 and IPv6 default static routes on Administration. Use the exit interface value in your configuration.
Step 2: Configure single-area OSPFv2
On the Administration, Science, and Technology routers, configure single-area OSPFv2 in Area 0.
a. Use a process ID of 10 for all OSPFv2 processes.
b. Activate routing for the appropriate networks. Use inverse masks that specify only addresses within the networks.
c. Specify a bandwidth value that matches the clock speed of the interfaces of Administration for interfaces of alldevices that are configured in Area 0.
d. Set the router IDs as follows:
Administration: 10.20.0.0
Science: 10.0.0.0
Technology: 20.0.0.0
Step 3: Configure single-area OSPFv3.
On the Administration, Science, and Technology routers configure single-area OSPFv3 in Area 0.
a. Use a process ID of 10 for all OSPFv3 processes.
b. Activate routing for the appropriate networks.
c. Set the router IDs as follows:
Administration: 10.20.0.0
Science: 10.0.0.0
Technology: 20.0.0.0
Step 4: Configure OSPFv2 in multiple areas.
Configure the routers that have all interfaces in Areas 10 and 20 with OSPFv2.
a. Use a process ID of 10 for all OSPF processes.
b. Activate routing for the appropriate networks. Use inverse masks that specify only addresses within the networks. After this step is completed, hosts on all LANs should be able to communicate with each other over IPv4.
c. Set the router IDs as follows:
Bio: 10.1.1.1
Physics: 10.2.2.2
CompSci: 20.1.1.1
Electronics: 20.2.2.2
Step 5: Configure OSPFv3 in multiple areas.
Configure the routers that have all interfaces in Areas 10 and 20 with OSPFv3.
a. Enable the routers to route IPv6.
b. Use a process ID of 10 for all OSPF processes.
c. Activate routing for the appropriate networks. After this step is completed, hosts on all LANs should be able to communicate with each other over IPv6.
d. Set the router IDs as follows:
Bio: 10.1.1.1
Physics: 10.2.2.2
CompSci: 20.1.1.1
Electronics: 20.2.2.2
Step 6: Customize OSPFv2.
Customize OSPFv2 operation as follows:
a. For the multiaccess network connected between the Bioand Physics routers, configure priorities so that Bio will become the DR and Physics will be the BDR. Use priority values of 255 and 200.
b. Configure the interfaces on all routers that are attached to LANs with hosts to notsend OSPFv2 traffic into the LAN.
c. Enable all routers to automatically and accurately calculate costs for routes that include 1Gbps Ethernet networks by changing the reference bandwidth.
d. Configure OSPFv2 so that the default routes that are configured on Administrationare automatically distributed to all routers in the network.
e. Adjust the OSPFv2 timers on the Ethernet link between Bioand Physics as follows:
Hello: 5 seconds
Dead: 20 seconds
Step 7: Customize OSPFv3.
Customize OSPFv3 operation as follows:
a. For the multiaccess network connected between the Bioand Physics routers configure priorities so that Bio will become the DR and Physics will be the BDR. Use priority values of 255 and 200.
b. Configure the interfaces on all routers that are attached to LANs with hosts to notsend OSPFv3 traffic into the LAN.
c. Enable all routers to automatically and accurately calculate costs for routes that include 1Gbps Ethernet networks by changing the reference bandwidth.
d. Configure OSPFv3 so that the default routes that are configured on Administrationare automatically distributed to all routers in the network.
e. Explicitly configure the OSPFv3 timers on the Ethernet link between Bio and Physics as follows:
Hello: 5 seconds
Dead: 20 seconds
Answers
NOTE: Use cable Console to connect PCs and Routers
OSPF
Administration:
Administration>en Administration#conf terminal Administration(config)#ip route 0.0.0.0 0.0.0.0 s0/1/0 Administration(config)#ipv6 unicast-routing Administration(config)#ipv6 route ::/0 s0/1/0 Administration(config)#router ospf 10 Administration(config-router)#network 10.10.10.0 0.0.0.3 area 0 Administration(config-router)#network 10.10.20.0 0.0.0.3 area 0 Administration(config-router)#router-id 10.20.0.0 Administration(config-router)#do clear ip ospf process Administration(config-router)#yes Administration(config-router)#exit Administration(config)#int s0/0/0 Administration(config-if)#bandwidth 128000 Administration(config-if)#int s0/0/1 Administration(config-if)#bandwidth 128000 Administration(config-if)#exit Administration(config)#int s0/0/0 Administration(config-if)#ipv6 ospf 10 area 0 Administration(config-if)#int s0/0/1 Administration(config-if)#ipv6 ospf 10 area 0 Administration(config-if)#exit Administration(config)#Ipv6 router ospf 10 Administration(config-rtr)#router-id 10.20.0.0 Administration(config-rtr)#do clear ipv6 ospf process Administration(config-rtr)#yes Administration(config-rtr)#exit Administration(config)#router ospf 10 Administration(config-router)#auto-cost reference-bandwidth 1000 Administration(config-router)#exit Administration(config)#router ospf 10 Administration(config-router)#default-information originate Administration(config-router)#exit Administration(config)#ipv6 router ospf 10 Administration(config-rtr)#default-information originate Administration(config-rtr)#exit Administration(config)#ipv6 router ospf 10 Administration(config-router)#auto-cost reference-bandwidth 1000
Science:
Science>EN Science#conf ter Science(config)#router ospf 10 Science(config-router)#network 10.10.10.0 0.0.0.3 area 0 Science(config-router)#network 172.16.10.0 0.0.0.3 area 10 Science(config-router)#network 172.16.10.4 0.0.0.3 area 10 Science(config-router)#router-id 10.0.0.0 Science(config-router)#do clear ip ospf process Science(config-router)#yes Science(config-router)#exit Science(config)#ipv6 unicast-routing Science(config)#Int s0/0/0 Science(config-if)#Ipv6 ospf 10 area 0 Science(config-if)#exit Science(config)#Int s0/0/1 Science(config-if)#Ipv6 ospf 10 area 10 Science(config-if)#exit Science(config)#Int s0/1/0 Science(config-if)#Ipv6 ospf 10 area 10 Science(config-if)#exit Science(config)#int s0/0/0 Science(config-if)#bandwidth 128000 Science(config-if)#exit Science(config)#ipv6 router ospf 10 Science(config-rtr)#router-id 10.0.0.0 Science(config-rtr)#do clear ipv6 ospf process Science(config-rtr)#yes Science(config-rtr)#exit Science(config)#ipv6 router ospf 10 Science(config-router)#auto-cost reference-bandwidth 1000 Science(config-router)#exit Science(config)#router ospf 10 Science(config-router)#auto-cost reference-bandwidth 1000
