[alert-announce]How to find: Press “Ctrl + F” in the browser and fill in whatever wording is in the question to find that question/answer. If the question is not here, find it in Questions Bank.[/alert-announce][alert-note]NOTE: If you have the new question on this test, please comment Question and Multiple-Choice list in form below this article. We will update answers for you in the shortest time. Thank you! We truly value your contribution to the website.[/alert-note]
Modules 9 – 12: Optimize, Monitor, and Troubleshoot Networks Exam Answers Answers
1. What is the term used to indicate a variation of delay?
- latency
- serialization delay
- speed mismatch
- jitter
2. A network engineer performs a ping test and receives a value that shows the time it takes for a packet to travel from a source to a destination device and return. Which term describes the value?
- jitter
- latency
- priority
- bandwidth
3. What role do network devices play in the IntServ QoS model?
- Network devices ensure that resources are available before traffic is allowed to be sent by a host through the network.
- Network devices provide a best-effort approach to forwarding traffic.
- Network devices are configured to service multiple classes of traffic and handle traffic as it may arrive.
- Network devices use QoS on a hop-by-hop basis to provide excellent scalability.
4. Which device would be classified as a trusted endpoint?
- switch
- router
- firewall
- IP phone
5. What is the benefit of deploying Layer 3 QoS marking across an enterprise network?
- Layer 3 marking can carry the QoS information end-to-end.
- Layer 3 marking can carry QoS information on switches that are not IP aware.
- Layer 3 marking can be carried in the 802.1Q fields.
- Layer 3 marking can be used to carry non-IP traffic.
- Layer 2 marking of frames can be performed for non-IP traffic.
- Layer 2 marking of frames is the only QoS option available for switches that are not “IP aware.”
- Layer 3 marking will carry the QoS information end-to-end.
6. What is the function of a QoS trust boundary?
- A trust boundary identifies the location where traffic cannot be remarked.
- A trust boundary only allows traffic to enter if it has previously been marked.
- A trust boundary identifies which devices trust the marking on packets that enter a network.
- A trust boundary only allows traffic from trusted endpoints to enter the network.
7. What are two approaches to prevent packet loss due to congestion on an interface? (Choose two.)
- Decrease buffer space.
- Disable queuing mechanisms.
- Drop lower-priority packets.
- Prevent bursts of traffic.
- Increase link capacity.
- Increase link capacity to ease or prevent congestion.
- Guarantee enough bandwidth and increase buffer space to accommodate bursts of traffic from fragile flows.
- Prevent congestion by dropping lower-priority packets before congestion occurs.
8. What configuration scenario would offer the most protection to SNMP get and set messages?
- SNMPv2 for in-band management with read-write community strings
- SNMPv1 with out-of-band management in a private subnet
- SNMPv3 configured with the auth security level
- SNMP community strings
9. Refer to the exhibit. The network administrator enters these commands into the R1 router:
R1# copy running-config tftp
Address or name of remote host [ ]?
When the router prompts for an address or remote host name, what IP address should the administrator enter at the prompt?
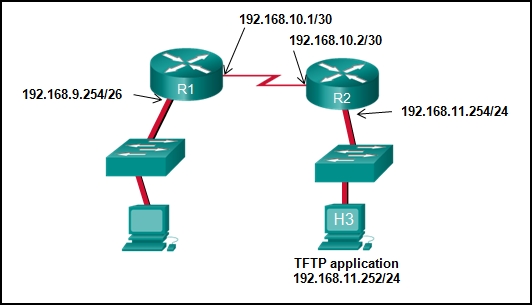
- 192.168.9.254
- 192.168.10.2
- 192.168.11.252
- 192.168.11.254
- 192.168.10.1
10. The command ntp server 10.1.1.1 is issued on a router. What impact does this command have?
- determines which server to send system log files to
- synchronizes the system clock with the time source with IP address 10.1.1.1
- identifies the server on which to store backup configurations
- ensures that all logging will have a time stamp associated with it
11. As the network administrator you have been asked to implement EtherChannel on the corporate network. What does this configuration consist of?
