3.5.5 Packet Tracer – Configure DTP (Instructor Version)
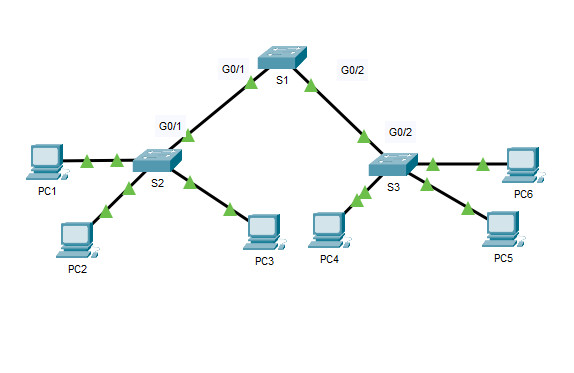
Addressing Table
| Device | Interface | IP Address | Subnet Mask |
|---|---|---|---|
| PC1 | NIC | 192.168.10.1 | 255.255.255.0 |
| PC2 | NIC | 192.168.20.1 | 255.255.255.0 |
| PC3 | NIC | 192.168.30.1 | 255.255.255.0 |
| PC4 | NIC | 192.168.30.2 | 255.255.255.0 |
| PC5 | NIC | 192.168.20.2 | 255.255.255.0 |
| PC6 | NIC | 192.168.10.2 | 255.255.255.0 |
| S1 | VLAN 99 | 192.168.99.1 | 255.255.255.0 |
| S2 | VLAN 99 | 192.168.99.2 | 255.255.255.0 |
| S3 | VLAN 99 | 192.168.99.3 | 255.255.255.0 |
Objectives
- Configure static trunking
- Configure and Verify DTP
Background / Scenario
As the number of switches in a network increases, the administration necessary to manage the VLANs and trunks can be challenging. To ease some of the VLAN and trunking configurations, trunk negotiation between network devices is managed by the Dynamic Trunking Protocol (DTP), and is automatically enabled on Catalyst 2960 and Catalyst 3650 switches.
In this activity, you will configure trunk links between the switches. You will assign ports to VLANs and verify end-to-end connectivity between hosts in the same VLAN. You will configure trunk links between the switches, and you will configure VLAN 999 as the native VLAN.
Instructions
Part 1: Verify VLAN configuration.
Verify the configured VLANs on the switches.
a. On S1, go to privileged EXEC mode and enter the show vlan brief command to verify the VLANs that are present.
S1# show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4
Fa0/5, Fa0/6, Fa0/7, Fa0/8
Fa0/9, Fa0/10, Fa0/11, Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gig0/1, Gig0/2
99 Management active
999 Native active
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
b. Repeat Step 1a on S2 and S3.
What VLANs are configured on the switches?
Part 2: Create additional VLANs on S2 and S3.
a. On S2, create VLAN 10 and name it Red.
S2(config)# vlan 10 S2(config-vlan)# name Red
b. Create VLANs 20 and 30 according to the table below.
| VLAN Number | VLAN Name |
|---|---|
| 10 | Red |
| 20 | Blue |
| 30 | Yellow |
S2(config-vlan)#vlan 20 S2(config-vlan)#name Blue S2(config-vlan)#vlan 30 S2(config-vlan)#name Yellow
c. Verify the addition of the new VLANs. Enter show vlan brief at the privileged EXEC mode.
S2#show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4
Fa0/5, Fa0/6, Fa0/7, Fa0/8
Fa0/9, Fa0/10, Fa0/11, Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gig0/1, Gig0/2
10 Red active
20 Blue active
30 Yellow active
99 Management active
999 Native active
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
In addition to the default VLANs, which VLANs are configured on S2?
d. Repeat the previous steps to create the additional VLANs on S3.