Technology:
Technology>en Technology#conf ter Technology(config)#Router ospf 10 Technology(config-router)#network 10.10.20.0 0.0.0.3 area 0 Technology(config-router)#network 172.16.20.0 0.0.0.3 area 20 Technology(config-router)#network 172.16.20.4 0.0.0.3 area 20 Technology(config-router)#router-id 20.0.0.0 Technology(config-router)#do clear ip ospf process Technology(config-router)#yes Technology(config-router)#exit Technology(config)#ipv6 unicast-routing Technology(config)#Int s0/0/0 Technology(config-if)#Ipv6 ospf 10 area 0 Technology(config-if)#exit Technology(config)#Int s0/0/1 Technology(config-if)#Ipv6 ospf 10 area 20 Technology(config-if)#exit Technology(config)#Int s0/1/0 Technology(config-if)#Ipv6 ospf 10 area 20 Technology(config-if)#exit Technology(config)#int s0/0/0 Technology(config-if)#bandwidth 128000 Technology(config-if)#exit Technology(config)#Ipv6 router ospf 10 Technology(config-rtr)#router-id 20.0.0.0 Technology(config-rtr)#do clear ipv6 ospf process Technology(config-rtr)#yes Technology(config-rtr)#exit Technology(config)#router ospf 10 Technology(config-router)#auto-cost reference-bandwidth 1000 Technology(config-router)#exit Technology(config)#ipv6 router ospf 10 Technology(config-router)#auto-cost reference-bandwidth 1000
Bio:
Bio>en Bio#conf ter Bio(config)#router ospf 10 Bio(config-router)#network 172.16.10.0 0.0.0.3 area 10 Bio(config-router)#network 192.168.11.0 0.0.0.255 area 10 Bio(config-router)#network 172.16.10.8 0.0.0.3 area 10 Bio(config-router)#router-id 10.1.1.1 Bio(config-router)#do clear ip ospf process Bio(config-router)#yes Bio(config-router)#exit Bio(config)#ipv6 unicast-routing Bio(config)#int s0/0/0 Bio(config-if)#ipv6 ospf 10 area 10 Bio(config-if)#exit Bio(config)#int g0/0 Bio(config-if)#ipv6 ospf 10 area 10 Bio(config-if)#exit Bio(config)#int g0/1 Bio(config-if)#ipv6 ospf 10 area 10 Bio(config-if)#exit Bio(config)#ipv6 router ospf 10 Bio(config-rtr)#router-id 10.1.1.1 Bio(config-rtr)#do clear ipv6 ospf process Bio(config-rtr)#yes Bio(config-rtr)#exit Bio(config)#int g0/1 Bio(config-if)#ip ospf priority 255 Bio(config-if)#exit Bio(config)#router ospf 10 Bio(config-router)#passive-interface g0/0 Bio(config-router)#exit Bio(config)#router ospf 10 Bio(config-router)#auto-cost reference-bandwidth 1000 Bio(config-router)#exit Bio(config)#int g0/1 Bio(config-if)#ip ospf hello-interval 5 Bio(config-if)#ip ospf dead-interval 20 Bio(config-if)#exit Bio(config)#int g0/1 Bio(config-if)#ipv6 ospf priority 255 Bio(config-if)#exit Bio(config)#ipv6 router ospf 10 Bio(config-rtr)#passive-interface g0/0 Bio(config-rtr)#exit Bio(config)#int g0/1 Bio(config-if)#ipv6 ospf hello-interval 5 Bio(config-if)#ipv6 ospf dead-interval 20 Bio(config-if)#exit Bio(config)#ipv6 router ospf 10 Bio(config-router)#auto-cost reference-bandwidth 1000
Physics:
Physics>en Physics#conf ter Physics(config)#Router ospf 10 Physics(config-router)#network 172.16.10.4 0.0.0.3 area 10 Physics(config-router)#network 172.16.10.8 0.0.0.3 area 10 Physics(config-router)#network 192.168.12.0 0.0.0.255 area 10 Physics(config-router)#router-id 10.2.2.2 Physics(config-router)#do clear ip ospf process Physics(config-router)#yes Physics(config-router)#exit Physics(config)#ipv6 unicast-routing Physics(config)#int s0/0/0 Physics(config-if)#ipv6 ospf 10 area 10 Physics(config-if)#exit Physics(config)#int g0/0 Physics(config-if)#ipv6 ospf 10 area 10 Physics(config-if)#exit Physics(config)#int g0/1 Physics(config-if)#ipv6 ospf 10 area 10 Physics(config-if)#exit Physics(config)# Physics(config)#ipv6 router ospf 10 Physics(config-rtr)#router-id 10.2.2.2 Physics(config-rtr)#do clear ip ospf process Physics(config-rtr)#yes Physics(config-rtr)#exit Physics(config)#int g0/1 Physics(config-if)#ip ospf priority 200 Physics(config-if)#exit Physics(config)#router ospf 10 Physics(config-router)#passive-interface g0/0 Physics(config-router)#exit Physics(config)#router ospf 10 Physics(config-router)#auto-cost reference-bandwidth 1000 Physics(config-router)#exit Physics(config)#int g0/1 Physics(config-if)#ip ospf hello-interval 5 Physics(config-if)#ip ospf dead-interval 20 Physics(config-if)#exit Physics(config)#int g0/1 Physics(config-if)#ipv6 ospf priority 200 Physics(config-if)#exit Physics(config)#ipv6 router ospf 10 Physics(config-rtr)#passive-interface g0/0 Physics(config-rtr)#exit Physics(config)#int g0/1 Physics(config-if)#ipv6 ospf hello-interval 5 Physics(config-if)#ipv6 ospf dead-interval 20 Physics(config-if)#exit Physics(config)#ipv6 router ospf 10 Physics(config-router)#auto-cost reference-bandwidth 1000
CompSci:
CompSci>en CompSci#conf ter CompSci(config)#Router ospf 10 CompSci(config-router)#network 172.16.20.0 0.0.0.3 area 20 CompSci(config-router)#network 192.168.21.0 0.0.0.255 area 20 CompSci(config-router)#router-id 20.1.1.1 CompSci(config-router)#do clear ip ospf process CompSci(config-router)#yes CompSci(config-router)#exit CompSci(config)#ipv6 unicast-routing CompSci(config)#int s0/0/0 CompSci(config-if)#ipv6 ospf 10 area 20 CompSci(config-if)#exit CompSci(config)# CompSci(config)#int g0/0 CompSci(config-if)#ipv6 ospf 10 area 20 CompSci(config-if)#exit CompSci(config)# CompSci(config)#ipv6 router ospf 10 CompSci(config-rtr)#router-id 20.1.1.1 CompSci(config-rtr)#do clear ipv6 ospf process CompSci(config-rtr)#yes CompSci(config-rtr)#exit CompSci(config)#router ospf 10 CompSci(config-router)# CompSci(config-router)#passive-interface g0/0 CompSci(config-router)#exit CompSci(config)#ipv6 router ospf 10 CompSci(config-rtr)#passive-interface g0/0 CompSci(config-rtr)#exit CompSci(config)#router ospf 10 CompSci(config-router)#auto-cost reference-bandwidth 1000 CompSci(config-router)#exit CompSci(config)#ipv6 router ospf 10 CompSci(config-router)#auto-cost reference-bandwidth 1000
