[tabs][tab title=”TYPE A”]
CCNA Routing and Switching
Routing and Switching Essentials
Chapter 2 SIC: Static Routing and Basic Router Configuration
A few things to keep in mind while completing this activity:
- Do not use the browser Backbutton or close or reload any exam windows during the exam.
- Do not close Packet Tracer when you are done. It will close automatically.
- Click the Submit Assessmentbutton in the browser window to submit your work.
Introduction
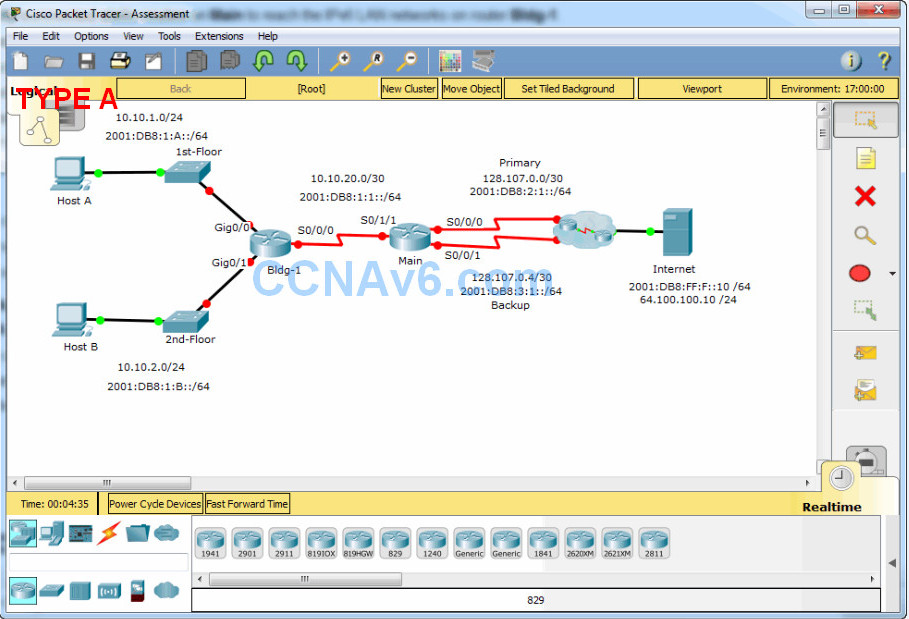
New Corp. is preparing to convert its network to use IPv6. It is experimenting with the transition, and has set up a test network that is configured with both IPv4 and IPv6 addressing on all hosts and device interfaces. The company will be using default, static, and floating static routes to create connectivity in the network.
In this practice skills assessment, you will configure the New Corp. network with IPv4 and IPv6 interface and host addressing, and IPv4 and IPv6 default, static, and floating static routes. In addition, you will complete a basic configuration on a router.
You are not required to configure the Internet server, or the switches.
Note: In order to keep the assessment activity as brief as possible, you will only be partially configuring some devices, as directed in the instructions. In a real network, all devices would be fully configured to function in the network. You are only responsible for completing the tasks covered in the instructions. Any configuration that you do beyond the requirements will not result in additional credit.
All IOS device configurations should be completed from a direct terminal connection to the device console. In addition, many values that are required to complete the configurations have not been given to you. In those cases, create the values that you need to complete the requirements.
You will practice and be assessed on the following skills:
- Basic router configuration
- IPv4 and IPv6 router interface activation and addressing
- Directly attached IPv4 and IPv6 static route configuration
- Directly attached IPv4 and IPv6 default route configuration
- Directly attached IPv4 and IPv6 floating static route configuration
- IPv4 and IPv6 host addressing
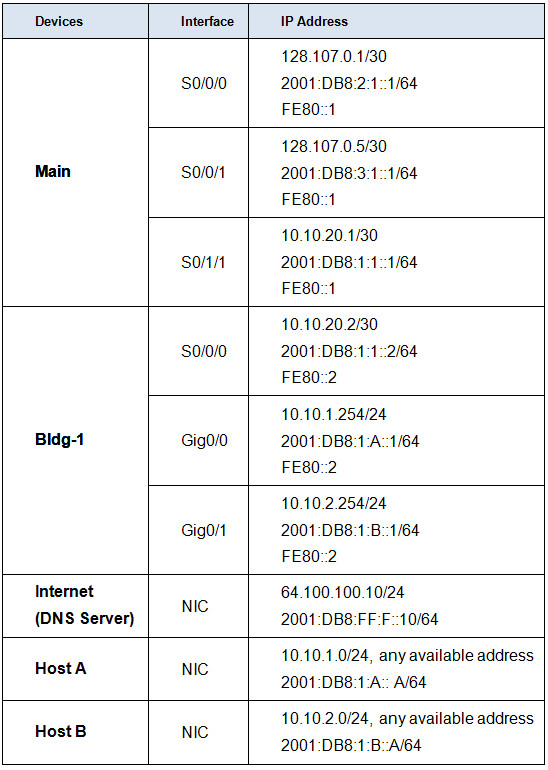
Addressing Table
Instructions
Step 1: Basic Device Configuration
Perform a basic device configuration on Main.