- providing redundant links that dynamically block or forward traffic
- grouping two devices to share a virtual IP address
- grouping multiple physical ports to increase bandwidth between two switches
- providing redundant devices to allow traffic to flow in the event of device failure
12. What is a definition of a two-tier LAN network design?
- access and core layers collapsed into one tier, and the distribution layer on a separate tier
- distribution and core layers collapsed into one tier, and the access layer on a separate tier
- access, distribution, and core layers collapsed into one tier, with a separate backbone layer
- access and distribution layers collapsed into one tier, and the core layer on a separate tier
13. What are two reasons to create a network baseline? (Choose two.)
- to select a routing protocol
- to determine what kind of equipment to implement
- to design a network according to a proper model
- to identify future abnormal network behavior
- to evaluate security vulnerabilities in the network
- to determine if the network can deliver the required policies
14. A computer can access devices on the same network but cannot access devices on other networks. What is the probable cause of this problem?
- The computer has an incorrect subnet mask.
- The computer has an invalid default gateway address.
- The cable is not connected properly to the NIC.
- The computer has an invalid IP address.
15. In which step of gathering symptoms does the network engineer determine if the problem is at the core, distribution, or access layer of the network?
- Gather information.
- Narrow the scope.
- Document the symptoms.
- Determine ownership.
- Determine the symptoms.
16. A network administrator is deploying QoS with the ability to provide a special queue for voice traffic so that voice traffic is forwarded before network traffic in other queues. Which queuing method would be the best choice?
- LLQ
- CBWFQ
- WFQ
- FIFO
17. What are two characteristics of voice traffic? (Choose two.)
- Voice traffic latency should not exceed 150 ms.
- Voice traffic is unpredictable and inconsistent.
- Voice traffic requires at least 384 kbs of bandwidth.
- Voice traffic consumes lots of network resources.
- Dropped voice packets are not retransmitted.
18. Which type of network traffic cannot be managed using congestion avoidance tools?
- TCP
- ICMP
- IP
- UDP
19. When QoS is implemented in a converged network, which two factors can be controlled to improve network performance for real-time traffic? (Choose two.)
- delay
- packet addressing
- jitter
- packet routing
- link speed
20. An administrator wants to replace the configuration file on a Cisco router by loading a new configuration file from a TFTP server. What two things does the administrator need to know before performing this task? (Choose two.)
- name of the configuration file that is currently stored on the router
- configuration register value
- name of the configuration file that is stored on the TFTP server
- router IP address
- TFTP server IP address
21. Refer to the exhibit. Which of the three Cisco IOS images shown will load into RAM?
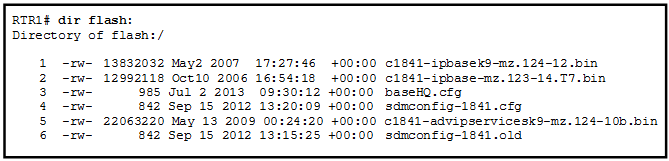
- The router selects an image depending on the boot system command in the configuration.
- The router selects an image depending on the value of the configuration register.
- The router selects the third Cisco IOS image because it is the most recent IOS image.
- The router selects the third Cisco IOS image because it contains the advipservicesk9 image.
- The router selects the second Cisco IOS image because it is the smallest IOS image.
22. Refer to the exhibit. What two types of devices are connected to R1? (Choose two.)
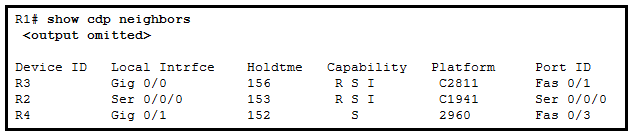
- switch
- hub
- router
- repeater
- Source Route Bridge
23. What are three functions provided by the syslog service? (Choose three.)
- to select the type of logging information that is captured
- to periodically poll agents for data
- to provide statistics on packets that are flowing through a Cisco device
- to provide traffic analysis
- to gather logging information for monitoring and troubleshooting
- to specify the destinations of captured messages
- gathering logging information
- selection of the type of information to be logged
- selection of the destination of the logged information
24. What is the function of the MIB element as part of a network management system?
- to collect data from SNMP agents
- to send and retrieve network management information
- to change configurations on SNMP agents
- to store data about a device
25. What network design would contain the scope of disruptions on a network should a failure occur?
- the reduction in the number of redundant devices and connections in the network core
- the installation of only enterprise class equipment throughout the network
- the deployment of distribution layer switches in pairs and the division of access layer switch connections between them
- the configuration of all access layer devices to share a single gateway
26. Which action should be taken when planning for redundancy on a hierarchical network design?
- add alternate physical paths for data to traverse the network
- continually purchase backup equipment for the network
- implement STP portfast between the switches on the network
- immediately replace a non-functioning module, service or device on a network
27. What are two benefits of extending access layer connectivity to users through a wireless medium? (Choose two.)
- increased flexibility
- increased network management options
- decreased number of critical points of failure
- reduced costs
- increased bandwidth availability
28. What is a basic function of the Cisco Borderless Architecture access layer?
- aggregates Layer 2 broadcast domains
- provides access to the user
- aggregates Layer 3 routing boundaries
- provides fault isolation
29. Which characteristic would most influence a network design engineer to select a multilayer switch over a Layer 2 switch?