Electronics:
Electronics>en Electronics#conf ter Electronics(config)#Router ospf 10 Electronics(config-router)#network 172.16.20.4 0.0.0.3 area 20 Electronics(config-router)#network 192.168.22.0 0.0.0.255 area 20 Electronics(config-router)#router-id 20.2.2.2 Electronics(config-router)#do clear ip ospf process Electronics(config-router)#yes Electronics(config-router)#exit Electronics(config)#ipv6 unicast-routing Electronics(config)#int s0/0/0 Electronics(config-if)#ipv6 ospf 10 area 20 Electronics(config-if)#exit Electronics(config)#int g0/0 Electronics(config-if)#ipv6 ospf 10 area 20 Electronics(config-if)#exit Electronics(config)# Electronics(config)#ipv6 router ospf 10 Electronics(config-rtr)#router-id 20.2.2.2 Electronics(config-rtr)#do clear ipv6 ospf process Electronics(config-rtr)#yes Electronics(config-rtr)#exit Electronics(config)#router ospf 10 Electronics(config-router)#passive-interface g0/0 Electronics(config-router)#exit Electronics(config)# Electronics(config)#ipv6 router ospf 10 Electronics(config-rtr)#passive-interface g0/0 Electronics(config-rtr)#exit Electronics(config)#router ospf 10 Electronics(config-router)#auto-cost reference-bandwidth 1000 Electronics(config-router)#exit Electronics(config)#ipv6 router ospf 10 Electronics(config-router)#auto-cost reference-bandwidth 1000 Electronics(config-router)#
[/tab]
[tab title=”Form 2″]
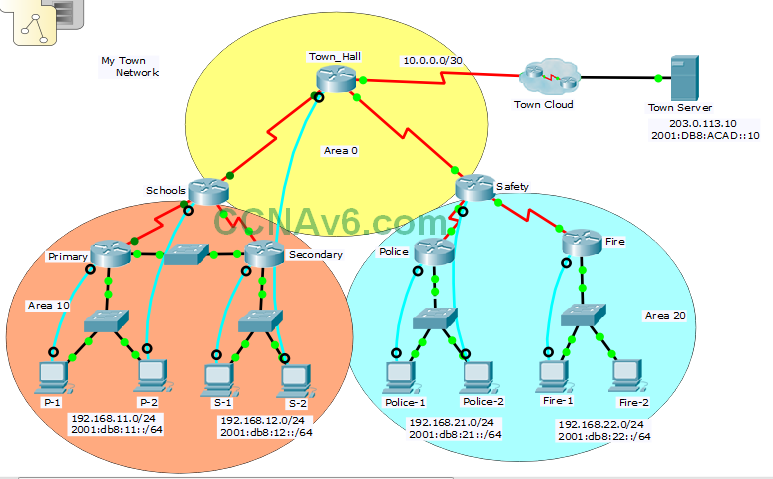
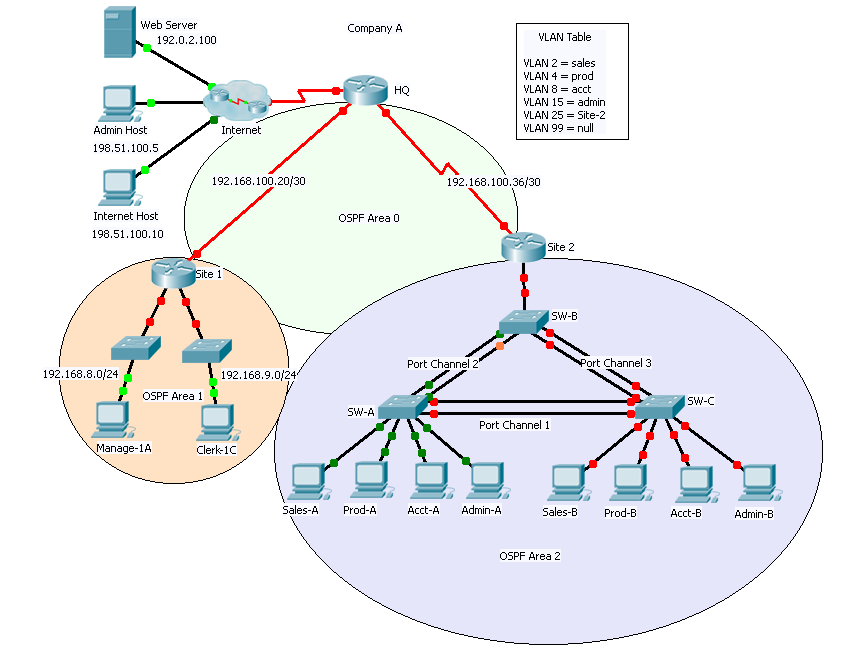
Network Diagram:
Diagram uses slightly different naming convention (Hostnames and vlan names) , same topology)
A few things to keep in mind while completing this activity:
1. Do not use the browser Back button or close or reload any exam windows during the exam.
2. Do not close Packet Tracer when you are done. It will close automatically.
3. Click the Submit Assessment button in the browser window to submit your work.
Introduction
In Part I of this practice skills assessment, you will configure the Company A network with routing and ACLs. You will configure dynamic routing with OSPFv2 and distribute a default route. In addition, you will configure two access control lists.
In Part II of this practice skills assessment, you will configure the Company A network with RPVST+, port security, EtherChannel, DHCP, VLANs and trunking, and routing between VLANs. In addition you will perform an initial configuration on a switch, secure switch ports and create SVIs. You will also control access to the switch management network with an access control list.
All IOS device configurations should be completed from a direct terminal connection to the device console from an available host.
Some values that are required to complete the configurations have not been given to you. In those cases, create the values that you need to complete the requirements. These values may include certain IP addresses, passwords, interface descriptions, banner text, and other values.
When you have been given a text value, such as a password, user name, DHCP pool name, ACL name, VLAN name, etc, you must enter these values exactly as they are given in these instructions. If the values do not match exactly, you may not receive credit for your configuration.
For the sake of time, many repetitive but important configuration tasks have been omitted from this activity. Many of these tasks, especially those related to device security, are essential elements of a network configuration. The intent of this activity is not to diminish the importance of full device configurations.
You will practice and be assessed on the following skills:
• Configuration of initial device settings
• IPv4 address assignment and configuration
• Configuration and addressing of device interfaces
• Configuration of the OSPFv2 routing protocol
• Configuration of a default route
• Configuration of ACL to limit device access
• Configuration of switch management settings including SSH
• Configuration of port security
• Configuration of unused switch ports according to security best practices
• Configuration of RPVST+
• Configuration of EtherChannel
• Configuration of a router as a DHCP server
• Configuration of VLANs and trunks
• Configuration of routing between VLANs
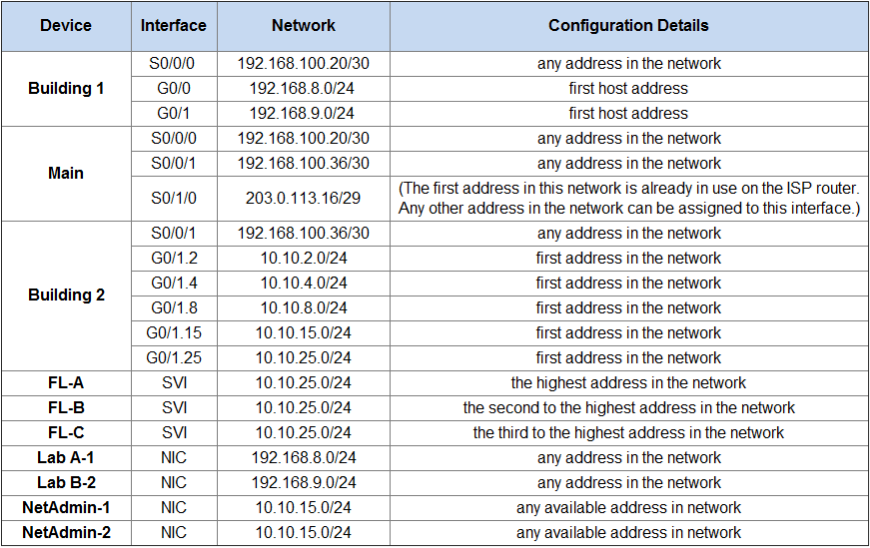
Addressing table:
VLAN Switch Port Assignment Table:
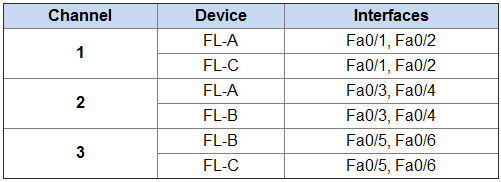
Port-Channel Groups:
Instructions:
All configurations must be performed through a direct terminal connection to the device console line from an available host.
Part I: OSPFv2 Router Configuration
Step 1: Plan the Addressing.
Task:
Determine the IP addresses that you will use for the required interfaces on the devices and LAN hosts. Follow the configuration details provided in the Addressing Table.
How:
This part requires and understanding of the addressing constants that make up a normal network separated by subnets. Let’s take a look at the first entry we are asked to find. We are asked to pick any address in the network 192.168.100.20/30.
A Typical network range has two addresses that are not suitable as host addresses, these are the First and the Last addresses are corespond to the Subnet ID and Broadcast address. So with our network we know that 192.168.100.20 will be the Subnet ID so our First usable host address will be 192.168.100.21/30
The next issue we run into is working out how many host addresses are available in the subnet. To explain this process I’m going to draw out 32bits representing the 4 octets of 8bits that make up an IPv4 address.
