CCNA 4 Practice Final Exam Answers
-
Which WAN technology is capable of transferring voice and video traffic by utilizing a fixed payload of 48 bytes for every frame?
Ethernet WAN
ISDN
ATM*
Frame Relay -
Which type of long distance telecommunication technology provides point-to-point connections and cellular access?
mobile broadband
WiMax*
satellite
municipal Wi-Fi -
A small law firm wants to connect to the Internet at relatively high speed but with low cost. In addition, the firm prefers that the connection be through a dedicated link to the service provider. Which connection type should be selected?
cable
ISDN
leased line
DSL* -
Refer to the exhibit. What type of Layer 2 encapsulation will be used for connection D on the basis of this configuration on a newly installed router:
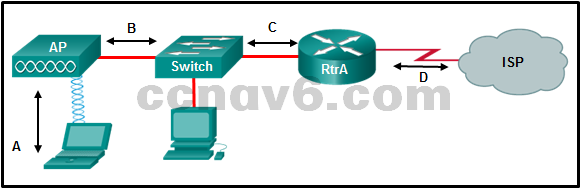
RtrA(config)# interface serial0/0/0
RtrA(config-if)# ip address 128.107.0.2 255.255.255.252
RtrA(config-if)# no shutdownFrame Relay
HDLC*
PPP
Ethernet -
Which two components of a WAN would more likely be used by an ISP? (Choose two.)
demarcation point
toll network*
CO*
CPE
DTE -
What are two advantages of packet switching over circuit switching? (Choose two.)
There are fewer delays in the data communications processes.
Multiple pairs of nodes can communicate over the same network channel.*
A dedicated secure circuit is established between each pair of communicating nodes.
A connection through the service provider network is established quickly before communications start.
The communication costs are lower.* -
What are two common types of circuit-switched WAN technologies? (Choose two.)
ISDN*
MPLS
ATM
PSTN*
Frame Relay -
Under which two categories of WAN connections does Frame Relay fit? (Choose two.)
packet-switched*
public infrastructure
dedicated
private infrastructure*
Internet -
Which two protocols in combination should be used to establish a link with secure authentication between a Cisco and a non-Cisco router? (Choose two.)
CHAP*
PAP
HDLC
PPP*
SLIP -
Which statement is true about NCP?
NCP tests the link to ensure that the link quality is sufficient.
Each network protocol has a corresponding NCP.*
Link termination is the responsibility of NCP.
NCP establishes the initial link between PPP devices. -
Refer to the exhibit. Which three steps are required to configure Multilink PPP on the HQ router? (Choose three.)
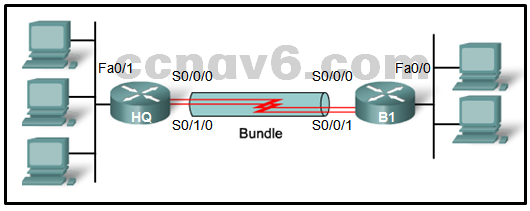
Assign the serial interfaces to the multilink bundle.*
Create and configure the multilink interface.*
Enable PPP encapsulation on the multilink interface.
Enable PPP encapsulation on the serial interfaces.*
Assign the Fast Ethernet interface to the multilink bundle.
Bind the multilink bundle to the Fast Ethernet interface. -
A network engineer is troubleshooting the failure of CHAP authentication over a PPP WAN link between two routers. When CHAP authentication is not included as part of the interface configuration on both routers, communication across the link is successful. What could be causing CHAP to fail?
The username configured on each router matches the hostname of the other router.
The hostname configured on each router is different.
The clock rate has not been configured on the DCE serial interface.
The secret password configured on each router is different.* -
Which statement describes the difference between CHAP and PAP in PPP authentication?
PAP uses a two-way handshake method and CHAP uses a three-way handshake method.*
PAP sends the password encrypted and CHAP does not send the password at all.
PAP and CHAP provide equivalent protection against replay attacks.