- ability to have multiple forwarding paths through the switched network based on VLAN number(s)
- ability to build a routing table
- ability to provide power to directly-attached devices and the switch itself
- ability to aggregate multiple ports for maximum data throughput
30. Refer to the exhibit. Why are routers R1 and R2 not able to establish an OSPF adjacency?
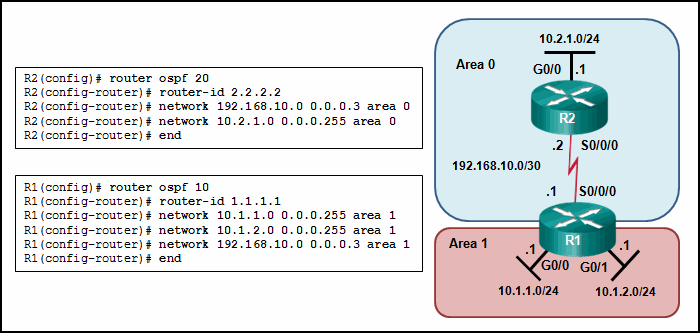
- The serial interfaces are not in the same area.
- The process numbers are not the same in both routers.
- A backbone router cannot establish an adjacency with an ABR router.
- The router ID values are not the same in both routers.
31. When is the most appropriate time to measure network operations to establish a network performance baseline?
- whenever high network use is detected, so that how the network performs under stress can be monitored
- during quiet vacation periods, so that the level of non-data traffic can be determined
- at the same time each day across a set period of average working days, so that typical traffic patterns can be established
- at random times during a 10 week period, so that abnormal traffic levels can be detected
32. Refer to the exhibit. A user has configured a NIC on the PC as shown but finds that the PC is unable to access the Internet. What is the problem?

- The preferred DNS address is incorrect.
- The default gateway address is incorrect.
- The settings were not validated upon exit.
- There should not be an alternate DNS server.
33. Refer to the exhibit. A network engineer configured an ACL preventing Telnet and HTTP access to the HQ web server from guest users in the Branch LAN. The address of the web server is 192.168.1.10 and all guest users are assigned addresses in the 192.168.10.0/24 network. After implementing the ACL, no one can access any of the HQ servers. What is the problem?
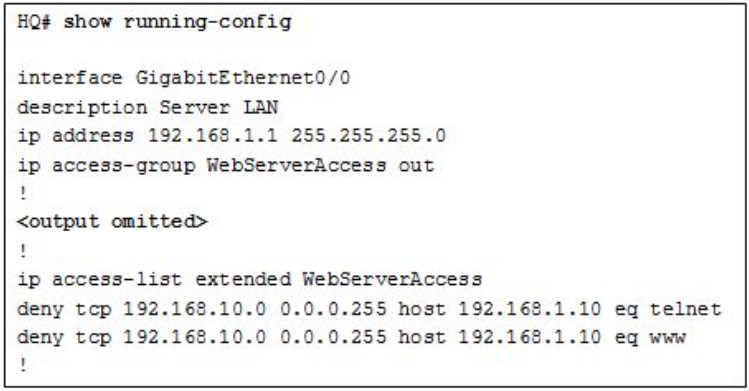
- Inbound ACLs must be routed before they are processed.
- The ACL is implicitly denying access to all the servers.
- Named ACLs require the use of port numbers.
- The ACL is applied to the interface using the wrong direction.
34. Refer to the exhibit. A network administrator has configured OSPFv2 on the two Cisco routers as shown. PC1 is unable to connect to PC2. What should the administrator do first when troubleshooting the OSPFv2 implementation?