[00000000] . [00000000] . [00000000] . [00000000]
Now fill up all the slots that correspond to 30 of the 32 bits
[11111111] . [11111111] . [11111111] . [11111100]
This leaves a total of 2 bits for our hosts to use.
BIT ADDRESS 00 192.168.100.20 Subnet ID 01 192.168.100.21 Host 10 192.168.100.22 Host 11 192.168.100.23 Broadcast Address
Addressing table – Complete
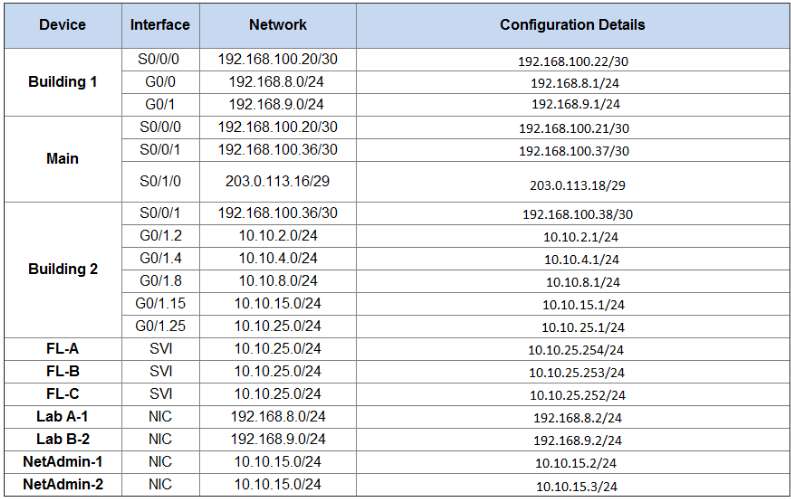
Step 2: Configure Site 1.
Task:
Configure Site 1 with initial settings:
• Configure the router host name: Bldg-1. This value must be entered exactly as it appears here.
• Prevent the router from attempting to resolve command line entries to IP addresses.
• Protect device configurations from unauthorized access with an encrypted secret password.
• Secure the router console and remote access lines.
• Prevent system status messages from interrupting console output.
• Configure a message-of-the-day banner.
• Encrypt all clear text passwords.
How:
• Configure the router host name: Bldg-1. This value must be entered exactly as it appears here.
Router(config)#hostname Bldg-1
• Prevent the router from attempting to resolve command line entries to IP addresses.
Bldg-1(config)#no ip domain lookup
• Protect device configurations from unauthorized access with an encrypted secret password.
Bldg-1(config)#enable secret class
• Secure the router console and remote access lines.
Bldg-1(config)#line console 0 Bldg-1(config-line)#password cisco Bldg-1(config-line)#login Bldg-1(config-line)#line vty 0 4 Bldg-1(config-line)#password cisco Bldg-1(config-line)#login Bldg-1(config-line)#line aux 0 Bldg-1(config-line)#password cisco Bldg-1(config-line)#login
• Prevent system status messages from interrupting console output.
Bldg-1(config)#line console 0 Bldg-1(config-line)#logging synchronous
• Configure a message-of-the-day banner.
Bldg-1(config)#banner motd "Authorized Access Only"
• Encrypt all clear text passwords.
Bldg-1(config)#service password-encryption
Step 3: Configure the Router Interfaces.
Task:
Configure the interfaces of all routers for full connectivity with the following:
• IP addressing
• Descriptions for the three connected interfaces of HQ.
• Configure DCE settings where required. Use a rate of 128000.
• The Ethernet subinterfaces on Site 2 will configured later in this assessment.
How:
• IP addressing
Bldg-1(config)#int s0/0/0 Bldg-1(config-if)#ip address 192.168.100.22 255.255.255.252 Bldg-1(config-if)#no shutdown Bldg-1(config)#int g0/0 Bldg-1(config-if)#ip address 192.168.8.1 255.255.255.0 Bldg-1(config-if)#no shutdown Bldg-1(config)#int g0/1 Bldg-1(config-if)#ip address 192.168.9.1 255.255.255.0 Bldg-1(config-if)#no shutdown Main(config)#int s0/0/0 Main(config-if)#ip address 192.168.100.21 255.255.255.252 Main(config-if)#no shutdown Main(config)#int s0/0/1 Main(config-if)#ip address 192.168.100.37 255.255.255.252 Main(config-if)#no shutdown Main(config)#int s0/1/0 Main(config-if)#ip address 203.0.113.18 255.255.255.248 Main(config-if)#no shutdown Bldg-2(config)#int s0/0/1 Bldg-2(config-if)#ip address 192.168.100.38 255.255.255.252 Bldg-2(config-if)#no shutdown Bldg-2(config)#int g0/1 Bldg-2(config-if)#no shutdown
• Descriptions for the three connected interfaces of HQ.
Main(config)#int s0/0/0 Main(config-if)#description 2-Building1 Main(config)#int s0/0/1 Main(config-if)#description 2-Building2 Main(config)#int s0/1/0 Main(config-if)#description 2-INTERNET
• Configure DCE settings where required. Use a rate of 128000.
Bldg-1(config)#int s0/0/0 Bldg-1(config-if)#clock rate 128000 Main(config)#int s0/0/1 Main(config-if)#clock rate 128000
• The Ethernet subinterfaces on Site 2 will configured later in this assessment.
Step 4: Configure inter-VLAN routing on Site 2.
Task:
Configure router Site 2 to route between VLANs using information in the Addressing Table and VLAN Switch Port Assignment Table. The VLANs will be configured on the switches later in this assessment.
• Do not route the VLAN 99 network.
How:
Bldg-2(config)#int g0/1.2 Bldg-2(config-subif)#encapsulation dot1Q 2 Bldg-2(config-subif)#ip address 10.10.2.1 255.255.255.0 Bldg-2(config-subif)#int g0/1.4 Bldg-2(config-subif)#encapsulation dot1Q 4 Bldg-2(config-subif)#ip address 10.10.4.1 255.255.255.0 Bldg-2(config-subif)#int g0/1.8 Bldg-2(config-subif)#encapsulation dot1Q 8 Bldg-2(config-subif)#ip address 10.10.8.1 255.255.255.0 Bldg-2(config-subif)#int g0/1.15 Bldg-2(config-subif)#encapsulation dot1Q 15 Bldg-2(config-subif)#ip address 10.10.15.1 255.255.255.0 Bldg-2(config-subif)#int g0/1.25 Bldg-2(config-subif)#encapsulation dot1Q 25 Bldg-2(config-subif)#ip address 10.10.25.1 255.255.255.0
Step 5: Configure Default Routing.
Task:
On Main, configure a default route to the Internet. Use the exit interface argument.
How:
Main(config)#ip route 0.0.0.0 0.0.0.0 s0/1/0
Step 6: Configure OSPF Routing.
a. On all routers:
Task:
• Configure multiarea OSPFv2 to route between all internal networks. Use a process ID of 1.
• Use the area numbers shown in the topology.
• Use the correct wild card masks for all network statements.
• You are not required to route the SVI-NET VLAN network on Site 2.
How:
• Configure multiarea OSPFv2 to route between all internal networks. Use a process ID of 1.
• Use the area numbers shown in the topology.
• Use the correct wild card masks for all network statements.
• You are not required to route the SVI-NET VLAN network on Site 2.
Calculating the wildcard for each OSPF route is done by looking again at the subnet mask bit. lets use the 192.168.100.20/30 network. The following shows what a wild card mask for 0.0.0.0 or /32 would look like
[00000000] . [00000000] . [00000000] . [00000000]
If we have 30 bits instead we’re left with two bits
[00000000] . [00000000] . [00000000] . [00000011]
This gives us a wild card of 0.0.0.3. Similarly you can look at what a /24 networks bit pattern looks like below.