PAP sends the password once and CHAP sends the password repeatedly until acknowledgment of authentication is received. -
A technician at a remote location is troubleshooting a router and has emailed partial debug command output to a network engineer at the central office. The message that is received by the engineer only contains a number of LCP messages that relate to a serial interface. Which WAN protocol is being used on the link?
PPP*
VPN
HDLC
Frame Relay -
Which DSL technology provides higher downstream bandwidth to the user than upstream bandwidth?
CDMA
SDSL
TDMA
ADSL* -
Which communication protocol allows the creation of a tunnel through the DSL connection between the customer router and the ISP router to send PPP frames?
POTS
CHAP
ADSL
PPPoE* -
Which group of APIs are used by an SDN controller to communicate with various applications?
northbound APIs*
westbound APIs
southbound APIs
eastbound APIs -
Which two technologies are core components of Cisco ACI architecture? (Choose two.)
OpenFlow enabled switches
Application Policy Infrastructure Controller*
Transparent Interconnection of Lots of Links
Application Network Profile*
Interface to the Routing System -
Two corporations have just completed a merger. The network engineer has been asked to connect the two corporate networks without the expense of leased lines. Which solution would be the most cost effective method of providing a proper and secure connection between the two corporate networks?
site-to-site VPN*
Cisco Secure Mobility Clientless SSL VPN
Cisco AnyConnect Secure Mobility Client with SSL
remote access VPN using IPsec
Frame Relay -
When GRE is configured on a router, what do the tunnel source and tunnel destination addresses on the tunnel interface refer to?
the IP addresses of tunnel interfaces on intermediate routers between the connected routers
the IP addresses of the two LANs that are being connected together by the VPN
the IP addresses at each end of the WAN link between the routers*
the IP address of host on the LAN that is being extended virtually -
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
What problem is preventing the hosts from communicating across the VPN tunnel?The tunnel IP addresses are incorrect.*
The EIGRP configuration is incorrect.
The tunnel destinations addresses are incorrect.
The tunnel source interfaces are incorrect. -
Which routing protocol is used to exchange routing information between autonomous systems on the Internet?
OSPF
EIGRP
IS-IS
BGP* -
The graphic shows four autonomous systems (AS). AS 65002 is connected to AS 65003 and to AS 65004. AS 65003 is connected only to AS 65002. AS 65004 is connected to AS 65002 and AS 65005. AS 65005 is connected to AS 65003 and to the Internet.Refer to the exhibit. For which autonomous system would running BGP not be appropriate?
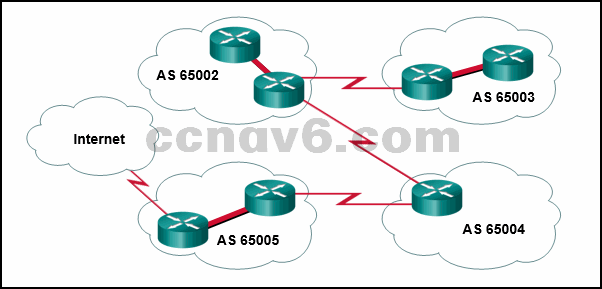
65004
65005
65002
65003* -
What two functions describe uses of an access control list? (Choose two.)
ACLs can permit or deny traffic based upon the MAC address originating on the router.
ACLs provide a basic level of security for network access.*
ACLs can control which areas a host can access on a network.*
ACLs assist the router in determining the best path to a destination.
Standard ACLs can restrict access to specific applications and ports. -
A network administrator is explaining to a junior colleague the use of the lt and gt keywords when filtering packets using an extended ACL. Where would the lt or gt keywords be used?
in an IPv6 extended ACL that stops packets going to one specific destination VLAN
in an IPv6 named ACL that permits FTP traffic from one particular LAN getting to another LAN
in an IPv4 extended ACL that allows packets from a range of TCP ports destined for a specific network device*
in an IPv4 named standard ACL that has specific UDP protocols that are allowed to be used on a specific server -
Refer to the exhibit. A router has an existing ACL that permits all traffic from the 172.16.0.0 network. The administrator attempts to add a new ACE to the ACL that denies packets from host 172.16.0.1 and receives the error message that is shown in the exhibit. What action can the administrator take to block packets from host 172.16.0.1 while still permitting all other traffic from the 172.16.0.0 network?