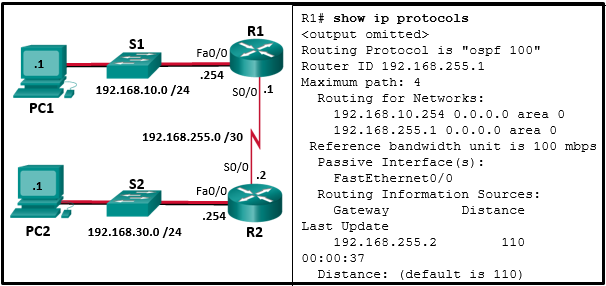
- Disconnect the serial link between router R1 and R2.
- Turn off OSPFv2.
- Implement the network 192.168.255.0 0.0.0.3 area 0 command on router R1.
- Test Layer 3 connectivity between the directly connected routers.
35. What type of traffic is described as requiring latency to be no more than 150 milliseconds (ms)?
- voice
- video
- data
36. A network manager wants to add a time to log messages so that there is record of when the message was generated. What command should the administrator use on a Cisco router?
- show cdp interface
- ntp server 10.10.14.9
- service timestamps log datetime
- clock timezone PST -7
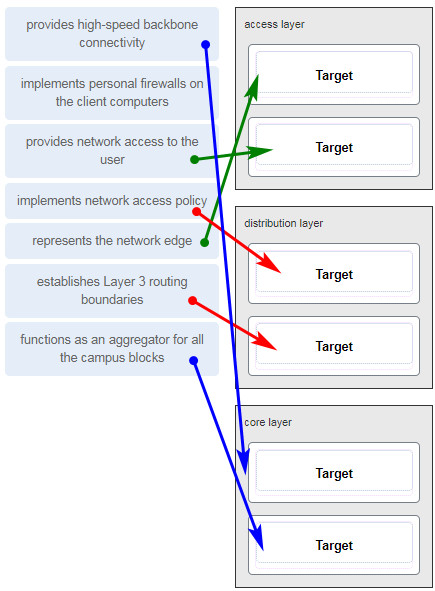
37. Match the functions to the corresponding layers. (Not all options are used.)
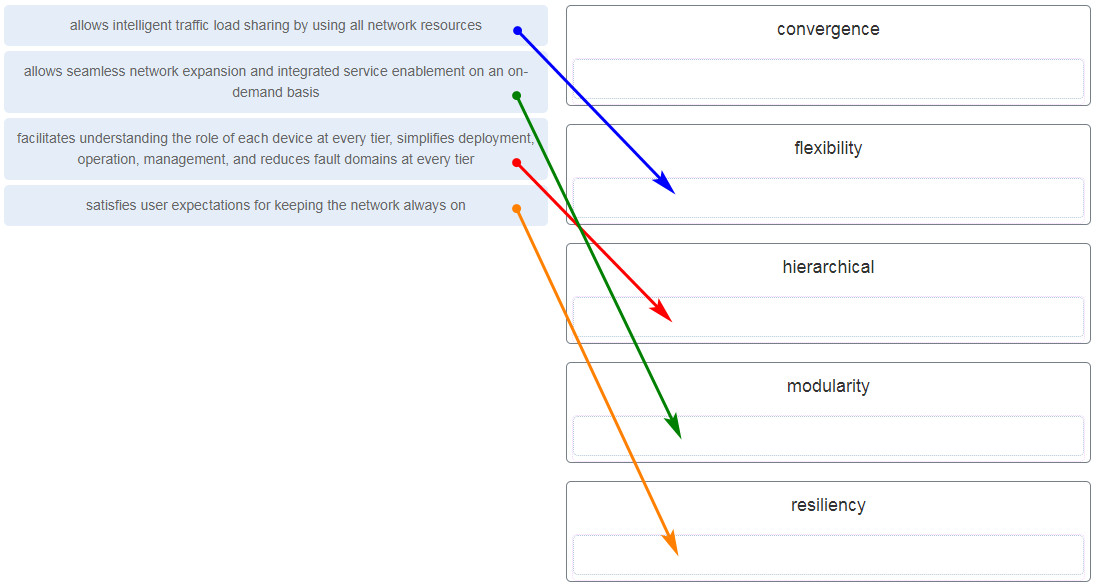
38. Match the borderless switched network guideline description to the principle. (Not all options are used.)
39. What are two characteristics of the best-effort QoS model? (Choose two.)
- It allows end hosts to signal their QoS needs to the network.
- It uses a connection-oriented approach with QoS.
- It provides preferential treatment for voice packets.
- It does not provide a delivery guarantee for packets.
- It treats all network packets in the same way.
40. Why is QoS an important issue in a converged network that combines voice, video, and data communications?
- Data communications are sensitive to jitter.