[00000000] . [00000000] . [00000000] . [11111111]
/24’s wild card mask is 0.0.0.255.
Using this information we can setup the various networks on each of the routers
Bldg-1(config)#router ospf 1 Bldg-1(config-router)#network 192.168.100.20 0.0.0.3 area 0 Bldg-1(config-router)#network 192.168.8.0 0.0.0.255 area 1 Bldg-1(config-router)#network 192.168.9.0 0.0.0.255 area 1 Main(config)#router ospf 1 Main(config-router)#network 192.168.100.20 0.0.0.3 area 0 Main(config-router)#network 192.168.100.36 0.0.0.3 area 0 Bldg-2(config)#router ospf 1 Bldg-2(config-router)#network 192.168.100.36 0.0.0.3 area 0 Bldg-2(config-router)#network 10.10.2.0 0.0.0.255 area 2 Bldg-2(config-router)#network 10.10.4.0 0.0.0.255 area 2 Bldg-2(config-router)#network 10.10.8.0 0.0.0.255 area 2 Bldg-2(config-router)#network 10.10.15.0 0.0.0.255 area 2
• Prevent routing updates from being sent to the LANs.
Bldg-1(config)#router ospf 1 Bldg-1(config-router)#passive-interface GigabitEthernet0/0 Bldg-1(config-router)#passive-interface GigabitEthernet0/1 Main(config)#router ospf 1 Main(config-router)#passive-interface Serial0/1/0 Bldg-2(config)#router ospf 1 Bldg-2(config-router)#passive-interface GigabitEthernet0/1 Bldg-2(config-router)#passive-interface g0/1.2 Bldg-2(config-router)#passive-interface g0/1.4 Bldg-2(config-router)#passive-interface g0/1.8 Bldg-2(config-router)#passive-interface g0/1.15
b. On the HQ router:
Task:
• Configure multiarea OSPFv2 to distribute the default route to the other routers.
How:
Main(config)#router ospf 1 Main(config-router)#default-information originate
Step 7: Customize Multiarea OSPFv2.
Customize multiarea OSPFv2 by performing the following configuration tasks:
Task:
a. Set the bandwidth of all serial interfaces to 128 kb/s.
b. Configure OSPF router IDs as follows:
• Site 1: 1.1.1.1
• HQ: 2.2.2.2
• Site 2: 3.3.3.3
• The configured router IDs should be in effect on all three routes.
c. Configure the OSPF cost of the link between Site 1 and HQ to 7500.
How:
a. Set the bandwidth of all serial interfaces to 128 kb/s.
Bldg-1(config)#int s0/0/0 Bldg-1(config-if)#bandwidth 128 Main(config)#int s0/0/0 Main(config-if)#bandwidth 128 Main(config)#int s0/0/1 Main(config-if)#bandwidth 128 Bldg-2(config)#int s0/0/1 Bldg-2(config-if)#bandwidth 128
b. Configure OSPF router IDs as follows:
• Site 1: 1.1.1.1
Bldg-1(config)#router ospf 1 Bldg-1(config-router)#router-id 1.1.1.1
• HQ: 2.2.2.2
Main(config)#router ospf 1 Main(config-router)#router-id 2.2.2.2
• Site 2: 3.3.3.3
Bldg-2(config)#router ospf 1 Bldg-2(config-router)#router-id 3.3.3.3
• The configured router IDs should be in effect on all three routes.
c. Configure the OSPF cost of the link between Site 1 and HQ to 7500.
Bldg-1(config)#int s0/0/0 Bldg-1(config-if)#ip ospf cost 7500 Main(config)#int s0/0/0 Main(config-if)#ip ospf cost 7500
Step 8: Configure OSPF MD5 Authentication on the Required Interfaces.
How:
Configure OSPF to authenticate routing updates with MD5 authentication on the OSPF interfaces.
• Use a key value of 1.
• Use xyz_OSPF as the password.
• Apply MD5 authentication to the required interfaces.
How:
Bldg-1(config)#int s0/0/0 Bldg-1(config-if)#ip ospf message-digest-key 1 md5 xyz_OSPF Bldg-1(config-if)#ip ospf authentication message-digest Main(config)#int s0/1/0 Main(config-if)#ip ospf message-digest-key 1 md5 xyz_OSPF Main(config-if)#ip ospf authentication message-digest Main(config)#int s0/0/1 Main(config-if)#ip ospf message-digest-key 1 md5 xyz_OSPF Main(config-if)#ip ospf authentication message-digest Bldg-2(config)#int s0/0/1 Bldg-2(config-if)#ip ospf message-digest-key 1 md5 xyz_OSPF Bldg-2(config-if)#ip ospf authentication message-digest
Step 9: Configure Access Control Lists.
Task/How:
You will configure two access control lists in this step. You should use the any and host keywords in the ACL statements as required. The ACL specifications are as follows:
a. Restrict access to the vty lines on HQ with an ACL:
• Create a named standard ACL using the name telnetBlock. Be sure that you enter this name exactly as it appears in this instruction or you will not receive credit for your configuration.
Main(config)#ip access-list standard TELNET-BLOCK
• Allow only Admin Host to access the vty lines of HQ.
• No other Internet hosts (including hosts not visible in the topology) should be able to access the vty lines of HQ.
• Your solution should consist of one ACL statement.
• Your ACL should be placed in the most efficient location as possible to conserve network bandwidth and device processing resources.
Main(config-std-nacl)#permit host 198.51.100.5 Main(config)#line vty 0 15 Main(config-line)#access-class TELNET-BLOCK in
b. Block ping requests from the Internet with an ACL:
• Use access list number 101.
Main(config)#interface serial 0/1/0 Main(config-if)#ip access-group 101 in
• Allow only Admin Host to ping addresses within the Company A network. Only echo messages should be permitted.
• Prevent all other Internet hosts (not only the Internet hosts visible in the topology) from pinging addresses inside the Company A network. Block echo messages only.
• All other traffic should be allowed.
• Your ACL should consist of three statements.
• Your ACL should be placed in the most efficient location as possible to conserve network bandwidth and device processing resources.
c. Control access to the management interfaces (SVI) of the three switches attached to Site 2 as follows:
• Create a standard ACL.
• Use the number 1 for the list.
Bldg-2(config)#access-list 1 permit 10.10.15.0 0.0.0.255
• Permit only addresses from the admin VLAN network to access any address on the SVI-NET VLAN network. (VLAN25)
Bldg-2(config)#interface gi0/1.25 Bldg-2(config-if)#ip access-group 1 out
• Hosts on the admin VLAN network should be able to reach all other destinations.
• Your list should consist of one statement.
• Your ACL should be placed in the most efficient location as possible to conserve network bandwidth and device processing resources.
• You will be able to test this ACL at the end of Part II of this assessment.
Part II: Switching and DHCP Configuration
Step 1: Create and name VLANs.
Task/How:
On all three switches that are attached to Site 2, create and name the VLANs shown in the VLAN Table.
• The VLAN names that you configure must match the values in the table exactly.
• Each switch should be configured with all of the VLANs shown in the table.