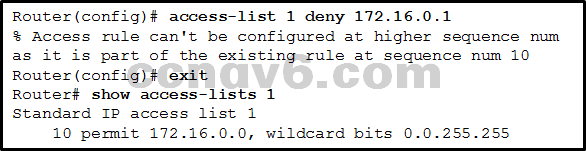
Add a deny any any ACE to access-list 1.
Manually add the new deny ACE with a sequence number of 15.
Create a second access list denying the host and apply it to the same interface.
Manually add the new deny ACE with a sequence number of 5.* -
Which three implicit access control entries are automatically added to the end of an IPv6 ACL? (Choose three.)
deny icmp any any
permit ipv6 any any
deny ipv6 any any*
permit icmp any any nd-na*
permit icmp any any nd-ns*
deny ip any any -
Which statement describes a difference between the operation of inbound and outbound ACLs?
Inbound ACLs are processed before the packets are routed while outbound ACLs are processed after the routing is completed.*
On a network interface, more than one inbound ACL can be configured but only one outbound ACL can be configured.
In contrast to outbound ALCs, inbound ACLs can be used to filter packets with multiple criteria.
Inbound ACLs can be used in both routers and switches but outbound ACLs can be used only on routers. -
What is the result of a DHCP starvation attack?
Clients receive IP address assignments from a rogue DHCP server.
The attacker provides incorrect DNS and default gateway information to clients.
The IP addresses assigned to legitimate clients are hijacked.
Legitimate clients are unable to lease IP addresses.* -
What is a recommended best practice when dealing with the native VLAN?
Turn off DTP.
Use port security.
Assign it to an unused VLAN.*
Assign the same VLAN number as the management VLAN. -
Which management protocol can be used securely with Cisco devices to retrieve or write to variables in a MIB?
SNMP version 1
SNMP version 2
SNMP version 2c
SNMP version 3*
SNMP version 3 is considered the secure version of SNMP. -
What are two benefits of using SNMP traps? (Choose two.)
They limit access for management systems only.
They eliminate the need for some periodic polling requests.*
They can provide statistics on TCP/IP packets that flow through Cisco devices.
They can passively listen for exported NetFlow datagrams.
They reduce the load on network and agent resources.* -
What is an advantage of SNMPv3 over SNMPv1 or SNMPv2?
mobility
support of other network monitoring protocols
faster response times
security* -
What network monitoring tool copies traffic moving through one switch port, and sends the copied traffic to another switch port for analysis?
SPAN*
SNMP
syslog
802.1X -
RSPAN depends on which type of VLAN?
RSPAN VLAN*
default VLAN
native VLAN
black hole VLAN
management VLAN
private VLAN -
Why is QoS an important issue in a converged network that combines voice, video, and data communications?
Voice and video communications are more sensitive to latency.*
Legacy equipment is unable to transmit voice and video without QoS.
Data communications must be given the first priority.
Data communications are sensitive to jitter. -
What are two characteristics of voice traffic? (Choose two.)
It is insensitive to packet loss.
It consumes few network resources.*
It can tolerate latency up to 400 ms.
It is delay sensitive.*
It is bursty. -
True or False.
DiffServ is a QoS strategy that enforces end-to-end guarantees.
true
false* -
What QoS step must occur before packets can be marked?
policing
shaping
queuing
classifying* -
Refer to the exhibit. A network administrator has deployed QoS and has configured the network to mark traffic on the VoIP phones as well as the Layer 2 and Layer 3 switches. Where should initial marking occur to establish the trust boundary?