- Legacy equipment is unable to transmit voice and video without QoS.
Correct Response - Voice and video communications are more sensitive to latency.
- Data communications must be given the first priority.
41. A network administrator configures a router with the command sequence:
R1(config)# boot system tftp://c1900-universalk9-mz.SPA.152-4.M3.bin R1(config)# boot system rom
What is the effect of the command sequence?
- On next reboot, the router will load the IOS image from ROM.
- The router will search and load a valid IOS image in the sequence of flash, TFTP, and ROM.
- The router will copy the IOS image from the TFTP server and then reboot the system.
- The router will load IOS from the TFTP server. If the image fails to load, it will load the IOS image from ROM.
42. Which statement describes SNMP operation?
- An SNMP agent that resides on a managed device collects information about the device and stores that information remotely in the MIB that is located on the NMS.
- A set request is used by the NMS to change configuration variables in the agent device.
- An NMS periodically polls the SNMP agents that are residing on managed devices by using traps to query the devices for data.
- A get request is used by the SNMP agent to query the device for data.
43. Refer to the exhibit. A network administrator issues the show lldp neighbors command on a switch. What are two conclusions that can be drawn? (Choose two.)
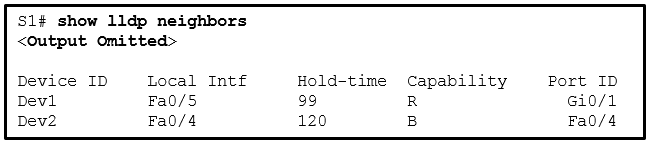
- Dev1 is connected to interface Fa0/5 of S1.
- Dev1 is a switch with mixed types of interfaces.
- Dev2 is a switch.
- Dev1 is connected to interface Fa0/4 of Dev2.
- S1 has only two interfaces.
44. What are the three layers of the switch hierarchical design model? (Choose three.)
- distribution
- network access
- data link
- enterprise
- access
- core
45. Refer to the exhibit. Which devices exist in the failure domain when switch S3 loses power?
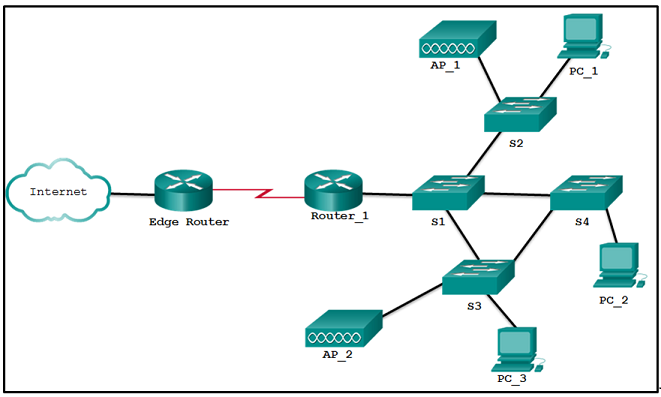
- S4 and PC_2
- PC_3 and PC_2
- PC_3 and AP_2
- S1 and S4
- AP_2 and AP_1
46. A network designer is considering whether to implement a switch block on the company network. What is the primary advantage of deploying a switch block?
- This is network application software that prevents the failure of a single network device.
- The failure of a switch block will not impact all end users.
- This is a security feature that is available on all new Catalyst switches.
- A single core router provides all the routing between VLANs.
47. Which troubleshooting tool would a network administrator use to check the Layer 2 header of frames that are leaving a particular host?
- knowledge base
- protocol analyzer
- CiscoView
- baselining tool
48. Refer to the exhibit. R1 and R3 are connected to each other via the local serial 0/0/0 interface. Why are they not forming an adjacency?

- They have different routing processes.
- They have different router IDs.
- They are in different subnets.
- The connecting interfaces are configured as passive.
49. What type of traffic is described as not resilient to loss?
- video
- data
- voice
50. A network manager wants lists the contents of flash. What command should the administrator use on a Cisco router?
- show file systems
- dir
- lldp enable
- service timestamps log datetime
51. Voice packets are being received in a continuous stream by an IP phone, but because of network congestion the delay between each packet varies and is causing broken conversations. What term describes the cause of this condition?
- buffering
- latency
- queuing
- jitter
52. A user is unable to reach the website when typing http://www.cisco.com in a web browser, but can reach the same site by typing http://72.163.4.161 . What is the issue?