FL-A(config)#vlan 2 FL-A(config-vlan)#name dept1 FL-A(config)#vlan 4 FL-A(config-vlan)#name dept2 FL-A(config)#vlan 8 FL-A(config-vlan)#name dept3 FL-A(config)#vlan 15 FL-A(config-vlan)#name NetAdmin FL-A(config)#vlan 25 FL-A(config-vlan)#name manage FL-A(config)#vlan 99 FL-A(config-vlan)#name safe FL-B(config)#vlan 2 FL-B(config-vlan)#name dept1 FL-B(config)#vlan 4 FL-B(config-vlan)#name dept2 FL-B(config)#vlan 8 FL-B(config-vlan)#name dept3 FL-B(config)#vlan 15 FL-B(config-vlan)#name NetAdmin FL-B(config)#vlan 25 FL-B(config-vlan)#name manage FL-B(config)#vlan 99 FL-B(config-vlan)#name safe FL-C(config)#vlan 2 FL-C(config-vlan)#name dept1 FL-C(config)#vlan 4 FL-C(config-vlan)#name dept2 FL-C(config)#vlan 8 FL-C(config-vlan)#name dept3 FL-C(config)#vlan 15 FL-C(config-vlan)#name NetAdmin FL-C(config)#vlan 25 FL-C(config-vlan)#name manage FL-C(config)#vlan 99 FL-C(config-vlan)#name safe
Step 2: Assign switch ports to VLANs.
Task/How:
Using the VLAN table, assign switch ports to the VLANs you created in Step 1, as follows:
• All switch ports that you assign to VLANsn should be configured to static access mode.
• All switch ports that you assign to VLANs should be activated.
FL-A(config)#interface fa0/5 FL-A(config-if)#switchport mode access FL-A(config-if)#switchport access vlan 2 FL-A(config-if)#no shutdown FL-A(config)#interface fa0/10 FL-A(config-if)#switchport mode access FL-A(config-if)#switchport access vlan 4 FL-A(config-if)#no shutdown FL-A(config)#interface fa0/15 FL-A(config-if)#switchport mode access FL-A(config-if)#switchport access vlan 8 FL-A(config-if)#no shutdown FL-A(config)#interface fa0/24 FL-A(config-if)#switchport mode access FL-A(config-if)#switchport access vlan 15 FL-A(config-if)#no shutdown FL-C(config)#interface fa0/7 FL-C(config-if)#switchport mode access FL-C(config-if)#switchport access vlan 2 FL-C(config-if)#no shutdown FL-C(config)#interface fa0/10 FL-C(config-if)#switchport mode access FL-C(config-if)#switchport access vlan 4 FL-C(config-if)#no shutdown FL-C(config)#interface fa0/15 FL-C(config-if)#switchport mode access FL-C(config-if)#switchport access vlan 8 FL-C(config-if)#no shutdown FL-C(config)#interface fa0/24 FL-C(config-if)#switchport mode access FL-C(config-if)#switchport access vlan 15 FL-C(config-if)#no shutdown
• Note that all of the unused ports on FL-A should be assigned to VLAN 99. This configuration step on switches FL-B and FL-C is not required in this assessment for the sake of time.
• Secure the unused switch ports on FL-A by shutting them down.
FL-A(config)#interface range fa0/6-9,fa0/11-14,fa0/16-23 FL-A(config-if-range)#switchport mode access FL-A(config-if-range)#switchport access vlan 99 FL-A(config-if-range)#shutdown FL-A(config)#interface range g0/1-2 FL-A(config-if-range)#switchport mode access FL-A(config-if-range)#switchport access vlan 99 FL-A(config-if-range)#shutdown
Step 3: Configure the SVIs.
Task/How:
Refer to the Addressing Table. Create and address the SVIs on all three of the switches that are attached to Site 2. Configure the switches so that they can communicate with hosts on other networks. Full connectivity will be established after routing between VLANs has been configured later in this assessment.
FL-A(config)#ip default-gateway 10.10.25.1 FL-A(config)#interface vlan 25 FL-A(config-vlan)#ip address 10.10.25.254 255.255.255.0 FL-A(config-vlan)#no shutdown FL-B(config)#ip default-gateway 10.10.25.1 FL-B(config)#interface vlan 25 FL-B(config-vlan)#ip address 10.10.25.253 255.255.255.0 FL-B(config-vlan)#no shutdown FL-C(config)#ip default-gateway 10.10.25.1 FL-C(config)#interface vlan 25 FL-C(config-vlan)#ip address 10.10.25.252 255.255.255.0 FL-C(config-vlan)#no shutdown
Step 4: Configure Trunking and EtherChannel.
Task/How:
a. Use the information in the Port-Channel Groups table to configure EtherChannel as follows:
• Use LACP.
• The switch ports on both sides of Channels 1 and 2 should initiate negotiations for channel establishment.
FL-A(config)#interface range fa0/1-2 FL-A(config-if-range)#channel-group 1 mode active FL-A(config-if-range)#no shutdown FL-A(config)#interface range fa0/3-4 FL-A(config-if-range)#channel-group 2 mode active FL-A(config-if-range)#no shutdown FL-A(config)#interface port-channel 1 FL-A(config-if)#switchport mode trunk FL-A(config)#interface port-channel 2 FL-A(config-if)#switchport mode trunk FL-B(config)#interface range fa0/3-4 FL-B(config-if-range)#channel-group 2 mode active FL-B(config-if-range)#no shutdown FL-B(config)#interface port-channel 2 FL-B(config-if)#switchport mode trunk FL-C(config)#interface range fa0/1-2 FL-C(config-if-range)#channel-group 1 mode active FL-C(config-if-range)#no shutdown FL-C(config)#interface port-channel 1 FL-C(config-if)#switchport mode trunk
• The switch ports on the FL-B side of Channel 3 should initiate negotiations with the switch ports on FL-C.
FL-B(config)#interface range fa0/5-6 FL-B(config-if-range)#channel-group 3 mode active FL-B(config-if-range)#no shutdown FL-B(config)#interface port-channel 3 FL-B(config-if)#switchport mode trunk
• The switch ports on the FL-C side of Channel 3 should not initiate negotiations with the switch ports on the other side of the channel.
FL-C(config)#interface range fa0/5-6 FL-C(config-if-range)#channel-group 3 mode passive FL-B(config-if-range)#no shutdown FL-C(config)#interface port-channel 3 FL-C(config-if)#switchport mode trunk
• All channels should be ready to forward data after they have been configured.
FL-X(config-if)#no shutdown (if you didn't do it prior)
b. Configure all port-channel interfaces as trunks.
FL-X(config)#interface port-channel X (again you should have done it prior) FL-X(config-if)#switchport mode trunk
c. Configure static trunking on the switch port on FL-B that is connected to Site 2.
FL-B(config)#interface g0/1 FL-B(config-if)#switchport mode trunk
Step 5: Configure Rapid PVST+.
Task/How:
Configure Rapid PVST+ as follows:
a. Activate Rapid PVST+ and set root priorities.
• All three switches should be configured to run Rapid PVST+.
FL-A(config)#spanning-tree mode rapid-pvst FL-B(config)#spanning-tree mode rapid-pvst FL-C(config)#spanning-tree mode rapid-pvst
• FL-A should be configured as root primary for VLAN 2 and VLAN 4 using the default primary priority values.
FL-A(config)#spanning-tree vlan 2 root primary FL-A(config)#spanning-tree vlan 4 root primary
• FL-A should be configured as root secondary for VLAN 8 and VLAN 15 using the default secondary priority values.
FL-A(config)#spanning-tree vlan 8 root secondary FL-A(config)#spanning-tree vlan 15 root secondary
• FL-C should be configured as root primary for VLAN 8 and VLAN 15 using the default primary priority values.
FL-C(config)#spanning-tree vlan 8 root primary FL-C(config)#spanning-tree vlan 15 root primary
• FL-C should be configured as root secondary for VLAN 2 and VLAN 4 using the default secondary priority values.
FL-C(config)#spanning-tree vlan 2 root secondary FL-C(config)#spanning-tree vlan 4 root secondary
b. Activate PortFast and BPDU Guard on the active FL-C switch access ports.
• On FL-C, configure PortFast on the access ports that are connected to hosts.
FL-C(config)#interface range fa0/7, fa0/10, fa0/15, fa0/24 FL-C(config-if-range)#spanning-tree portfast
• On FL-C, activate BPDU Guard on the access ports that are connected to hosts.