S3(config)#vlan 10 S3(config-vlan)#name Red S3(config-vlan)#vlan 20 S3(config-vlan)#name Blue S3(config-vlan)#vlan 30 S3(config-vlan)#name Yellow
Part 3: Assign VLANs to Ports
Use the switchport mode access command to set access mode for the access links. Use the switchport access vlan vlan-id command to assign a VLAN to an access port.
| Ports | Assignments | Network |
|---|---|---|
| S2 F0/1 – 8 S3 F0/1 – 8 |
VLAN 10 (Red) | 192.168.10.0 /24 |
| S2 F0/9 – 16 S3 F0/9 – 16 |
VLAN 20 (Blue) | 192.168.20.0 /24 |
| S2 F0/17 – 24 S3 F0/17 – 24 |
VLAN 30 (Yellow) | 192.168.30.0 /24 |
a. Assign VLANs to ports on S2 using assignments from the table above.
S2(config-if)# interface range f0/1 - 8 S2(config-if-range)# switchport mode access S2(config-if-range)# switchport access vlan 10 S2(config-if-range)# interface range f0/9 -16 S2(config-if-range)# switchport mode access S2(config-if-range)# switchport access vlan 20 S2(config-if-range)# interface range f0/17 - 24 S2(config-if-range)# switchport mode access S2(config-if-range)# switchport access vlan 30
b. Assign VLANs to ports on S3 using the assignments from the table above.
S3(config)#interface range f0/1-8 S3(config-if-range)#switchport mode access S3(config-if-range)#switchport access vlan 10 S3(config-if-range)#interface range f0/9-16 S3(config-if-range)#switchport mode access S3(config-if-range)#switchport access vlan 20 S3(config-if-range)#interface range f0/17-24 S3(config-if-range)#switchport mode access S3(config-if-range)#switchport access vlan 30
Now that you have the ports assigned to VLANs, try to ping from PC1 to PC6.
Was the ping successful? Explain.
Part 4: Configure Trunks on S1, S2, and S3.
Dynamic trunking protocol (DTP) manages the trunk links between Cisco switches. Currently, all the switchports are in the default trunking mode, which is dynamic auto. In this step, you will change the trunking mode to dynamic desirable for the link between switches S1 and S2. The link between switches S1 and S3 will be set as a static trunk. Use VLAN 999 as the native VLAN in this topology.
a. On switch S1, configure the trunk link to dynamic desirable on the GigabitEthernet 0/1 interface. The configuration of S1 is shown below.
S1(config)# interface g0/1 S1(config-if)# switchport mode dynamic desirable
What will be the result of trunk negotiation between S1 and S2?
b. On switch S2, verify that the trunk has been negotiated by entering the show interfaces trunk command. Interface GigabitEthernet 0/1 should appear in the output.
S2>enable S2#show interface trunk Port Mode Encapsulation Status Native vlan Gig0/1 auto n-802.1q trunking 1 Port Vlans allowed on trunk Gig0/1 1-1005 Port Vlans allowed and active in management domain Gig0/1 1,10,20,30,99,999 Port Vlans in spanning tree forwarding state and not pruned Gig0/1 1,10,20,30,99,999
What is the mode and status for this port?
c. For the trunk link between S1 and S3, configure interface GigabitEthernet 0/2 as a static trunk link on S1.
In addition, disable DTP negotiation on interface G0/2 on S1.
S1(config)# interface g0/2 S1(config-if)# switchport mode trunk S1(config-if)# switchport nonegotiate
d. Use the show dtp command to verify the status of DTP.
S1# show dtp
Global DTP information
Sending DTP Hello packets every 30 seconds
Dynamic Trunk timeout is 300 seconds
1 interfaces using DTP
e. Verify trunking is enabled on all the switches using the show interfaces trunk command.
S1# show interfaces trunk Port Mode Encapsulation Status Native vlan Gig0/1 desirable n-802.1q trunking 1 Gig0/2 on 802.1q trunking 1 Port Vlans allowed on trunk Gig0/1 1-1005 Gig0/2 1-1005 Port Vlans allowed and active in management domain Gig0/1 1,99,999 Gig0/2 1,99,999 Port Vlans in spanning tree forwarding state and not pruned Gig0/1 1,99,999 Gig0/2 1,99,999
What is the native VLAN for these trunks currently?