- DHCP
- DNS
- Default Gateway
- TCP/IP Protocol stack
53. What type of traffic is described as tending to be unpredictable, inconsistent, and bursty?
- Audio
- Video
- Data
- Voice
54. A network manager wants to determine the size of the Cisco IOS image file on the networking device. What command should the administrator use on a Cisco router?
- show flash:0
- copy flash: tftp:
- config-register 0x2102
- confreg 0x2142
55. What is the principle that is applied when a network technician is troubleshooting a network fault by using the divide-and-conquer method?
- Testing is performed at Layer 7 and at Layer 1, then at Layers 6 and 2, and so on, working towards the middle of the stack until all layers are verified as operational.
- Once it is verified that components in a particular layer are functioning properly, it can then be assumed that components in the layers below it are also functional.
- Testing is performed at all layers of the OSI model until a non-functioning component is found.
- Once it is verified that a component in a particular layer is functioning properly, testing can then be performed on any other layer.
56. Which queuing algorithm has only a single queue and treats all packets equally?
- CBWFQ
- FIFO
- LLQ
- WFQ
57. What type of traffic is described as traffic that requires at least 30 Kbps of bandwidth?
- voice
- data
- video
58. What type of traffic is described as being able to tolerate a certain amount of latency, jitter, and loss without any noticeable effects?
- voice
- video
- data
59. A network manager wants to view the amount of available and free memory, the type of file system, and its permissions. What command should the administrator use on a Cisco router?
- ntp server 10.10.14.9
- lldp enable
- clock timezone PST -7
- show file systems
60. What type of traffic is described as requiring latency to be no more than 400 milliseconds (ms)?
- voice
- data
- video
61. What type of traffic is described as consisting of traffic that requires a higher priority if interactive?
- data
- voice
- video
62. A network manager wants to configure the router to load a new image from flash during bootup. What command should the administrator use on a Cisco router?
- copy flash: tftp:
- boot system
- clock set 14:25:00 nov 13 2018
- copy tftp startup-config
63. What type of traffic is described as predictable and smooth?
- data
- video
- voice
64. A network manager wants to ensure that the device will ignore the startup config file during startup and bypass the required passwords. What command should the administrator use on a Cisco router?
- copy usbflash0:/R1-Config
- copy running-config tftp
- confreg 0x2142
- config-register 0x2102
65. What type of traffic is described as having a high volume of data per packet?
- video
- voice
- data
66. A network manager wants to backup the running configuration to a file server. What command should the administrator use on a Cisco router?
- cd usbflash0:
- show file systems
- copy running-config tftp
- dir
67. What type of traffic is described as consisting of traffic that gets a lower priority if it is not mission-critical?
- voice
- data
- video

What type of traffic is described as traffic that requires at least 30 Kbps of bandwidth?
(X) voice
data
video
Which queuing algorithm has only a single queue and treats all packets equally?
CBWFQ
(X) FIFO
LLQ
WFQ
What is the principle that is applied when a network technician is troubleshooting a network fault by using the divide-and-conquer method?
Testing is performed at Layer 7 and at Layer 1, then at Layers 6 and 2, and so on, working towards the middle of the stack until all layers are verified as operational.
Once it is verified that components in a particular layer are functioning properly, it can then be assumed that components in the layers below it are also functional.
Testing is performed at all layers of the OSI model until a non-functioning component is found.
X Once it is verified that a component in a particular layer is functioning properly, testing can then be performed on any other layer.
A network manager wants to determine the size of the Cisco IOS image file on the networking device. What command should the administrator use on a Cisco router?
X show flash:0
copy flash: tftp:
config-register 0x2102
confreg 0x2142
What type of traffic is described as tending to be unpredictable, inconsistent, and bursty?
(1). Audio
(2). Video
(3). Data
(4). Voice
The answer is Video
A user is unable to reach the website when typing http://www.cisco.com in a web browser, but can reach the same site by typinghttp://72.163.4.161 . What is the issue?
(1). DHCP
(2). DNS
(3). Default Gateway
(4). TCP/IP Protocol stack
The answer is DNS.
What is the principle that is applied when a network technician is troubleshooting a network fault by using the divide-and-conquer method?
What is answer?
Una vez que se verifica que los componentes de una capa en particular funcionan correctamente, se puede suponer que los componentes en las capas inferiores también son funcionales.
