10.7.6 Packet Tracer – Use a TFTP Server to Upgrade a Cisco IOS Image (Instructor Version)
Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only.
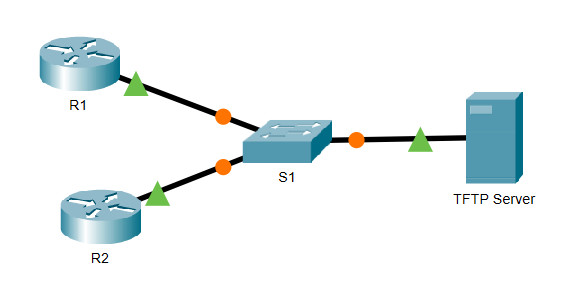
Addressing Table
| Device | Interface | IP Address | Subnet Mask | Default Gateway |
|---|---|---|---|---|
| R1 | G0/0/0 | 192.168.2.1 | 255.255.255.0 | N/A |
| R2 | G0/0 | 192.168.2.2 | 255.255.255.0 | N/A |
| S1 | VLAN 1 | 192.168.2.3 | 255.255.255.0 | 192.168.2.1 |
| TFTP Server | NIC | 192.168.2.254 | 255.255.255.0 | 192.168.2.1 |
Objectives
- Part 1: Upgrade an IOS Image on a Cisco Device
- Part 2: Backup an IOS Image on a TFTP Server
Scenario
A TFTP server can help manage the storage of IOS images and revisions to IOS images. For any network, it is good practice to keep a backup copy of the Cisco IOS Software image in case the system image in the router becomes corrupted or accidentally erased. A TFTP server can also be used to store new upgrades to the IOS and then deployed throughout the network where it is needed. In this activity, you will upgrade the IOS images on Cisco devices by using a TFTP server. You will also backup an IOS image with the use of a TFTP server.
Instructions
Part 1: Upgrade an IOS Image on a Cisco Device
Step 1: Upgrade an IOS image on a router.
a. Access the TFTP server and enable the TFTP service.
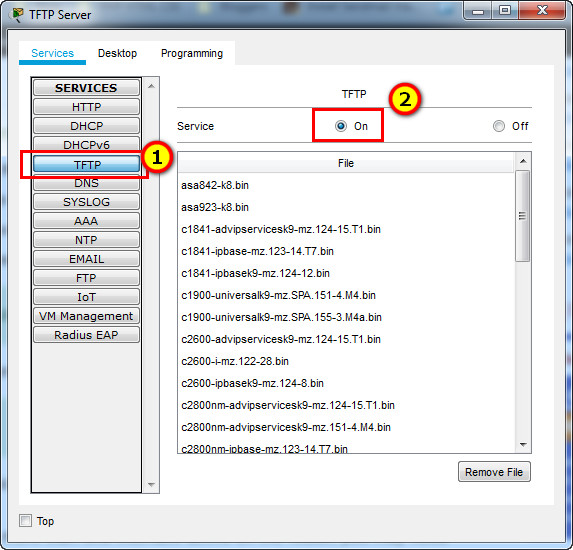
b. Note the IOS image files that are available on the TFTP server.
Which IOS images stored on the server are compatible with a 1941 router?
c. From R2, issue the show flash: command and record the available flash memory.
R2#show flash:
System flash directory:
File Length Name/status
3 33591768 c1900-universalk9-mz.SPA.151-4.M4.bin
2 28282 sigdef-category.xml
1 227537 sigdef-default.xml
[33847587 bytes used, 221896413 available, 255744000 total]
249856K bytes of processor board System flash (Read/Write)
d. Copy the CISCO1941/K9 IOS version 15.5 image for the 1941 router from the TFTP Server to R2.
Note: In an actual network, if there is more than one interface active on the router, you may need to enter the ip tftp source interface command to specify which interface should be used to contact the TFTP server. This command is not supported in PT 7.2 and older versions and is not necessary to complete this activity.
R2# copy tftp: flash: Address or name of remote host []? 192.168.2.254 Source filename []? c1900-universalk9-mz.SPA.155-3.M4a.bin Destination filename [c1900-universalk9-mz.SPA.155-3.M4a.bin]? Accessing tftp://192.168.2.254/c1900-universalk9-mz.SPA.155-3.M4a.bin.... Loading c1900-universalk9-mz.SPA.155-3.M4a.bin from 192.168.2.254: !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! [OK - 33591768 bytes] 33591768 bytes copied in 4.099 secs (860453 bytes/sec)
e. Verify that the IOS image has been copied to flash.
How many IOS images are located in flash?
R2#show flash:
System flash directory:
File Length Name/status
3 33591768 c1900-universalk9-mz.SPA.151-4.M4.bin
5 33591768 c1900-universalk9-mz.SPA.155-3.M4a.bin
2 28282 sigdef-category.xml
1 227537 sigdef-default.xml
[67439355 bytes used, 188304645 available, 255744000 total]
249856K bytes of processor board System flash (Read/Write)
f. Use the boot system command to load the version 15.5 IPBase image on the next reload.