- Configure the router hostname to the value in the addressing table.
- Prevent the router from attempting to resolve unrecognized CLI entries as domain names.
- Protect device configurations from unauthorized access with the encrypted secret password of cisco.
- Secure the router console and vty lines with the password class.
- Prevent all passwords from being viewed in clear text in device configuration files.
- Add a message-of-the-day banner of your choice.
- Provide descriptions on all active interfaces.
Step 2: Configure Default, Static, and Floating Static Routes.
Configure static, default, and floating static routes on the routers.
Main:
- Configure interfaces of the Main router with IPv4 and IPv6 addressing based on the Addressing Table.
- Configure two directly connected static routes on Main to reach the two IPv4 LAN networks on router Bldg-1.
- Configure two directly connected static routes on Main to reach the IPv6 LAN networks on router Bldg-1.
- Configure directly connected IPv4 default static routes to reach hosts outside of the network.
- Configure the primary path through Serial0/0/0.
- Configure a floating default static route for the backup path through Serial0/0/1 with a metric of 2.
- Configure directly connected IPv6 default static routes to reach hosts outside of the network.
- Configure the Primary path through Serial0/0/0.
- Configure the Backup path through Serial0/0/1 with a metric of 2.
Bldg-1:
- Configure interfaces on the Bldg-1 router with IPv4 and IPv6 addressing based on the Addressing Table.
- Configure a directly connected IPv4 default static route on Bldg-1 to reach the Internet.
- Configure a directly connected IPv6 default static route on Bldg-1 to reach the Internet.
Step 3: Configure Host Addressing
- Configure the Host A and Host B hosts with both IPv4 and IPv6 addresses based on the Addressing Table.
- IPv6 default gateway addresses should be the link local address of the LAN router interface.
- Configure the DNS server address for both IPv4 and IPv6.
- All PC hosts should be able to reach the Internet server.
Intruction – Answers Script
Main or Central (Router 1)
en
conf ter
hostname Main (Central)
no ip domain-lookup
enable secret cisco
line console 0
password class
login
line vty 0 15
password cisco
login
exit
service password-encryption
banner motd $CCNAv6.com$
int s0/0/0
description PRIMARY CONNECTION
ip address 128.107.0.1 255.255.255.252
ipv6 address 2001:DB8:2:1::1/64
ipv6 address FE80::1 link-local
no shutdown
int s0/0/1
description BACKUP CONNECTION
ip address 128.107.0.5 255.255.255.252
ipv6 address 2001:DB8:3:1::1/64
ipv6 address FE80::1 link-local
no shutdown
int s0/1/1
description Connect to Bldg-1
ip address 10.10.20.1 255.255.255.252
ipv6 address 2001:DB8:1:1::1/64
ipv6 address FE80::1 link-local
no shutdown
exit
ip route 10.10.1.0 255.255.255.0 s0/1/1
ip route 10.10.2.0 255.255.255.0 s0/1/1
ipv6 route 2001:DB8:1:A::/64 s0/1/1
ipv6 route 2001:DB8:1:B::/64 s0/1/1
ip route 0.0.0.0 0.0.0.0 s0/0/0
ip route 0.0.0.0 0.0.0.0 s0/0/1 2
ipv6 route ::/0 s0/0/0
ipv6 route ::/0 s0/0/1 2
ipv6 unicast-routing
Bldg-1 or Quest (Router 2)
enable conf terminal int s0/0/0 ip address 10.10.20.2 255.255.255.252 ipv6 address 2001:DB8:1:1::2/64 ipv6 address FE80::2 link-local no shutdown int g0/0 ip address 10.10.1.254 255.255.255.0 ipv6 address 2001:DB8:1:A::1/64 ipv6 address FE80::2 link-local no shutdown int g0/1 ip address 10.10.2.254 255.255.255.0 ipv6 address 2001:DB8:1:B::1/64 ipv6 address FE80::2 link-local no shutdown exit int s0/0/0 description Connection to Main int g0/0 description LAN A int g0/1 description LAN B exit ip route 0.0.0.0 0.0.0.0 s0/0/0 ipv6 route ::/0 s0/0/0