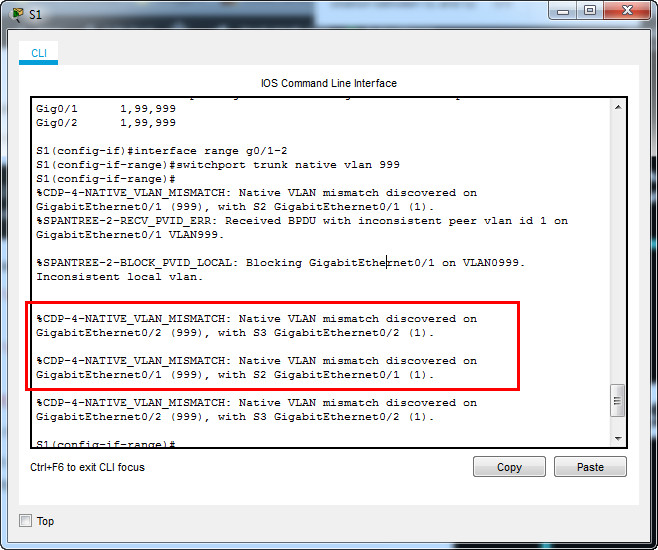
f. Configure VLAN 999 as the native VLAN for the trunk links on S1.
S1(config)# interface range g0/1 - 2 S1(config-if-range)# switchport trunk native vlan 999
What messages did you receive on S1? How would you correct it?
g. On S2 and S3, configure VLAN 999 as the native VLAN.
[tabs]
[tab title=”S2″]
S2(config)#interface g0/1 S2(config-if)#switchport mode trunk S2(config-if)#switchport trunk native vlan 999
[/tab]
[tab title=”S3″]
S3(config)#interface g0/2 S3(config-if)#switchport mode trunk S3(config-if)#switchport trunk native vlan 999
[/tab]
[/tabs]
h. Verify trunking is successfully configured on all the switches. You should be able ping one switch from another switch in the topology using the IP addresses configured on the SVI.
S1#ping 192.168.99.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.99.2, timeout is 2 seconds: ..!!! Success rate is 60 percent (3/5), round-trip min/avg/max = 0/0/0 ms S1#ping 192.168.99.3 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.99.3, timeout is 2 seconds: ..!!! Success rate is 60 percent (3/5), round-trip min/avg/max = 0/0/0 ms S1#
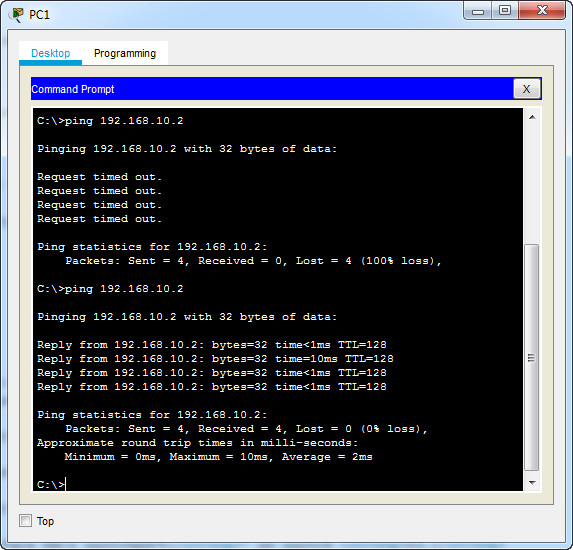
i. Attempt to ping from PC1 to PC6.
Why was the ping unsuccessful? (Hint: Look at the ‘show vlan brief’ output from all three switches. Compare the outputs from the ‘show interface trunk’ on all switches.)