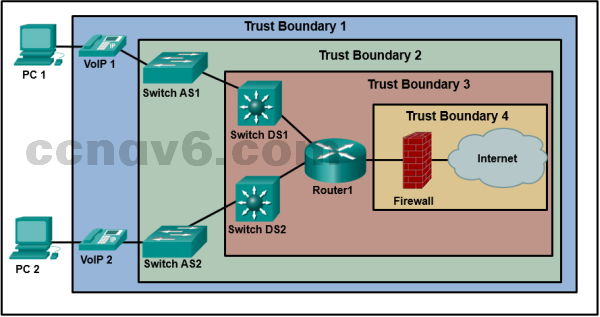
Trust Boundary 4
Trust Boundary 3
Trust Boundary 1*
Trust Boundary 2 -
Which IoT pillar provides the infrastructure for application mobility?
the management and automation pillar
the application enablement platform pillar*
the Fog computing pillar
the network connectivity pillar -
What are three abstraction layers of a computer system? (Choose three.)
firmware*
network
hardware*
data
services*
security -
Users are reporting longer delays in authentication and in accessing network resources during certain time periods of the week. What kind of information should network engineers check to find out if this situation is part of a normal network behavior?
network configuration files
debug output and packet captures
syslog records and messages
the network performance baseline* -
A user is unable to connect to the Internet. The network administrator decides to use the top-down troubleshooting approach. Which action should the administrator perform first?
Run the tracert command to identify the faulty device.
Check the patch cable connection from the PC to the wall.
Run the ipconfig command to verify the IP address, subnet mask, and gateway on the PC.
Enter an IP address in the address bar of the web browser to determine if DNS has failed.* -
How do network administrators use IP SLAs to monitor a network and to detect a network failure early?
by simulating network data and IP services to collect network performance data in real time*
by using network protocol analyzers to evaluate errors
by taking a snap shot of network performance and comparing with an established baseline
by measuring the CPU and memory usage on routers and switches -
What are two examples of network problems that are found at the data link layer? (Choose two.)
encapsulation errors*
incorrect interface clock rates
late collisions and jabber
framing errors*
electromagnetic interference -
The output of the show ip interface brief command indicates that Serial0/0/0 is up but the line protocol is down. What are two possible causes for the line protocol being in the down state? (Choose two.)
The encapsulation on the Serial0/0/0 interface is incorrect.*
The clock rate is not set on the DTE.
A network is missing from the routing protocol configuration.
Keepalives are not being sent by the remote device.*
An incorrect default gateway is set on the router. -
Refer to the exhibit. A small office uses an ISR to provide connectivity for both wired and wireless computers. One day, a sales person who is using a laptop cannot connect to Server1 through the wireless network. A network technician attempts to determine if the problem is on the wireless or the wired network. The technician pings successfully from the wireless laptop to the default gateway IP address on the ISR. What should be the next troubleshooting step?
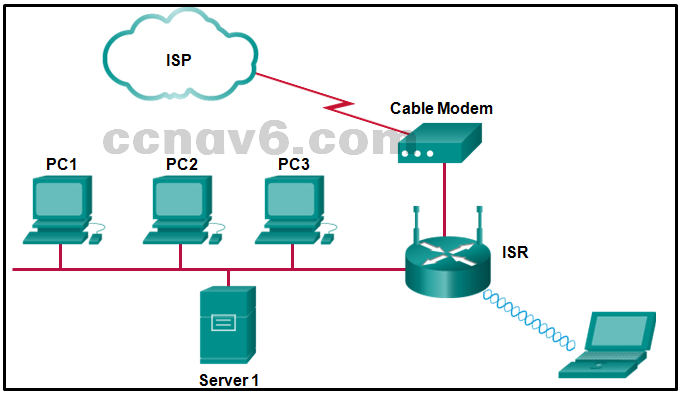
Ping from Server1 to its gateway IP address.*
Ping from Server1 to PC1.
Ping from the laptop to PC1.
Ping from the laptop to the Ethernet port on the cable modem. -
Refer to the exhibit. A ping from R1 to 10.1.1.2 is successful, but a ping from R1 to any address in the 192.168.2.0 network fails. What is the cause of this problem?