Configure Host Addressing
Host A:
IPv4 Configuration:
– IP Address: 10.10.1.10
– Subnet Mask: 255.255.255.0
– Gateway: 10.10.1.254
– DNS Server: 64.100.100.10
IPv6 Configuration:
– IPv6 Address: 2001:DB8:1:A::A / 64
– IPv6 Gateway: FE80::2
– IPv6 DNS Server: 2001:DB8:FF:F::10
Host B:
IPv4 Configuration:
– IP Address: 10.10.2.10
– Subnet Mask: 255.255.255.0
– Gateway: 10.10.2.254
– DNS Server: 64.100.100.10
IPv6 Configuration:
– IPv6 Address: 2001:DB8:1:B::A / 64
– IPv6 Gateway: FE80::2
– IPv6 DNS Server: 2001:DB8:FF:F::10
[/tab]
[tab title=”TYPE B”]
CCNA Routing and Switching
Introduction to Networks
ITN Practice Skills Assessment – Packet Tracer
A few things to keep in mind while completing this activity:
1. Do not use the browser Back button or close or reload any exam windows during the exam.
2. Do not close Packet Tracer when you are done. It will close automatically.
3. Click the Submit Assessment button in the browser window to submit your work.
Introduction
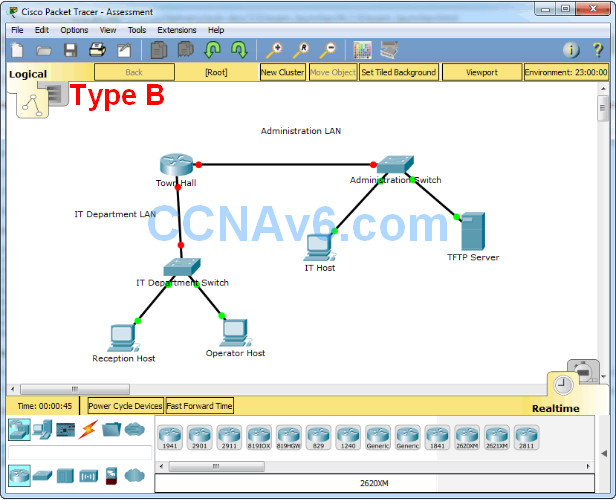
In this assessment, you will configure devices in an IPv4/IPv6 network. For the sake of time, you will not be asked to perform all configurations on all network devices as you may be required to do in a real network or other assessment. Instead, you will use the skills and knowledge that you have learned in the labs in this course to configure the Town Hall router. In addition, you will address the hosts on two LANs with IPv4 and IPv6 addresses, activate and address the management interface of the Administration Switch, and back up a device configuration to a TFTP server.
You will receive one of several topologies.
You are not required to configure the IT Department Switch, and you will not be able to access it in this practice skills assessment activity.
All IOS device configurations should be completed from a direct terminal connection to the device console. In addition, many values that are required to complete the configurations have not been given to you. In those cases, create the values that you need to complete the requirements. For values that have been supplied to you, they must be entered exactly as they appear in order for you to get full credit for your configuration.
You will practice and be assessed on the following skills:
- Configuration of initial IOS device settings
- Design and calculation of IPv4 addressing
- Configuration of IOS device interfaces including IPv4 and IPv6 addressing when appropriate
- Addressing of network hosts with IPv4 and IPv6 addresses
- Enhancing device security, including configuration of the secure transport protocol for remote device configuration
- Configuration of a switch management interface
Requirements by device:
Town Hall router:
- Configuration of initial router settings
- Interface configuration and IPv4 and IPv6 addressing
- Device security enhancement or device hardening
- Secure transport for remote configuration connections as covered in the labs
- Backup of the configuration file to a TFTP server
Administration Switch:
- Enabling basic remote management by Telnet
PC and Server hosts:
- IPv4 full addressing
- IPv6 addressing
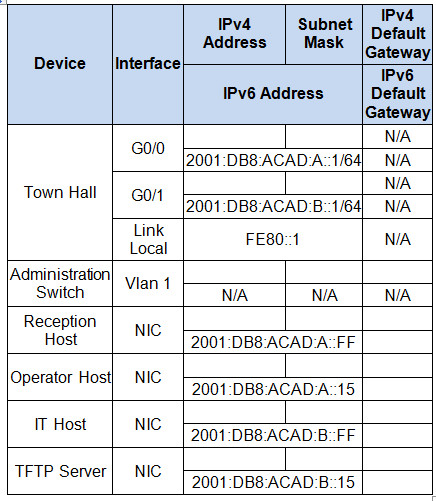
Addressing Table
Instructions
Step 1: Determine the IP Addressing Scheme.