FL-C(config)#interface range fa0/7, fa0/10, fa0/15, fa0/24 FL-C(config-if-range)#spanning-tree bpduguard enable FL-C(config-if-range)#no shutdown
Step 6: Configure switch security.
Task/How:
You are required to complete the following only on some of the devices in the network for this assessment. In reality, security should be configured on all devices in the network.
a. Configure port security on all active access ports that have hosts connected on FL-A.
FL-A(config)#interface fa0/5 FL-A(config-if)#switchport port-security FL-A(config)#interface fa0/10 FL-A(config-if)#switchport port-security FL-A(config)#interface fa0/15 FL-A(config-if)#switchport port-security FL-A(config)#interface fa0/24 FL-A(config-if)#switchport port-security
• Each active access port should accept only two MAC addresses before a security action occurs.
FL-A(config)#interface fa0/5 FL-A(config-if)#switchport port-security maximum 2 FL-A(config)#interface fa0/10 FL-A(config-if)#switchport port-security maximum 2 FL-A(config)#interface fa0/15 FL-A(config-if)#switchport port-security maximum 2 FL-A(config)#interface fa0/24 FL-A(config-if)#switchport port-security maximum 2
• The learned MAC addresses should be recorded in the running configuration.
FL-A(config)#interface fa0/5 FL-A(config-if)#switchport port-security mac-address sticky FL-A(config)#interface fa0/10 FL-A(config-if)#switchport port-security mac-address sticky FL-A(config)#interface fa0/15 FL-A(config-if)#switchport port-security mac-address sticky FL-A(config)#interface fa0/24 FL-A(config-if)#switchport port-security mac-address sticky
• If a security violation occurs, the switch ports should provide notification that a violation has occurred but not place the interface in an err-disabled state.
FL-A(config)#interface fa0/5 FL-A(config-if)#switchport port-security violation restrict FL-A(config)#interface fa0/10 FL-A(config-if)#switchport port-security violation restrict FL-A(config)#interface fa0/15 FL-A(config-if)#switchport port-security violation restrict FL-A(config)#interface fa0/24 FL-A(config-if)#switchport port-security violation restrict
b. On FL-B, configure the virtual terminal lines to accept only SSH connections.
• Use a domain name of ccnaPTSA.com.
FL-B(config)#ip domain-name ccnaPTSA.com
• Use FL-B as the host name.
FL-B(config)#hostname FL-B
• Use a modulus value of 1024.
FL-B(config)#crypto key generate rsa select 1024 key length
• Configure SSH version 2.
FL-B(config)#ip ssh version 2
• Configure the vty lines to only accept SSH connections.
FL-B(config)#line vty 0 4 FL-B(config-line)#login local FL-B(config-line)#transport input ssh FL-B(config)#line vty 5 15 FL-B(config-line)#login local FL-B(config-line)#transport input ssh
• Configure user-based authentication for the SSH connections with a user name of netadmin and an encrypted secret password of SSHsecret9 . The user name and password must match the values provided here exactly.
FL-B(config)#username netadmin password SSH_secret9
c. Ensure that all unused switch ports on FL-A have been secured as follows:
• They should be assigned to VLAN 99.
• They should all be in access mode.
• They should be shutdown.
Should have been done in Step 2, but here they are anyway FL-A(config)#interface range fa0/6-9,fa0/11-14,fa0/16-23 FL-A(config-if-range)#switchport mode access FL-A(config-if-range)#switchport access vlan 99 FL-A(config-if-range)#shutdown FL-A(config)#interface range g0/1-2 FL-A(config-if-range)#switchport mode access FL-A(config-if-range)#switchport access vlan 99 FL-A(config-if-range)#shutdown
Step 7: Configure Site 2 as a DHCP server for the hosts attached to the FL-A and FL-C switches.
Task/How:
Configure three DHCP pools as follows:
• Refer to the information in the Addressing Table.
• Create a DHCP pool for hosts on VLAN 2 using the pool name vlan2pool.
Bldg-2(config)#ip dhcp pool vlan2pool Bldg-2(dhcp-config)#network 10.10.2.0 255.255.255.0 Bldg-2(dhcp-config)#default-router 10.10.2.1 Bldg-2(dhcp-config)#dns-server 192.168.200.225
• Create a DHCP pool for hosts on VLAN 4 using the pool name vlan4pool.
Bldg-2(config)#ip dhcp pool vlan4pool Bldg-2(dhcp-config)#network 10.10.4.0 255.255.255.0 Bldg-2(dhcp-config)#default-router 10.10.4.1 Bldg-2(dhcp-config)#dns-server 192.168.200.225
• Create a DHCP pool for hosts on VLAN 8 using the pool name vlan8pool.
Bldg-2(config)#ip dhcp pool vlan8pool Bldg-2(dhcp-config)#network 10.10.8.0 255.255.255.0 Bldg-2(dhcp-config)#default-router 10.10.8.1 Bldg-2(dhcp-config)#dns-server 192.168.200.225
• All VLAN pool names must match the provided values exactly.
• Exclude the first five addresses from each pool.
Bldg-2(config)#ip dhcp excluded-address 10.10.2.1 10.10.2.5 Bldg-2(config)#ip dhcp excluded-address 10.10.4.1 10.10.4.5 Bldg-2(config)#ip dhcp excluded-address 10.10.8.1 10.10.8.5
• Configure a DNS server address of 192.168.200.225.
Bldg-2(dhcp-config)#dns-server 192.168.200.225 (this command from above)
• All hosts should be able to communication with hosts on other networks.
Bldg-2(dhcp-config)#default-router 10.10.X.1 (this command from above)
Step 8: Configure host addressing.
Task:
Hosts should be able to ping each other and external hosts after they have been correctly addressed, where permitted.
• Hosts on VLANs 2, 4, and 8 should be configured to receive addresses dynamically over DHCP.
• Hosts on VLAN 15 should be addressed statically as indicated in the Addressing Table. Once configured, the hosts should be able to ping hosts on other networks.
• Hosts on the LANs attached to Site 1 should be statically assigned addresses that enable them to communicate with hosts on other networks, as indicated in the Addressing Table.