R2(config)# boot system flash c1900-universalk9-mz.SPA.155-3.M4a.bin
g. Save the configuration and reload R2.
R2#copy running-config startup-config
R2#reload
h. Use the show version command to verify the upgraded IOS image is loaded after R2 reboots.
R2# show version Cisco IOS Software, C1900 Software (C1900-UNIVERSALK9-M), Version 15.5(3)M4a, RELEASE SOFTWARE (fc1) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2016 by Cisco Systems, Inc. Compiled Thu 06-Oct-16 13:56 by mnguyen ROM: System Bootstrap, Version 15.0(1r)M9, RELEASE SOFTWARE (fc1) R2 uptime is 21 seconds System returned to ROM by power-on System image file is "flash0:c1900-universalk9-mz.SPA.155-3.M4a.bin" ---- output omitted -----
Step 2: Upgrade an IOS image on a switch.
a. Access the TFTP server and copy the c2960-lanbasek9-mz.150-2.SE4.bin image to S1.
S1#copy tftp: flash:
Address or name of remote host []? 192.168.2.254
Source filename []? c2960-lanbasek9-mz.150-2.SE4.bin
Destination filename [c2960-lanbasek9-mz.150-2.SE4.bin]?
Accessing tftp://192.168.2.254/c2960-lanbasek9-mz.150-2.SE4.bin....
Loading c2960-lanbasek9-mz.150-2.SE4.bin from 192.168.2.254: !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
[OK - 4670455 bytes]
4670455 bytes copied in 3.08 secs (121911 bytes/sec)
S1#
b. Use the boot system command to configure the switch to load the new IOS image on boot.
S1(config)#boot system flash0:c2960-lanbasek9-mz.150-2.SE4.bin
c. Reload S1 and verify the new image has been loaded into memory.
S1#copy running-config startup-config
S1#reload
d. Close the TFTP configuration window if it is still open.
Part 2: Backup an IOS Image to a TFTP Server
a. On R1, display the contents of flash and record the IOS image.
R1#show flash:
System flash directory:
File Length Name/status
3 486899872isr4300-universalk9.03.16.05.S.155-3.S5-ext.SPA.bin
2 28282 sigdef-category.xml
1 227537 sigdef-default.xml
[487155691 bytes used, 2761893909 available, 3249049600 total]
3.17338e+06K bytes of processor board System flash (Read/Write)
b. Use the copy command to back up the IOS image in flash memory on R1 to a TFTP server. Note: The isr4300 image is considerably larger than the c1900 image. It will take longer to transmit it to the TFTP server.
R1# copy flash: tftp: Source filename []? isr4300-universalk9.03.16.05.S.155-3.S5-ext.SPA.bin Address or name of remote host []? 192.168.2.254 Destination filename [isr4300-universalk9.03.16.05.S.155-3.S5-ext.SPA.bin]? Writing isr4300-universalk9.03.16.05.S.155-3.S5-ext.SPA.bin....!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! --- output omitted ---- !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! [OK - 486899872 bytes] 486899872 bytes copied in 18.815 secs (83367 bytes/sec)
c. Access the TFTP server and verify that the IOS image has been copied to the TFTP server.
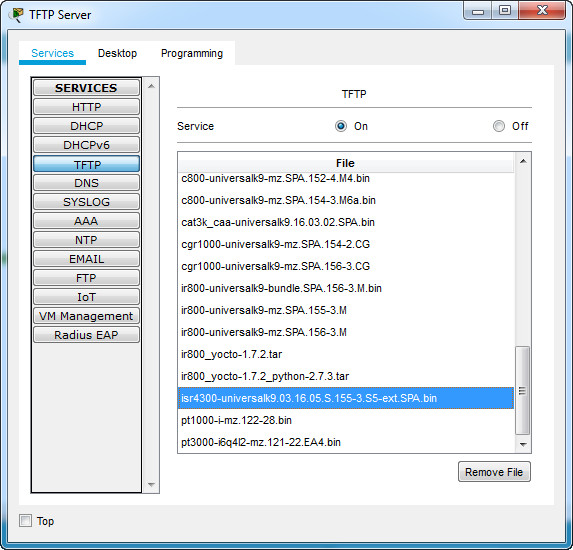
Note: You may have to start and stop the TFTP service on the server so the file appears in the file listing.
Download Packet Tracer Completed File
[sociallocker id=”54558″]
[wpdm_package id=’55951′]
[wpdm_package id=’55953′]
[/sociallocker]
[alert-note][one_half]
Previous Lab
10.6.10 Packet Tracer – Back Up Configuration Files
[/one_half][one_half_last]
Next Lab
10.8.1 Packet Tracer – Configure CDP, LLDP, and NTP
[/one_half_last][/alert-note]