Design an IPv4 addressing scheme and complete the Addressing Table based on the following requirements. Use the table to help you organize your work.
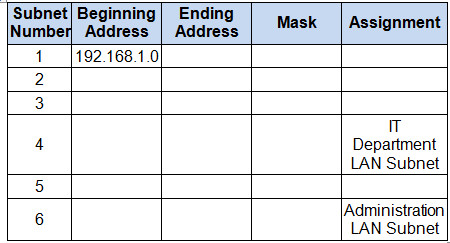
a.Subnet the 192.168.1.0/24 network to provide 30 host addresses per subnet while wasting the fewest addresses.
b. Assign the fourth subnet to the IT Department LAN.
c. Assign the last network host address (the highest) in this subnet to the G0/0 interface on Town Hall.
d. Starting with the fifth subnet, subnet the network again so that the new subnets will provide 14 host addresses per subnet while wasting the fewest addresses.
e. Assign the second of these new 14-host subnets to the Administration LAN.
f. Assign the last network host address (the highest) in the Administration LAN subnet to the G0/1 interface of the Town Hall router.
g. Assign the second to the last address (the second highest) in this subnet to the VLAN 1 interface of the Administration Switch.
h. Configure addresses on the hosts using any of the remaining addresses in their respective subnets.
Step 2: Configure the Town Hall Router.
Configure the Town Hall router with all initial configurations that you have learned in the course so far:
- Configure the router hostname: Middle
- Protect device configurations from unauthorized access with the encrypted privileged exec password.
- Secure all access lines into the router using methods covered in the course and labs.
- Require newly-entered passwords must have a minimum length of 10 characters.
- Prevent all passwords from being viewed in clear text in device configuration files.
- Configure the router to only accept in-band management connections over the protocol that is more secure than Telnet, as was done in the labs. Use the value 1024 for encryption key strength.
- Configure local user authentication for in-band management connections. Create a user with the name netadmin and a secret password of Cisco_CCNA5 Give the user the highest administrative privileges. Your answer must match these values exactly.
b. Configure the two Gigabit Ethernet interfaces using the IPv4 addressing values you calculated and the IPv6 values provided in the addressing table.
- Reconfigure the link local addresses to the value shown in the table.
- Document the interfaces in the configuration file.
Step 3: Configure the Administration Switch.
Configure Administration Switch for remote management over Telnet.
Step 4: Configure and Verify Host Addressing.
- Use the IPv4 addressing from Step 1 and the IPv6 addressing values provided in the addressing table to configure all host PCs with the correct addressing.
- Use the router interface link-local address as the IPv6 default gateways on the hosts.
- Complete the configuration of the TFTP server using the IPv4 addressing values from Step 1 and the values in the addressing table.
[/tab]
CCNA Routing and Switching Routing and Switching Essentials
Routing and Switching Essentials Chapter 2 SIC Practice Skills Assessment – Packet Tracer
[tab title=”TYPE C”]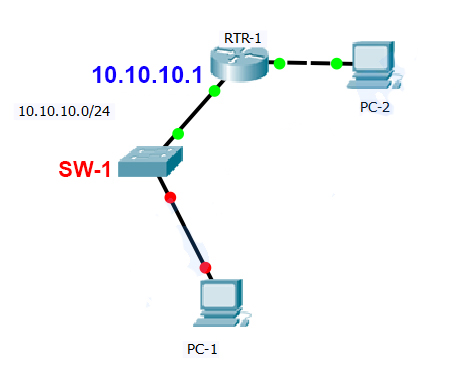
A few things to keep in mind while completing this activity:
1. Do not use the browser Back button or close or reload any exam windows during the exam.
2. Do not close Packet Tracer when you are done. It will close automatically.
3. Click the Submit Assessment button in the browser window to submit your work.
Introduction
In this practice skills assessment, you will configure SW-1 with an initial configuration, SSH, and port security.