How:
Simply setup all the addressing manually through the GUI on each workstation from the IP Addressing table
Quick Summary:
Attention: Rename the hostnames and VLAN names
hostname Bldg-1
no ip domain-lookup
enable secret cisco
line console 0
logging synchronous
password cisco
login
line aux 0
password cisco
login
line vty 0 15
password cisco
login
service password-encryption
banner motd #Authorized access only!#
interface serial 0/0/0
bandwidth 128
clock rate 128000
ip address 192.168.100.22 255.255.255.252
description 2-Central
ip ospf cost 7500
ip ospf message-digest-key 1 md5 xyz_OSPF
ip ospf authentication message-digest
no shutdown
exit
interface gi 0/0
ip address 192.168.8.1 255.255.255.0
description Manage-1A
no shutdown
interface gi 0/1
ip address 192.168.9.1 255.255.255.0
description Clerk-1C
no shutdown
exit
router ospf 1
router-id 1.1.1.1
passive-interface GigabitEthernet0/0
passive-interface GigabitEthernet0/1
area 0 authentication message-digest
network 192.168.100.20 0.0.0.3 area 0
network 192.168.8.0 0.0.0.255 area 1
network 192.168.9.0 0.0.0.255 area 1
no auto-summary
exit
hostname Main
no ip domain-lookup
enable secret cisco
line console 0
logging synchronous
password cisco
login
line aux 0
password cisco
login
line vty 0 15
password cisco
login
service password-encryption
banner motd #Authorized acces only #
ip route 0.0.0.0 0.0.0.0 s0/1/0
interface serial 0/0/0
bandwidth 128
ip address 192.168.100.21 255.255.255.252
description 2-East
ip ospf cost 7500
ip ospf message-digest-key 1 md5 xyz_OSPF
ip ospf authentication message-digest
no shutdown
exit
interface serial 0/0/1
bandwidth 128
ip address 192.168.100.37 255.255.255.252
description 2-West
clock rate 128000
ip ospf message-digest-key 1 md5 xyz_OSPF
ip ospf authentication message-digest
no shutdown
exit
interface serial 0/1/0
bandwidth 128
ip address 203.0.113.18 255.255.255.248
description 2-INTERNET
no shutdown
exit
router ospf 1
router-id 2.2.2.2
area 0 authentication message-digest
default-information originate
passive-interface Serial0/1/0
network 192.168.100.20 0.0.0.3 area 0
network 192.168.100.36 0.0.0.3 area 0
no auto-summary
exit
ip access-list standard telnetBlock
permit host 198.51.100.5
access-list 101 permit icmp 198.51.100.5 0.0.0.0 any echo
access-list 101 deny icmp any any echo
access-list 101 permit ip any any
line vty 0 15
access-class telnetBlock in
interface serial 0/1/0
ip access-group 101 in
exit
hostname Bldg-2
no ip domain-lookup
enable secret cisco
line console 0
logging synchronous
password cisco
login
line vty 0 15
password cisco
login
service password-encryption
banner motd #Authorized acces only#
interface serial 0/0/1
bandwidth 128
ip address 192.168.100.38 255.255.255.252
description 2-Central
ip ospf message-digest-key 1 md5 xyz_OSPF
ip ospf authentication message-digest
no shutdown
interface gi 0/1
no shutdown
interface gi 0/1.2
encapsulation dot1q 2
ip address 10.10.2.1 255.255.255.0
interface gi 0/1.4
encapsulation dot1q 4
ip address 10.10.4.1 255.255.255.0
interface gi 0/1.8
encapsulation dot1q 8
ip address 10.10.8.1 255.255.255.0
interface gi 0/1.15
encapsulation dot1q 15
ip address 10.10.15.1 255.255.255.0
interface gi 0/1.25
encapsulation dot1q 25
ip address 10.10.25.1 255.255.255.0
exit
router ospf 1
router-id 3.3.3.3
passive-interface GigabitEthernet0/1
network 192.168.100.36 0.0.0.3 area 0
network 10.10.2.0 0.0.0.255 area 2
network 10.10.4.0 0.0.0.255 area 2
network 10.10.8.0 0.0.0.255 area 2
network 10.10.15.0 0.0.0.255 area 2
no auto-summary
passive-interface g0/1.2
passive-interface g0/1.4
passive-interface g0/1.8
passive-interface g0/1.15
exit
interface serial 0/0/1
ip summary-address eigrp 100 10.10.0.0 255.255.240.0
ip dhcp excluded-address 10.10.2.1 10.10.2.5
ip dhcp excluded-address 10.10.4.1 10.10.4.5
ip dhcp excluded-address 10.10.8.1 10.10.8.5
ip dhcp pool vlan2pool
network 10.10.2.0 255.255.255.0
default-router 10.10.2.1
dns-server 192.168.200.225
ip dhcp pool vlan4pool
network 10.10.4.0 255.255.255.0
default-router 10.10.4.1
dns-server 192.168.200.225
ip dhcp pool vlan8pool
network 10.10.8.0 255.255.255.0
default-router 10.10.8.1
dns-server 192.168.200.225
exit
access-list 1 permit 10.10.15.0 0.0.0.255
interface gi0/1.25
ip access-group 1 out
hostname FL-A
no ip domain-lookup
enable secret cisco
line console 0
logging synchronous
password cisco
login
line vty 0 15
password cisco
login
service password-encryption
banner motd #Authorized access only!#
ip default-gateway 10.10.25.1
vlan 2
name dept1
vlan 4
name dept2
vlan 8
name dept3
vlan 15
name NetAdmin
vlan 25
name manage
vlan 99
name safe
interface vlan 25
ip address 10.10.25.254 255.255.255.0
no shutdown
interface fa0/5
switchport mode acces
switchport acces vlan 2
interface fa0/10
switchport mode acces
switchport acces vlan 4
interface fa0/15
switchport mode acces
switchport acces vlan 8
interface fa0/24
switchport mode acces
switchport acces vlan 15
interface range fa0/6-9,fa0/11-14,fa0/16-23
switchport mode acces
switchport acces vlan 99
shutdown
interface range gi0/1-2
switchport mode acces
switchport acces vlan 99
shutdown
interface range fa0/1-2
channel-group 1 mode active
interface port-channel 1
switchport mode trunk
interface range fa0/3-4
channel-group 2 mode active
interface port-channel 2
switchport mode trunk
exit
spanning-tree mode rapid-pvst
spanning-tree vlan 2 root primary
spanning-tree vlan 4 root primary
spanning-tree vlan 8 root secondary
spanning-tree vlan 15 root secondary
interface fa0/5
switchport port-security
switchport port-security violation restrict
switchport port-security maximum 2
switchport port-security mac-address sticky
interface fa0/10
switchport port-security
switchport port-security violation restrict
switchport port-security maximum 2
switchport port-security mac-address sticky
interface fa0/15
switchport port-security
switchport port-security violation restrict
switchport port-security maximum 2
switchport port-security mac-address sticky
interface fa0/24
switchport port-security
switchport port-security violation restrict
switchport port-security maximum 2
switchport port-security mac-address sticky
hostname FL-B
no ip domain-lookup
enable secret cisco
line console 0
logging synchronous
password cisco
login
line vty 0 15
password cisco
login
service password-encryption
banner motd #Authorized acces only!#
ip ssh version 2
ip domain-name ccnaPTSA.com
crypto key generate rsa
1024
username netadmin secret SSHsecret9
line vty 0 4
login local
transport input ssh
line vty 5 15
login local
transport input ssh
ip default-gateway 10.10.25.1
vlan 2
name dept1
vlan 4
name dept2
vlan 8
name dept3
vlan 15
name NetAdmin
vlan 25
name manage
vlan 99
name safe
interface vlan 25
ip address 10.10.25.253 255.255.255.0
no shutdown
interface gi 0/1
switchport mode trunk
interface range fa0/3-4
channel-group 2 mode active
interface port-channel 2
switchport mode trunk
interface range fa0/5-6
channel-group 3 mode active
interface port-channel 3
switchport mode trunk
spanning-tree mode rapid-pvst
hostname FL-C
no ip domain-lookup
enable secret cisco
line console 0
logging synchronous
password cisco
login
line vty 0 15
password cisco
login
service password-encryption
banner motd #Authorized acces only !#
ip default-gateway 10.10.25.1
vlan 2
name dept1
vlan 4
name dept2
vlan 8
name dept3
vlan 15
name NetAdmin
vlan 25
name manage
vlan 99
name safe
interface vlan 25
ip address 10.10.25.252 255.255.255.0
no shutdown
interface fa0/7
switchport mode acces
switchport acces vlan 2
interface fa0/10
switchport mode acces
switchport acces vlan 4
interface fa0/15
switchport mode acces
switchport acces vlan 8
interface fa0/24
switchport mode acces
switchport acces vlan 15
interface range fa0/1-2
channel-group 1 mode active
no shutdown
interface port-channel 1
switchport mode trunk
interface range fa0/5-6
channel-group 3 mode passive
no shutdown
interface port-channel 3
switchport mode trunk
spanning-tree mode rapid-pvst
spanning-tree vlan 2 root secondary
spanning-tree vlan 4 root secondary
spanning-tree vlan 8 root primary
spanning-tree vlan 15 root primary
interface range fa0/7, fa0/10, fa0/15, fa0/24
spanning-tree portfast
spanning-tree bpduguard enable
no shutdown

Why there’s no permit statements for access-group 101 ? (2nd Diagram, part I, step 9)
The configuration for the second diagram will not work properly.