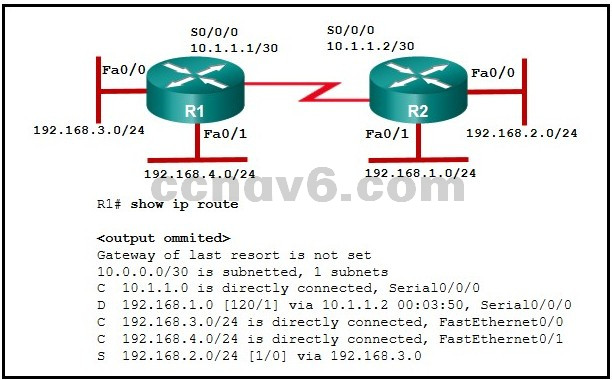
A default route is not configured on R1.
The static route for 192.168.2.0 is incorrectly configured.*
The serial interface between the two routers is down.
There is no gateway of last resort at R1. -
Which feature is unique to IPv6 ACLs when compared to those of IPv4 ACLs?
the use of named ACL statements
an implicit permit of neighbor discovery packets*
the use of wildcard masks
an implicit deny any any statement -
Question as presented:
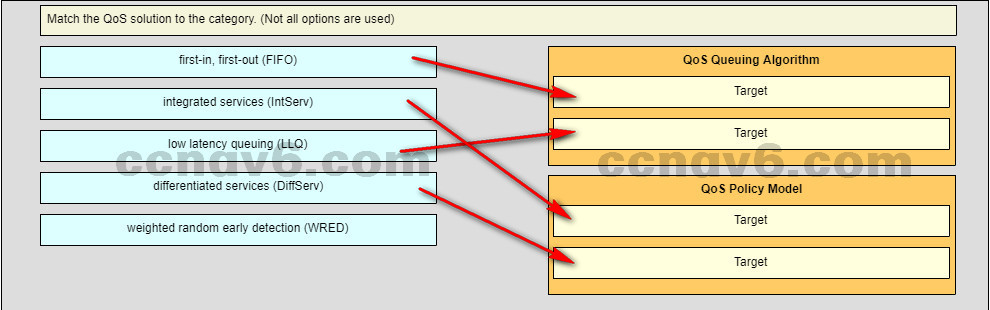
-
Question as presented:
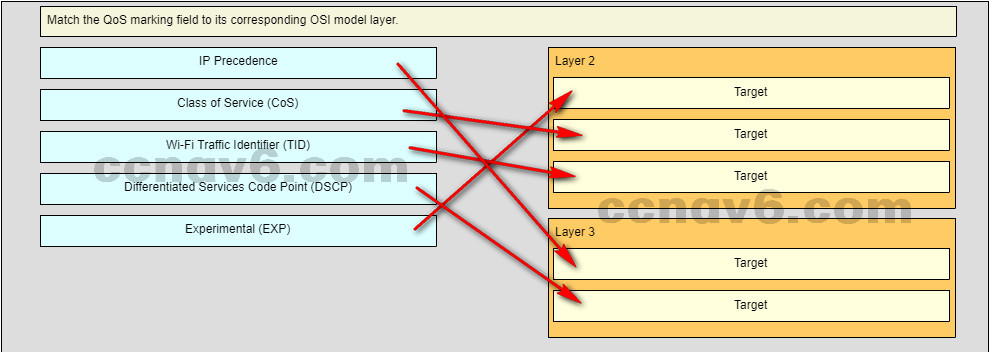
-
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question.
A user reports that PC0 cannot visit the web server www.server.com. Troubleshoot the network configuration to identify the problem.
What are three configuration issues that are causing the problem? (Choose three.)SW1 has a port configuration issue.*
There is an encapsulation issue for the link between Branch and SW1.
One of the interfaces on Branch is not activated.*
Routing on HQ is not configured correctly.*
The subinterface g0/0.1 on Branch is configured incorrectly for VLAN 10.
VLAN 20 is not created correctly on SW1.