You are only required to configure SW-1 in this assessment.
All IOS device configurations should be completed from a direct terminal connection to the device console.
It is possible that information that is required to complete the configurations has not been given to you. In that case, create the values that you need to complete the requirements. These values may include certain IP addresses, passwords, interface descriptions, banner text, and other values. You should always use the values that are provided in the instructions in any case.
You will practice and be assessed on the following skills:
• Configuration of initial device settings
• Configuration of switch ports
• Configuration and addressing of the switch management interface (SVI)
• Configuration of the SSH protocol for remote switch access.
• Configuration of port security features.
Addressing Table
| Device | Interface | IP Address | Subnet Mask |
|---|---|---|---|
| SW-1 | VLAN 1 | 10.10.10.100 | 255.255.255.0 |
| PC-1 | NIC | 10.10.10.10 | 255.255.255.0 |
| PC-2 | NIC | 192.168.2.1 | 255.255.255.0 |
Scenario
The network administrator has asked you to configure a new switch. In this activity, you will use a list of requirements to configure the new switch with initial settings, SSH, and port security.
1. Configure SW-1 with the following initial settings:
• Configure the switch with the hostname value from the addressing table. Your configured value must match the value in the addressing table exactly.
• Configure a banner message-of-the-day.
• Enable access to the device console with the password cisco.
• Create an MD5 encrypted enable password of class.
• Encrypt all plain text passwords.
• Management SVI addressing
• Address the default management interface.
• The switch should be reachable over the network from PC-1 and PC-2.
2. Configure SSH to secure remote access with the following settings:
• A domain name of cisco.com
• RSA key-pair parameters to support SSH version 2. Use a modulus of 1024.
• Set SSH to version 2.
• Create a user admin with password ccna.
• Configure vty lines to only accept SSH connections.
• Require the user created above to supply the user name and password in order to login over SSH.
3. Configure the port security feature to restrict network access:
• Disable all unused ports.
• Set all Fast Ethernet ports to access ports.
• Enable port security to allow only two hosts per port.
• Enable the MAC addresses of hosts that have connected to the switch ports to be recorded in the configuration file.
• Ensure that port violations disable ports.
Instruction
Can apply to all type (Type A, Type B, Type C, …). Please check HOSTNAME and IP on instruction
Switch(config)#hostname SW-1[CHECK HOSTNAME ON INSTRUCTIONS] SW-1(config)#banner motd $This is Switch$ SW-1(config)#line console 0 SW-1(config-line)#password cisco SW-1(config-line)#login SW-1(config-line)#exit SW-1(config)#enable secret class SW-1(config)#service password-encryption SW-1(config)#interface vlan1 SW-1(config-if)#ip address 10.10.10.100[check IP on Addressing Table] 255.255.255.0 SW-1(config-if)#ip default-gateway 10.10.10.1[check IP address of router port to Switch] SW-1(config-if)#no shutdown SW-1(config-if)#exit SW-1(config)#ip domain-name cisco.com SW-1(config)#crypto key generate rsa The name for the keys will be: SW-1.cisco.com Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes. How many bits in the modulus [512]: 1024 % Generating 1024 bit RSA keys, keys will be non-exportable…[OK] SW-1(config)#ip ssh version 2 SW-1(config)#username admin secret ccna SW-1(config)#line vty 0 15 SW-1(config-line)#login local SW-1(config-line)#transport input ssh SW-1(config-line)#exit SW-1(config-if)#int fa0/1 SW-1(config-if)#no shutdown SW-1(config)#int range fa0/2-24 SW-1(config-if-range)#shutdown SW-1(config-if-range)#int g0/2 SW-1(config-if)#shutdown SW-1(config)#int range fa0/1-24 SW-1(config-if-range)#switchport mode access SW-1(config-if-range)#switchport port-security SW-1(config-if-range)#switchport port-security mac-address sticky SW-1(config-if-range)#switchport port-security maximum 2 SW-1(config-if-range)# switchport port-security violation shutdown SW-1(config)#int range g0/1-2 SW-1(config-if-range)#switchport mode access SW-1(config-if-range)#switchport port-security SW-1(config-if-range)#switchport port-security mac-address sticky SW-1(config-if-range)#switchport port-security maximum 2 SW-1(config-if-range)# switchport port-security violation shutdown