S1#show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4
Fa0/5, Fa0/6, Fa0/7, Fa0/8
Fa0/9, Fa0/10, Fa0/11, Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
99 Management active
999 Native active
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
S1#show int trun
Port Mode Encapsulation Status Native vlan
Gig0/1 desirable n-802.1q trunking 999
Gig0/2 on 802.1q trunking 999
Port Vlans allowed on trunk
Gig0/1 1-1005
Gig0/2 1-1005
Port Vlans allowed and active in management domain
Gig0/1 1,99,999
Gig0/2 1,99,999
Port Vlans in spanning tree forwarding state and not pruned
Gig0/1 1,99,999
Gig0/2 1,99,999
j. Correct the configuration as necessary.
S1(config)#vlan 10 S1(config-vlan)#name Red S1(config-vlan)#vlan 20 S1(config-vlan)#name Blue S1(config-vlan)#vlan 30 S1(config-vlan)#name Yellow
Try Ping again from PC1 to PC6 –> successful
Part 5: Reconfigure trunk on S3.
a. Issue the ‘show interface trunk’ command on S3.
What is the mode and encapsulation on G0/2?
b. Configure G0/2 to match G0/2 on S1.
S3(config)#interface g0/2 S3(config-if)#switchport nonegotiate
What is the mode and encapsulation on G0/2 after the change?
c. Issue the command ‘show interface G0/2 switchport’ on switch S3.
S3#show interfaces g0/2 switchport
Name: Gig0/2
Switchport: Enabled
Administrative Mode: trunk
Operational Mode: trunk
Administrative Trunking Encapsulation: dot1q
Operational Trunking Encapsulation: dot1q
Negotiation of Trunking: Off
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 999 (Native)
Voice VLAN: none
Administrative private-vlan host-association: none
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk private VLANs: none
Operational private-vlan: none
Trunking VLANs Enabled: All
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Protected: false
Unknown unicast blocked: disabled
Unknown multicast blocked: disabled
Appliance trust: none
What is the ‘Negotiation of Trunking’ state displayed?
Part 6: Verify end to end connectivity.
a. From PC1 ping PC6. –> successful
b. From PC2 ping PC5. –> successful
c. From PC3 ping PC4. –> successful
Full Script
Switch S1
enable config t vlan 10 name Red vlan 20 name Blue vlan 30 name Yellow interface g0/1 switchport mode dynamic desirable switchport trunk native vlan 999 interface g0/2 switchport mode trunk switchport trunk native vlan 999 switchport nonegotiate end
Switch S2
enable config t vlan 10 name Red vlan 20 name Blue vlan 30 name Yellow interface range f0/1 - 8 switchport mode access switchport access vlan 10 interface range f0/9 - 16 switchport mode access switchport access vlan 20 interface range f0/17 - 24 switchport mode access switchport access vlan 30 interface GigabitEthernet0/1 switchport mode dynamic auto switchport trunk native vlan 999 end
Switch S3
enable config t vlan 10 name Red vlan 20 name Blue vlan 30 name Yellow interface range f0/1 - 8 switchport mode access switchport access vlan 10 interface range f0/9 - 16 switchport mode access switchport access vlan 20 interface range f0/17 - 24 switchport mode access switchport access vlan 30 interface GigabitEthernet0/2 switchport trunk native vlan 999 switchport mode trunk switchport nonegotiate end
Download PDF & PKA file:
[sociallocker id=”54558″]
[wpdm_package id=’38979′]
[wpdm_package id=’38981′]
[/sociallocker]
[alert-note][one_half]
Previous Lab
3.4.5 Packet Tracer – Configure Trunks
[/one_half][one_half_last]
Next Lab
3.6.1 Packet Tracer – Implement VLANs and Trunking
[/one_half_last][/alert-note]

where are the answers to the questions?
yeah were the answers ever since my classess went remote my instructors been going to these things religously
You seriously are such a lifesaver. I can learn so much from these things!