What type of traffic is described as being able to tolerate a certain amount of latency, jitter, and loss without any noticeable effects?
voice
data
video
A network manager wants to view the amount of available and free memory, the type of file system, and its permissions. What command should the administrator use on a Cisco router?
clock timezone PST -7
-> show file systems
ntp server 10.10.14.9
lldp enable
10
What type of traffic is described as requiring latency to be no more than 400 milliseconds (ms)?
I chose data
11
A network manager wants to view the amount of available and free memory, the type of file system, and its permissions. What command should the administrator use on a Cisco router?
show file systems
clock timezone PST -7
copy usbflash0:/R1-Config
copy running-config tftp
Answer: show file systems
A Network maager wants to view the amount of available and free memory,the type of file system,and it’s permissions.what command should the administrator use on a cisco router?
show file system
lldp enable
clock timezone PST-7
ntp server 10.10.14.9
The Answer is :
show file system 🙂
¿Qué tipo de tráfico se describe como que requiere una latencia de no más de 400 milisegundos (ms)?
(respueta) vídeo
datos
voz
Questions to correct :
Q 55 : What is the principle that is applied when a network technician is troubleshooting a network fault by using the divide-and-conquer method?
the answer is : Once it is verified that components in a particular layer are functioning properly, it can then be assumed that components in the layers below it are also functional.
Additional Question:
What type of traffic is described as consisting of traffic that requires a higher priority if interactive?
1-voice
2-vedio
3-data
The answer is 3 : data
That is based on the exam i have already did and received a feedback of the wrong questions.
Best Regards
Eman
Fixed! Thanks you so much!
What type of traffic is described as having a high volume of data per packet?
A user is unable to reach the website when typing http://www.cisco.com in a web browser, but can reach the same site by typing http://72.163.4.161 . What is the issue?
A network manager wants to configure the router to load a new image from flash during bootup. What command should the administrator use on a Cisco router?
A network manager wants to configure the router to load a new image from flash during bootup. What command should the administrator use on a Cisco router?
* clock set 14:25:00 nov 13 2018
* copy flash: tftp:
* copy tftp startup-config
* boot system
Boot system
What type of traffic is described as predictable and smooth?
* data
* video
* voice
What type of traffic is described as having a high volume of data per packet?
A network manager wants to configure the router to load a new image from flash during bootup. What command should the administrator use on a Cisco router?
What type of traffic is described as predictable and smooth?
What type of traffic is described as predictable and smooth?
A user is unable to reach the website when typing http://www.cisco.com in a web browser, but can reach the same site by typing http://72.163.4.161 . What is the issue?
DNS
TCP/IP protocol stack
DHCP
default gateway
DNS
A network manager wants to ensure that the device will ignore the startup config file during startup and bypass the required passwords. What command should the administrator use on a Cisco router?
Confreg 0x2142
A user is unable to reach the website when typinghttp://www.cisco.com in a web browser, but can reach the same site by typing http://72.163.4.161 . What is the issue?
DNS. This question is in the list.
What type of traffic is described as consisting of traffic that gets a lower priority if it is not mission-critical?
Which true answer? @@
The answer is data.
Its data
Thanks for all 🙂
A network manager wants to backup the running configuration to a file server. What command should the administrator use on a Cisco router?
What type of traffic is described as not resilient to loss?
data
video
voice
cual es la correcta?
digo esto porque en otras paginas web, dicen que la correcta es VIDEO, aunque sabemos que es DATOS.
digo esto debido a que le EXAMEN de CISCO no es perfecto y tiene errores….
What type of traffic is described as not resilient to loss?
data
video
voice
how long ago did you review the cisco exam to verify the answer please
According to other pages they indicate that the correct one that Cisco has in its exam is: VIDEO, although we know that it is not the correct one, we also have to take into account that the Cisco EXAM is not PERFECT and has errors …..
So I ask which is the correct one according to the last CISCO exam please.
I found the answer to that question here:
https://itexamanswers.net/ccna-3-v7-0-curriculum-module-9-qos-concepts.html#section-9-2-5-data
54What type of traffic is described as requiring latency to be no more than 400 milliseconds (ms)?
Voice does take priority over video when it comes to QoS. LLQ provides voice with the highest priority. However, video is still less resilient than voice because of the amount of data that each video packet contains. This makes video traffic more resource demanding, meaning it will suffer more when packets are dropped. CCNA states that voice traffic should not have loss more than 1%, and video traffic should not have loss more than 0.1%-1%.